Security Navigator: Trends and Strategies for 2024

These trends are crucial for your cybersecurity strategy in 2024
A rock-solid cybersecurity strategy requires making sharp choices. Because resources, time, and manpower are always scarce. You can only make those choices well if you know what is going on in your threat landscape and link this to your business objectives. That is why we collect a large amount of security data every year. The result: the Security Navigator 2024, a 180-page report with statistics, background, and interpretation from experts. The report exposes these trends:
1. Cyber extortion is increasing faster than ever
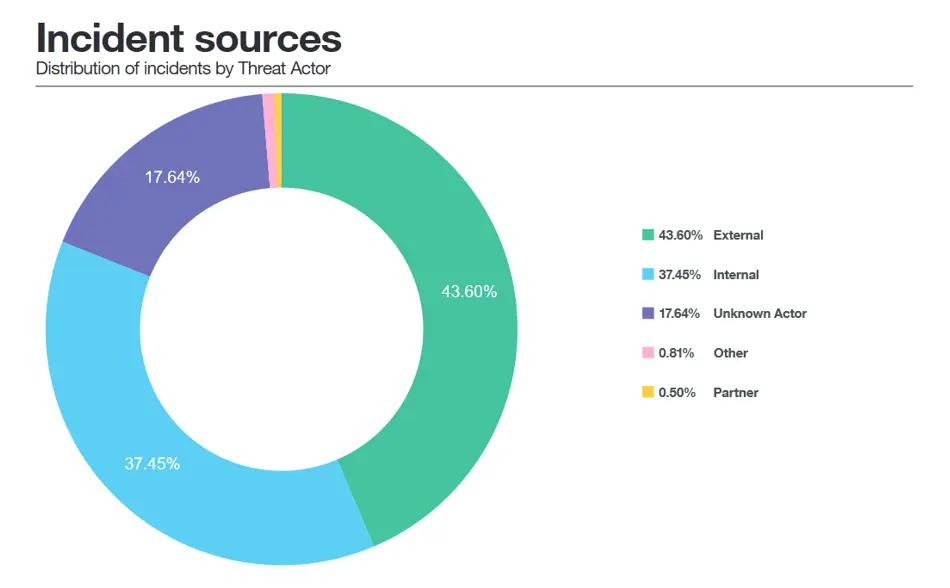
Cyber extortion is by far the most important cyber threat of the moment. Over the past 12 months, our researchers have documented 3,502 organizations that have fallen victim to this.
Moreover, in addition to the traditional ransomware methods, in which attackers demand a ransom in exchange for decrypting encrypted data, new ransomware techniques have emerged. For example, attacks in which attackers threaten to place data on public leak sites. Since January 2020, researchers registered 8,948 victims of this type of cyber extortion. According to Charl van der Walt, Head of Research at Orange Cyberdefense, a good backup is not sufficient with this attack method. “After all, restoring the data does not remove the risk of a gigantic data breach.”
According to Van der Walt, the fight against cyber extortion is tough. “Many of these current attacks are driven by unpredictable geopolitics. No one knows the attack tactics of tomorrow. The threat landscape is continuously changing.”
2. Vulnerability management is and remains crucial
Vulnerability management is one of the most crucial parts of defending against cyber attacks. Many organizations struggle with this aspect: a shocking 85% of vulnerabilities remain unpatched. This is worrying, because hackers are increasingly targeting these vulnerabilities. It is often the most effective way to circumvent security facilities such as a firewall.
Various methods can help improve the vulnerability management strategy. Van der Walt mentions two examples:
DSS (Decision Support System): “A DSS collects, analyzes, and presents data about vulnerabilities in a way that is understandable to decision-makers,” Van der Walt explains. “That helps with prioritizing the vulnerabilities and taking measures such as implementing patches.”
EPSS (Exploit Prediction Scoring System): “EPSS is like a weather forecast for cybersecurity. The so-called EPSS score - a number between 0 and 1 - tells you how likely it is that a certain vulnerability in your software will be exploited by hackers. This helps you decide which vulnerabilities to address first.”
3. Don't ignore internal threat actors
Internal threats pose a significant risk to organizations. No less than 37% of all security incidents occur among our own employees. These threats range from malicious actions by employees with a desire for revenge to an employee accidentally clicking on a link in a phishing email.
Mitigating these risks requires a culture of security awareness. Continuous monitoring is also necessary to quickly identify suspicious activities. “It is also important that internal tensions are resolved as much as possible, so that no breeding ground for resentment arises,” Van der Walt notes. “Employees should also feel comfortable reporting potential security incidents without fear of repercussions. Instead of punishing, organizations should reward their employees who dare to admit mistakes.”
4. Cyberwarfare: a growing threat
Iranian employees at a steel factory recently had to run for their lives . The reason: liquid steel at 1300 degrees Celsius gushed from the boilers onto the work floor. The cause: a devastating cyber attack mounted by 'Predatory Sparrow', a fanatical hacker group affiliated with Israel. They took revenge for Iran's worldwide attacks on Israeli-made equipment at water companies. And for the rocket attacks by the Houthi rebels.
Destructive cyberwarfare attacks with serious physical consequences such as these seem like a far cry. Yet Western organizations can also become victims. Not only because the West is increasingly involved in conflicts, but also because collateral damage can arise from cyberwarfare attacks. This also applies to organizations that are completely outside any conflict. “Cyber attacks on one target can intentionally or unintentionally impact other systems connected by the same network. Moreover, malware is not always picky, not even the malware in cyber warfare,” says Van der Walt.
Generative AI also plays a growing role in cyberwarfare. For example, it was recently announced that Russian, North Korean and Iranian hackers were making full use of ChatGPT to search for vulnerabilities and generate code. “This not only simplifies their attacks, but also puts them within reach of a broader group of hackers,” Van der Walt explains. “Furthermore, technologies such as deepfake and advanced machine learning models offer new opportunities for attackers. For example, to spread misinformation and circumvent security mechanisms.”
5. Smartphones pose a growing risk
Smartphones increasingly contain sensitive business data. In addition, they play an increasingly important role in security processes. Consider multi-factor authentication, where the employee must enter a code that is sent to the telephone. Both aspects make these devices an interesting target for hackers.
In addition, the operating software on these devices is certainly not free of vulnerabilities. For example, Apple's iOS already had 16 found (and patched) zero-day vulnerabilities in September last year. Enough reasons to include these devices prominently in your security strategy.
Timely patches and updates are not enough. Last year, the infamous Pegasus spyware once again showed the continued refinement of attack techniques. This spyware - originally developed for espionage purposes by Israel's NSA Group - was found to be able to break into iPhones without their owners realizing it. Simply via an invisible message or 'silent' call.
“Even fully updated smartphones are therefore vulnerable to advanced attacks,” says Van der Walt. “In addition to a strict patch policy, this requires measures such as advanced endpoint security, attention to security awareness and continuous monitoring for suspicious actions.”
6. OT security: often an IT matter
The number of known malware targeting industrial systems continues to increase. It is further fueled by the war in Ukraine. These threats usually do not arise from the OT systems themselves but from the underlying IT infrastructure. This is an increasing problem because OT environments are increasingly dependent on IT due to smart automation. This makes the threat landscape more complicated, with IT-targeted attacks able to unintentionally cause major problems in OT environments.
“OT systems are also designed to work reliably and consistently. They often contain outdated technologies that are vulnerable to modern cyber threats from the IT environment,” says Van der Walt. “Many organizations are also reluctant to regularly patch their OT systems, for fear of failed patches and therefore disruptions and downtime. However, thanks to special backup systems that get OT systems up and running again very quickly, you can prevent downtime.”
Tackling risks
The best approach to get a grip on all the risks and developments described above? According to Van der Walt, that question is difficult to answer in concrete terms. “The landscape is changing so quickly. Today's optimal strategies may be outdated tomorrow. The most important security characteristic that organizations must develop is therefore agility. You must be able to quickly adapt to new threats and insights.”
Another, equally important characteristic is a clear view of the threat landscape. “Security is a matter of making choices. But you can only make those choices if you know what the most important risks and threats are for your specific situation.”
CyberSOC
An effective way to combine and strengthen these features is to invest in Managed Detection & Response (MDR) through an external Security Operations Center (SOC). A team of specialists monitors the entire infrastructure 24/7. In the event of any threats, they can intervene quickly in consultation with the organization in question. This offers the opportunity to respond quickly to new threats and provides continuous insight into the security landscape.
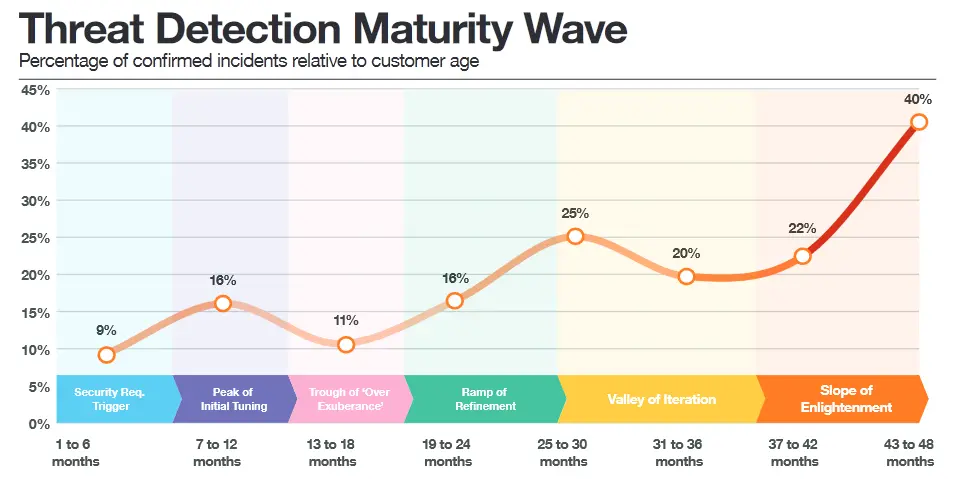
According to the researchers, organizations that opt for services such as a CyberSOC experience a growing Return On Investment (ROI) over time. After four years it even increases sharply. This is because both parties are getting to know each other better and working together more effectively. Machine learning also plays an important role here: thanks to this technology, real threats are becoming increasingly betterdetected .
“Long-term collaboration with an MSSP ensures a higher share of true positives . Employees therefore spend less time on false alarms and recognize real threats better. This not only saves time, but also enables faster and more effective action. In short: in a long-term collaboration, the security maturity of an organization will gradually improve. For better security, persistence wins,” he concludes.
Security Navigator 2024
Do you want more information, statistics, and background on these trends? The Security Navigator 2024 provides in-depth information, provides research figures, and places them in the right perspective. Download here the full report.
Do you want to improve your cybersecurity resilience and digital resilience? We can help organizations with, for example, managed detection & response. But also by providing insight into the threat landscape, specifically for your organization. We can plot this on your business objectives and ambitions and thus provide appropriate advice on how you can best make the right investments for good and agile cybersecurity. Would you like to discuss this with us without obligation or receive more information about our services? Please feel free to contact us, we are happy to make time for you!
