
22 November 2021

This article serves as a complement to the theoretical approach of the build and buy dilemma for CTI activities, adding concrete business elements to help managers decide whether or not to outsource this security function. The main feature which was incorporated in the analysis is the Return on Investment (ROI). This component accounts for the profitability of an investment. In this case, both the internal and external investments are considered. We argue that depending on the industry sector and the enterprise size, variations in the ROI are observed and make an option more profitable compared to the other. The chart below sums up our findings.
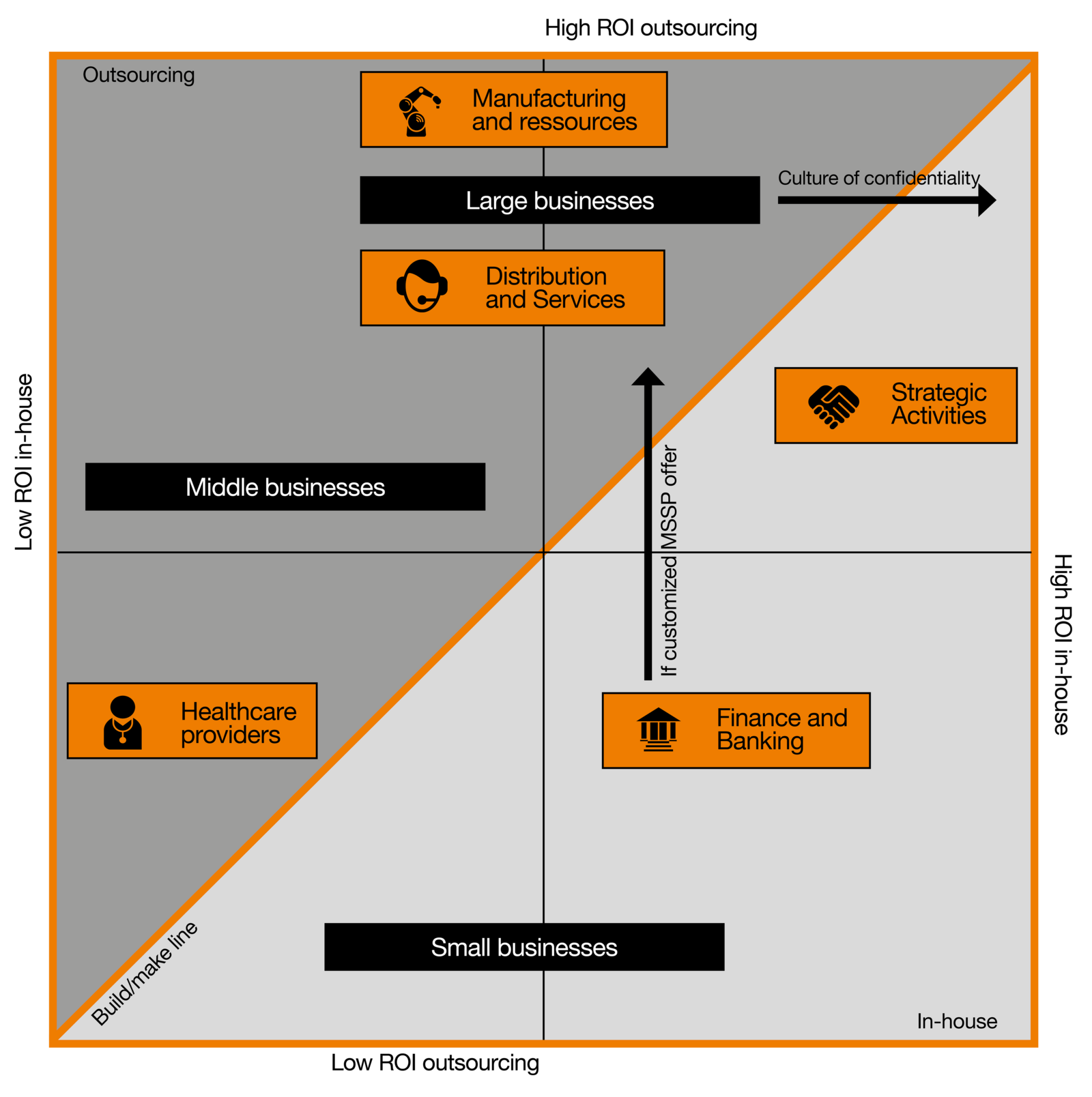
For each category, we are considering the most suitable option according to the organization’s needs. We are not assessing the ROI of full comprehensive CTI teams on small businesses as they cannot afford their building in the first place. Likewise, we are not estimating the business value of CTI feeds alone to a large organization as it would have little to no value. Bearing this in mind, we observe that the lowest ROI in-house comes from medium-sized businesses. It makes sense as they would have exhausted the value from raw OSINT CTI feeds and internal telemetry and would need more contextualized actionable intelligence. At the same time, building a CTI team would be too costly in relation to the moderate risk to the assets.
Small and large businesses have an average business value from building internal capacities. In the first case, their needs may be satisfied by a mix of internal telemetry and external CTI feeds which may bring some value that will be capped by the lack of context of these indicators (they may even become useless if the attacker is determined enough to bypass the defender’s efforts by using new, unidentified indicators). In the second case, the value of in-house CTI may be limited by the lack of scalability of IT servers, the turnover of human resources, or the long-term success of these technologies.
On the right side of the graph, we observe companies that have in common to own particularly sensitive assets (Finance and Banking). Their value increases the risk for the company to be targeted by malicious actors and thus increases the value of CTI for the organization, whether it is built in-house or outsourced. Likewise, strategic activities are represented at the far right of the graph as they are critically targeted by Advanced Persistent Threat (APT) actors. The Healthcare sector is an exception. Indeed, the value of medical records and the potential consequences of a business interruption is enormous and makes it high-value targets for malicious threat actors. Yet, unlike the financial sector, these organizations have limited resources, which prevent them from taking advantage of CTI.
From a company size perspective, there appears to be a strong correlation between organization size and the business value of CTI outsourcing. This can be explained by the unfavorable relationship between managed services costs and cyber risks for small and medium-sized companies. Indeed, for companies in this segment, the price of outsourced CTI offerings is too high relative to their risk assessment. Larger companies, on the other hand, benefit from the new maturity of the CTI sector as the diversity of offerings allows them to constantly adapt to the cyber risk assessment of their organization and its assets. From a sectorial perspective, the business value of outsourced CTI for a company will depend on the relevance of CTI’s sources. Manufacturing industries will highly benefit from mutualization as plenty of attacks’ schemes targeting these organizations are listed.
Two different cases can be distinguished. The first one in which both options generate low business value (corresponds graphically to the lower-left square). In this case, we consider companies for which the added value of CTI is too low compared to its cost, due to limited financial means and/or low exposure to cyber threats. In this scenario, CTI can be implemented in a partial way, performed by other security professionals in the organization (internal solution) or asked on top of another managed security offer (external solution).
The second case happens when both the in-house and outsourced options generate a high return. In this situation, whether a company falls on one side or the other of this line depends on individual characteristics intrinsic to the company. This explains why two companies with similar attributes in terms of size and industry may make different choices with respect to CTI. A large company with a well-developed culture of confidentiality will move horizontally along the graph favoring the development of CTI capabilities internally.
Finally, despite the growth in maturity of the CTI market, for a company to find an offer fully corresponding to its expectations is not guaranteed. However, this seems essential for companies with important and specific assets (e.g., Finance, Healthcare providers). These organizations can move vertically along the graph, only favoring the buy option if it reaches a sufficiently high level of customization.
The bottom line is that the CTI market is in the throes of change. Security functions that were once considered advanced are now core products ready to be consumed by companies and sold by vendors, raising the fundamental question: which functions are better off outsourced? The conclusion of the article is that the diversity of CTI’s offerings makes it possible to meet the requirements of most businesses. This growth in maturity of the sector also allows giving guarantees on the level of expertise of the service. However, if outsourcing enables to avoid important setup and running costs, some companies do not get significant business value from it. This may be due to their size and exposure to risk that does not justify such an investment. It may also be due to the specificity of the sector and the absence of offers that adequately meet expectations. Finally, some companies maintain a strong culture of confidentiality and prefer to develop internal CTI capabilities.
Cyber risk is new, which makes it particularly difficult to assess. If one were to go to small businesses with external CTI, most would be ecstatic. After a while, they would realize that the information they received is too big to process and not directly useful to them. This shows that the contribution of CTI can be overestimated and that the definition of the needs of the company according to its exposure remains the key step before considering building or buying any CTI.
To go further…
Imagine you are a company whose head office is in a certain zone, zone A. Now, let’s say that zone A has experienced a crime wave against businesses. Naturally, you check that your cameras are working, that your fences are resistant and dissuasive, that your alarm system goes off in case of an intrusion. Naturally, you hope that the police investigations will provide you with information about these malicious actors. It would never occur to you to pay a third-party company to investigate these offenders since it is the role of the police and more broadly of the state to combat crime. Now, if we transpose this situation to cyberspace, we witness double standards. Apart from a few exceptions within the public sector, a company can only rely on itself when it comes to defending against cyber threat actors. Today, CTI data sharing should be the norm, and seeing projects like OpenCTI type platform being at an embryonic stage shows both promises and how far we still have to go.