How Palo Alto Networks helps you prepare for GDPR
GDPR: a short summary
The General Data Protection Regulation (GDPR) is the EU’s upcoming new personal data protection law. On the 25th of May 2018, the GDPR becomes enforceable and will replace the Data Protection Directive that was introduced in 1995. This will significantly change the rules surrounding the protection of personal data of EU residents.
The GDPR is much stricter and has a greater scope of coverage than the Data Protection Directive. The GDPR now also includes companies outside the EU and introduces new data breach notification requirements and administrative fines. The vast majority of GDPR requirements are centered around data management and data security. In essence, the law requires and enforces the security of data processing. This includes access, rectification and erasure of personal data held on individuals, and the right of data portability.
SecureLink elaborated extensively on the GDPR subject in the following other blog posts:
2 GDPR principles you can’t forget
GDPR is about privacy. When talking about security versus privacy, two principles of ‘Privacy by Design’ are very important:
- You can have security without privacy, but you can’t have privacy without security.
- Security and transparency are privacy’s key driver of success.
Technologies like Palo Alto Networks and F5 Networks play a key role in the support of these two principles. This blog post will elaborate on specific features of these two technologies in your journey towards GDPR readiness.
How Palo Alto Networks’ Next-Generation Security platform contributes to GDPR.
Palo Alto Networks’ Next-Generation Firewalls are a basic security technology when it comes to the protection of your perimeter and internal network. Next-Generation Firewalls focus on Applications, Users and Content. These focus points are very useful for data protection as well. SecureLink’s primary focus with Palo Alto Networks is on the outgoing network connections and on the protection of the endpoints as these are very important vectors for data exfiltration or voluntary/involuntary data leakage.
The following Palo Alto Networks features are very interesting to look at in the context of GDPR:
Data Breach Prevention:
A crucial GDPR-related aspect is data breach prevention. Data breaches can be the result of hacking but data leakage can also happen accidentally.
The Palo Alto Networks platform approach employs a series of prevention techniques relevant to data security. Combined, these techniques make a large contribution towards GDPR:
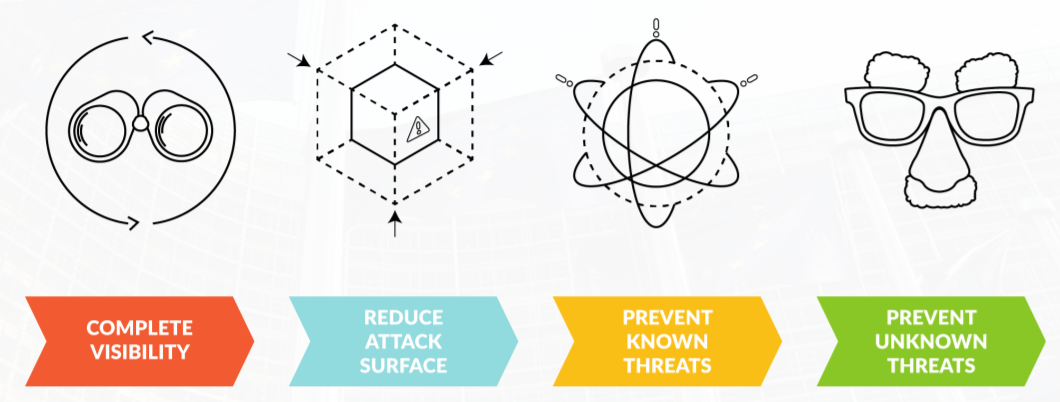
- Visibility: The Palo Alto Networks platform approach offers visibility into all traffic across the network, endpoint and the cloud. This visibility enables a dynamic security policy, since you can only protect against what you see.
- Reduction of attack surface: The rising usage of new technologies like Cloud services or IoT also dramatically expand the potential attack surface for cyber criminals. Palo Alto Networks enforces a positive security model by only enabling the allowed applications for the right users and denying everything else.
- Known threat prevention: Known trojans, exploits or malware can often be the cause of data breaches. On the endpoint side, Palo Alto Networks uses a combination of the threat intelligence gathered from its global community of customers and a unique multi-method prevention approach to block known malware or exploits before the endpoint can be compromised. On the perimeter side, the attack surface is reduced through the granular management of all types of applications.
- Unknown threat prevention: More sophisticated or targeted attacks often employ malware or exploits of an unknown nature. When such a novel malware or exploit is seen by Palo Alto Networks’ Wildfire, it is automatically processed and within 5 minutes a new control is distributed to your Palo Alto Firewalls and/or Traps protected endpoints.
Data Leakage or Exfiltration Prevention:
The Palo Alto Networks’ security platform can prevent data leakage and exfiltration in several ways to maintain the appropriate security controls for GDPR. Data leakage can happen for many reasons, ranging from attackers trying to gain access to the perimeter to accidental personal data leakage due to untrained or unaware employees.
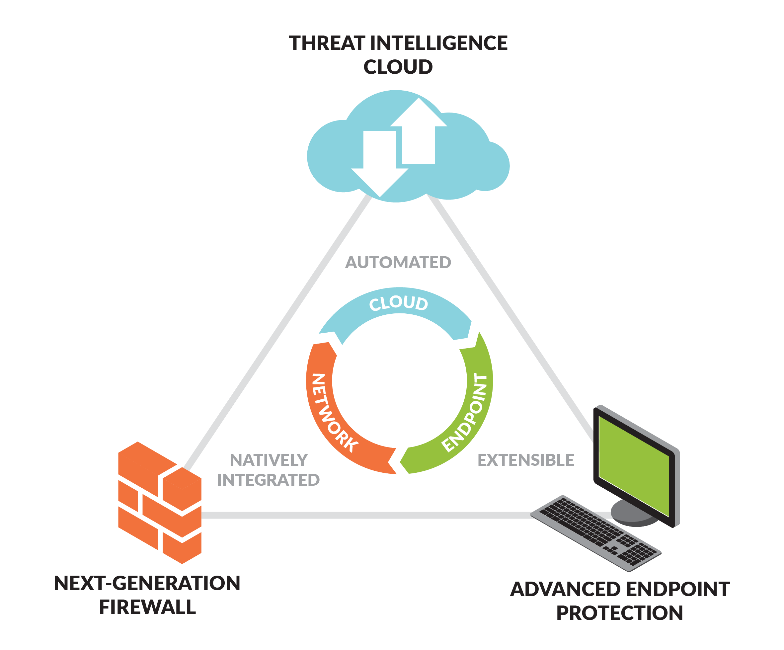
Image Source: www.westconcomstor.com/nz/en/vendors/wc-vendors/Palo-Alto.html
- Network security: The Palo Alto Networks Next Generation Firewall is the main point of inspection for all traffic passing on the internal network. The firewall has built-in data filtering profiles and advanced policies to inspect, control and limit unauthorized transfers of sensitive data, such as credit card numbers. Palo Alto Networks’ Next Generation Firewalls can use document meta-data tags like ‘confidential’ or ‘sensitive’, set by technologies like the Varonis Data Classification Framework, to stop accidental data-exfiltration.
- SaaS level security: The Palo Alto Aperture SaaS Security Service complements the firewall by using SaaS APIs to connect directly to SaaS applications. This approach makes it possible to see what users are sharing or uploading on SaaS platforms like Dropbox, Office 365, Salesforce, etc…
Policies can then be applied to enforce responsible use. Furthermore, alerts can be generated when policy violations are detected. Aperture can also automatically remediate certain risks when it is configured to do so. - Endpoint security: Traps is the Palo Alto Networks’ advanced endpoint protection product. Traps employs a multi-method approach to prevent known and unknown threats that can compromise an endpoint.
- Credential theft security: Stolen credentials are one of the most common threat vectors for data breaches. The Palo Alto platform can stop credential leakage by preventing users from submitting credentials to unauthorised or unknown sites. Multi-factor authentication policies can also be enforced to govern access to critical applications with sensitive data.
Data Breach Notification:
If and when a data breach would happen, the GDPR requires that this event is reported to the authorities. This report must contain the data that was impacted and the measures that were taken to prevent it.
In order to comply with these notification requirements and to remediate the problem you must know who the impacted user was, what the threat was and what the risk level was. The SecureLink SecureDetect service offers an added value to actively monitor your Next-Generation Firewall and notifies your Security Incident Response teams on what the impact of the data breach is.
The Palo Alto Firewall can also be used to educate users by showing custom notification pages whenever an accidental data leak is prevented. This message could include a link to corporate data policies for example.
Palo Alto Networks’ Next-Generation Firewall GDPR configuration:
Palo Alto Networks’ Next-Generation Firewall is also a part of a Data Register & Data Protection Impact Assessment. Transparency is one of the key principles of Privacy by Design. Transparency is related to the principles of concerning openness and it is a prerequisite for accountability. Technical mechanisms for achieving or supporting transparency comprise logging and reporting.
The ENISA Privacy and Data Protection by Design – from policy to engineering documentation dedicates a section to “Communications anonymity and pseudonymity”.
“End-to-end encryption may be used to protect the content of communications, but leaves meta-data exposed to third-parties. Meta-data is information “about” the communication, such as who is talking to whom, the time and volume of messages, the duration of sessions or calls, the location and possible identity of the network end-points.
The exposure of meta-data may have a devastating impact on privacy. Uncovering the fact that a journalist is talking to someone within an organization or government department may compromise them as a journalistic source, even if the details of the message contents are not recoverable. Similarly, observing someone persistently browsing for information on some form of cancer may be indicative of a health concern or condition. Meta-data may also uncover lifestyle information that is not immediately obvious to communicating parties. For example persistent collocation of two mobile devices at out of office hours and on weekends is indicative of a close personal relationship. Meta-data analysis of mobile phone location logs, or WiFi / IP addresses, can uncover those relations even when the individuals concerned have not exchanged any messages.”
The same applies to Palo Alto Networks’ log information that correlates a user and a visited URL. For this purpose, the ENISA paper proposes a solution: “Third-party anonymity ensures meta-data is not revealed to third-parties, while both partners know, with high certainty, each other’s identity”. In this use case, the anonymity of your end-users should be protected against a system administrator as the third-party. While the Data Protection Officer (DPO) together with HR (four eyes principle) can reveal the identity of the end-users when it is required. Palo Alto Networks NGFWs have an out-of-the-box feature for this purpose: https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/firewall-administration/reference-web-interface-administrator-access/web-interface-access-privileges/define-user-privacy-settings-in-the-admin-role-profile.
Conclusion
GDPR is about privacy and privacy requires security. It is crystal clear that Palo Alto Networks’ Security Platform is important to provide prevention and detection capabilities to put security into practice. The built-in features, such as prevention of data breaches and data leakage/exfiltration offer a tremendous added value when it comes to GDPR. A Palo Alto Networks’ NGFW is one of the key perimeter security controls that help you with the notification of the data breaches.
