The Social Problem

Author: Grant Paling, Product Manager, Global Service Lines
Social Media. You love it or you hate it right? Or probably both. It is the cause of much joy and yet at the same time much pain.
When you’re reading that opening sentence, how are you thinking of social media? In a personal context or a business context? Is there a line for you that you draw between where social media is used personally versus in business or is it just a blurred mess?
Some figures to keep in mind
When it comes to cyber risk, social media is surely one of the fastest-growing risks. Indeed, we can see in the 2024 Security Navigator in our Threat Detection data that social threat actions grew slightly as a proportion of all incidents - which when combined with the fact that the total number of confirmed incidents went down from the 2023 report, means that there was an increase in this category where many other categories reduced:

Looking a bit closer the prevalence of Social tactics is even more apparent. When we look at the more granular VERIS sub actions we find that two classic social tactics are among the top ten most seen threat actions. We find this observation also confirmed in Proofpoint's "State of the Phish" report, stating that 84% of businesses experienced a phishing attack in 2022.

Humans, sadly, remain the weakest link in the chain. The “vulnerability” you can exploit without necessarily leaving a clear machine-level indicator of doing so. And it is important to consider this also when looking at the above data – how many pure social threat actions went unnoticed due to there being no “paper trail” as such?
Why is social media being utilized more and more by cyber criminals? Is it more attractive than email these days? What makes it such a dangerous threat vector?
Here are a few thoughts to consider.
Blurred lines: the contextual use of your socials
Social media began as purely a platform for connecting to one another for personal use. Until platforms such as LinkedIn came along, we mainly posted pictures of our children and pets, wrote long statuses we thought somebody might read and of course, the art of “trolling” became popular reminding us that not all social interactions are positive ones. If we compare social media to email, with email there is this separation between business use and personal use that is far less embedded in our psyche. With email, you have work email, and you have personal email. And for many of us, that’s a clear separation we make (and in many cases are forced to make!). But when it comes to social media accounts – Facebook, WhatsApp, even LinkedIn don’t have that clear separation. People cross boundaries. There is no “context switch” and I would argue that the extra vigilance you might have (hopefully from a well-structured awareness training programme) in handling incoming business emails, does not transfer always to use of social media. In using social media, I believe that we still have a more relaxed and informal attitude to it that is baked into our culture (given its rather informal beginnings and our more general use of it today).
Let’s take a scenario where you have the same phishing attempt. The objective is to send you a link that you will then click on that takes you to a phishing site and downloads some malware to begin an attack. The oldest trick in the book, right? Now let’s compare it:
You get an email from a work colleague saying “Have you seen this? We are being acquired…” with a link to click on, via your business email.
You get LinkedIn message from a work colleague saying “Have you seen this? We are being acquired…” with a link to click on, via LinkedIn messenger.
What is your instant reaction to these two attempts to perpetrate the same fraud? Does one evoke more suspicion than the other? Which do you think the end users in your company are more likely to report as a phishing attempt?
Social media: The beginning of the end
Another big difference when we compare social media to email is the level of effort that has been put into security monitoring.
For email, businesses have been spending on email security for as long as I can remember. Social media, on the other hand, many businesses are still spending next to nothing on securing. One big difference of course is that businesses own their email accounts and therefore it is easier to impose control. In comparison, social media is the wild west.
One gap that is actively being exploited on both counts is the lack of community sharing. In the current digital economy, you are only as good as your weakest link and unfortunately many times your weakest link is likely going to be a third party that is investing less in cyber security than you.
Let’s take an example I saw at one of our customers some months ago (and in fact have seen at multiple businesses since).
Looking for new beginnings but only finding bad endings
The first stage of the attack began with what is known as “recruiter fraud”. Because who doesn’t want a new job right? RIGHT?!?!
I hope if you were shouting “YES, ME!” at the screen, you weren’t sitting next to your boss. There would be a lot to unpack there. Who am I kidding, many of you probably only see your boss in real life occasionally and as such, there is no one glancing over your shoulder…
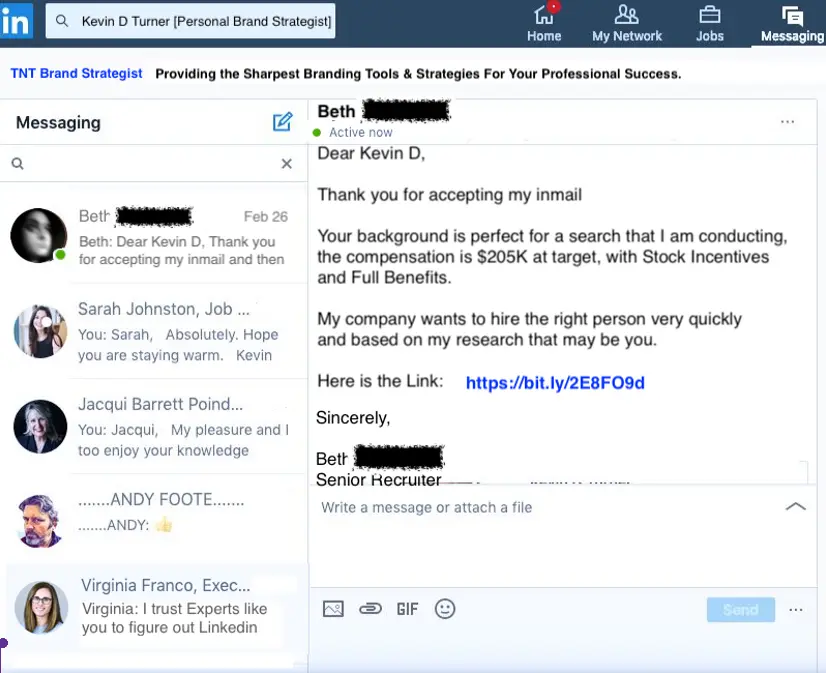
But back to the story. The answer is that even though you are perfectly happy in your job, many are not. And in this story the fraudsters targeted brokers for a financial services company and posed as head-hunters from a rival firm. In came the lure via social media. It looked like any other InMail – recruiter you’ve never met, promises of untold riches and outstanding benefits. All you needed to do was respond.
Here it got interesting. For the few employees that did respond, the attackers encouraged the users to head to Discord, to continue the conversation. It would be easier to share the details they said. (And harder to track their activities we know).
So, they did and the attackers asked them to upload their resumé to a link. The trusting employees did so but it wouldn’t work. Had the attack failed?
Of course not. This was the plan all along. To paraphrase the attackers: “Oh you’re accessing it from your phone? We’ve had problems with that, can you connect via your laptop?”
And of course, our candidates for this super special role went ahead and did just that. And off to the phishing site they went and BOOM. Our attackers are in. Luckily, we were able to detect the attack once the attackers started to move around from there as our customer had our managed detection and response services in place. But not everyone of course has a good level of security monitoring in place and many such attacks out there in the world have succeeded where this one failed.
But could the attack have been stopped earlier? And how?
First, it’s tough. It’s tough because let’s say you have invested in a service like our Managed Cybercrime Monitoring service and that includes monitoring both fraudulent domains and monitoring of fraudulent social media accounts trying to infringe on your brand. That is all fine and well but, in this case, it was a third party (a competitor!) whose brand was being used against your users and then you are exposed by your competitors(!) not playing their part. The first piece of advice would be, don’t be the weak link. Control your own brand usage as much as you can and look to ensure your third parties (during your third-party security assessments) are doing the same. Network with your peers through cybersecurity communities. Share best practices. Do what you can.
Ensure your users are equally well educated on social media scams, as they are on email phishing. Because attackers are coming through more than one door. The same goes for other emerging alternatives like vishing, smishing and QR code scams.
If you become aware of a malicious site, report it. We set up the Phishing Initiative for the community, as part of playing our role in building a safer digital society. Let’s work together as much as we can, because we know that our adversaries are (save the odd infighting between ransomware groups).
Summary
Social Media remains a growing threat vector that needs attention and should be factored into risk analysis. Corporate-owned social media accounts are obvious digital assets that need protecting but by proxy, the (often personal) accounts of executives and other key figures in the business may be targeted. Whether you like it or not, securing social media and the associated risks of hacked accounts, brand exploitation and social engineering (to name a few) is a responsibility of all businesses and requires some attention. You can of course call on Orange Cyberdefense to help advise you on the topic and provide associated services that help you to play your part, as we do, in creating a safer digital society.
The safest thing right now is probably not to respond to any job offers. Your boss would appreciate it too. Happy socializing and be safe!
Links
Proofpoint "2023 State of the Phish" report: https://www.proofpoint.com/uk/resources/threat-reports/state-of-phish
Link to Managed Cybercrime Monitoring page: https://orangecyberdefense.com/global/all-services/detect-respond/managed-cybercrime-monitoring
Link to MDR services: https://www.orangecyberdefense.com/global/all-services/detect-respond
Link to Assess & Advise: https://www.orangecyberdefense.com/global/all-services/assess-and-advise