

IT/OT Segmentation
Creating strongholds within the fortress
One of the most basic security issues found when tracing back successful breaches is that once attackers had compromised an entry point they could move fairly easy within the network. So while the outside perimeter proved to be fairly resilient there was virtually no control that could restrict what is known as “lateral movement” within the victims network.
The good news is: there is a remedy to this issue. Once a threat actor has tricked and worked their way into a single part of the network, say the office of location A – why not confront them with another firewall when trying to access location B? Why not confront them with a much harder to crack firewall when trying to access accounting? This is called “segmentation” and while it should be best practice it is oftentimes skipped, though modern firewalls are easily capable of implementing this, if configured correctly.
Leveraging the full capabilities of a next-gen firewall
Segmentation affects all layers of the OSI layer model. In addition to a purely physical separation (Layer 1), the formation of virtual LANs (VLAN) on Layer 2 and the division of a network into subnets (Layer 3), today’s technologies also enable the strict isolation of network traffic on the higher layers 4 -7, e.g. through the use of a next-generation firewall (NGFW). And while segmentation should be set up by experts: once set up it will massively add to both your security and the value you make of your firewall.
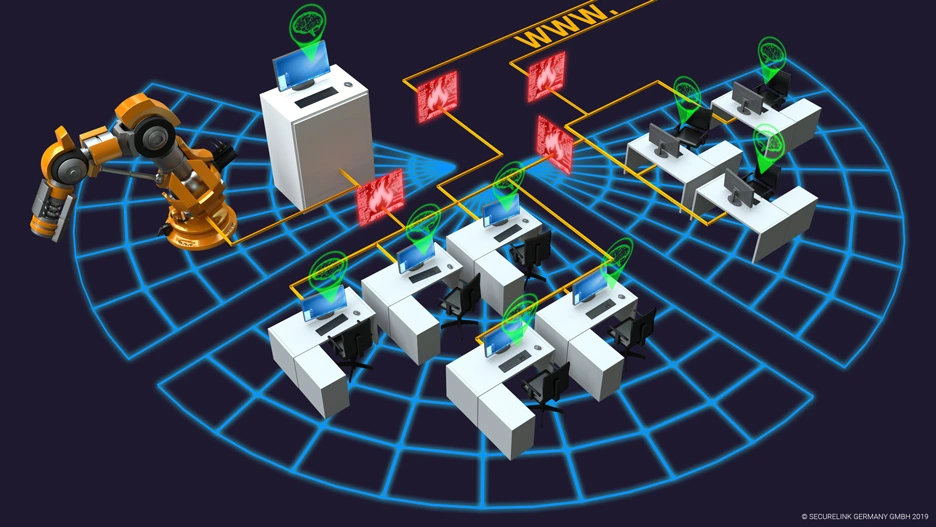
Focussing on OT context
Industrial networks use very similar technologies as you know from your enterprise and office IT. Most are based on IP and Ethernet and use wireless or wired transmission paths. But this is where the similarities end. Serial transmission paths are still widely used today, such as RS232 or RS485.
Requirements such as real time, fault tolerance, secured bandwidth and latency are extremely important in industrial networks. Availability goes beyond the integrity and confidentiality of data, with serious consequences. These design principles of industrial protocols are today transferred to Ethernet and IP, and entire industrial system landscapes are migrated to them.
What on the one hand means ubiquitous networking using the same technologies as in enterprise and office IT has, on the other hand, unpleasant side effects: significant security risks if no suitable network design principles are used, e.g. adapted network segmentations.
Infrastructure segmentation is the first step in a holistic view of both your classic IT and your industrial production landscape.
Services we offer:
- we check your infrastructure and prepare the architecture for effective segmentation
- we take care of the delivery, installation and configuration of the NGFW
- You can also rely on a team of experienced NGFW experts at any time in the further course
Our partners in technology:
- CheckPoint
- Palo Alto Networks
- Fortinet
More articles


