BIG-IP version 15.1
Will your F5 Networks system support the next version BIG-IP 15.1?
The following F5 Networks systems can support the latest version and features of BIG-IP 15.1:
- BIG-IP 2000s
- BIG-IP 2200s
- BIG-IP 4000v
- BIG-IP 4200v
- BIG-IP 5050s
- BIG-IP 5250v
- BIG-IP 7050s
- BIG-IP 7250v
- BIG-IP 10050s
- BIG-IP 10250v
- BIG-IP 12250v
- All BIG-IP iSeries
- VIPRION B2120
- VIPRION B2250
- All BIG-IP Virtual Editions version 13.0.0 or later
End of Software Development
An important consideration must be made for the BIG-IP 2×00, 4×00, 5×00, 7×00, 10×50, 12250 systems. The hardware platform will be End of Software Development on April 1st, 2021.
The End of Software Development marks the end of the regular support phase, F5 Product Development cease the repair of confirmed software defects for the designated platform or software release.
The most important features of BIG-IP 15.1
Management features
- Improved management of BIG-IP system services
- Behavioral DoS Dashboard Improvements
- Additional data collection options for AFM DoS reports
- Application Visibility Report DoS attack
- PCI Compliance 3.2 check
Security features
- Policy Builder Reorganization
- New Security Violation Attack Types
- Reduce False Positives
- CAPTCHA Sound Support
- Modernized Customization of APM Client UI
- Improved Actor Intention Behind the same IP Address (NAT)
Network features
- Session persistence in HTTP/2 full-proxy configurations
- Hybrid SSL Acceleration
- Enforcement of RFC compliance for the HTTP protocol
Details: BIG-IP 2000s and 2200s
April 1, 2018 was the end-of-sale date of the BIG-IP 2000 series. So, now is the ideal moment to upgrade to the new BIG-IP iSeries i2600 or i2800 which provide a more efficient price/performance ratio.
The BIG-IP i2600 and i2800 has double throughput capacity compared to their predecessor. The BIG-IP i2600 and i2800 have a dual power supply possibility, and a 10 Gbps Fiber or Copper Direct Attach option.
BIG-IP 2000 series vs BIG-IP iSeries 2000: a comparison
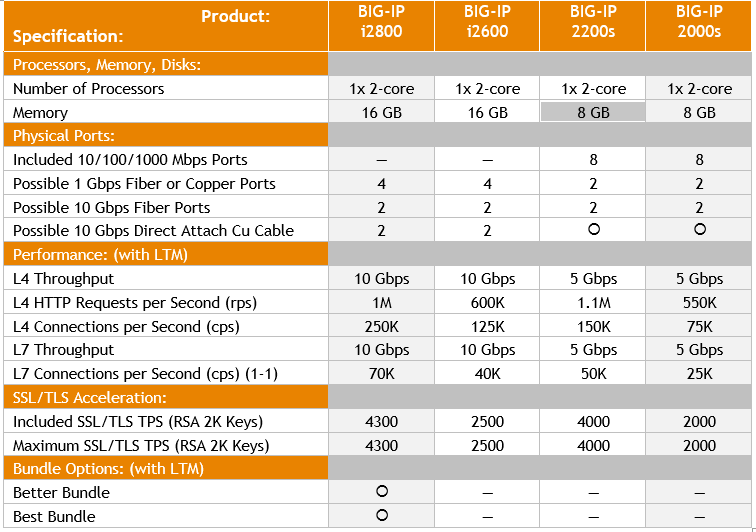
The BIG-IP iSeries 2800 is the entry level F5 Networks system that can be licensed with a Best Bundle.
BIG-IP 4000s and 4200v
April 1, 2018 was the end-of-sale date of the BIG-IP 4000 series. So, now is the ideal moment to upgrade to the new BIG-IP iSeries i4600 or i4800 which provide a more efficient price/performance ratio.
The BIG-IP i4600 and i4800 has double throughput and SSL/TLS acceleration capacity compared to their predecessor. The BIG-IP i4600 and i4800 have a dual power supply possibility, and a 10 Gbps Fiber and Copper Direct Attach option.
BIG-IP 4000 series vs BIG-IP iSeries 4000: a comparison
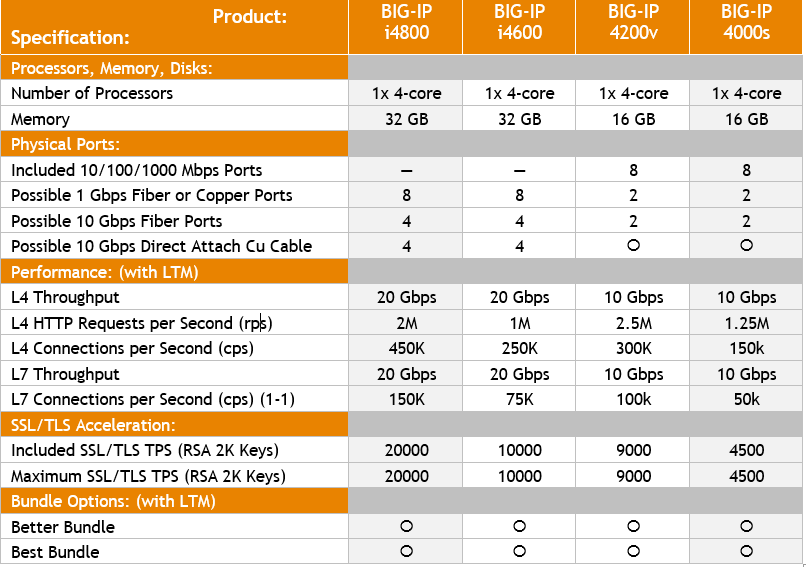
The BIG-IP iSeries 4000 has double processing, memory and 10 Gbps connection capabilities compared with its predecessor.
BIG-IP 5050s and 5250v
April 1, 2018 was the end-of-sale date of the BIG-IP 5000 series. So, now is the ideal moment to upgrade to the new BIG-IP iSeries i5600 or i5800 which provide a more efficient price/performance ratio.
The BIG-IP i5600 and i5800 has double throughput capacity compared to their predecessor. The BIG-IP i5600 and i5800 have a solid state drive as a standard, dual power supply possibility, and a 40 Gbps Fiber option. The BIG-IP i5800 series is the first F5 Networks platform in the portfolio supporting multiple virtual F5 Networks BIG-IP instances through virtual Clustered Multiprocessing and dedicated hardware acceleration for network and SSL/TLS traffic.
A comparison: BIG-IP 5000 series vs BIG-IP iSeries 5000
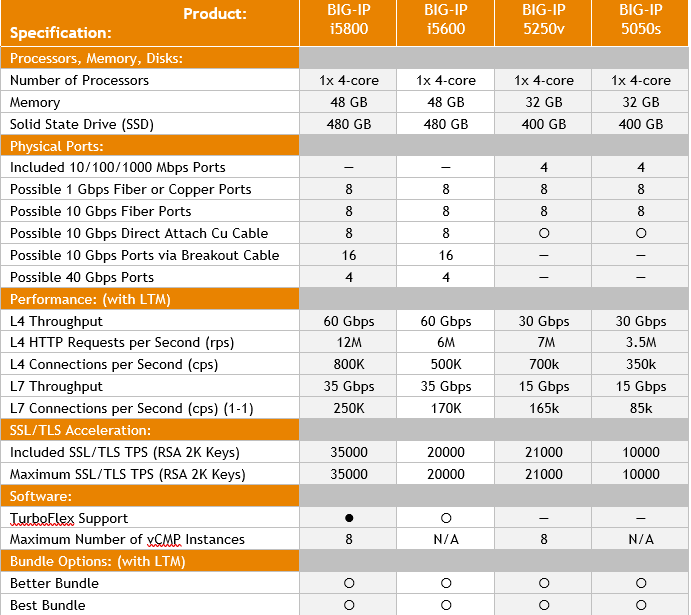
The BIG-IP iSeries i5800 is thanks to the multiple Virtual Clustered Multiprocessing instances and hardware acceleration the perfect model for any organization requiring cost efficient utilization of F5 Networks features in the data center.
BIG-IP 7050s and 7250v
April 1, 2018 was the end-of-sale date of the BIG-IP 7000 series. So, now is the ideal moment to upgrade to the new BIG-IP iSeries i7600 or i7800 which provide a more efficient price/performance ratio.
The BIG-IP i7600 and i7800 has triple processor and memory capacity compared to their predecessor. The BIG-IP i7600 and i7800 have a solid state drive as a standard, dual power supply as a standard. The BIG-IP i7800 series is thanks to the processor and memory capable of supporting more multiple virtual F5 Networks BIG-IP instances through virtual Clustered Multiprocessing than its predecessor. The dedicated hardware acceleration for network and SSL/TLS traffic makes this the perfect platform for any enterprise that would like to take advantage of the full capabilities of F5 Networks.
A comparison: BIG-IP 7000 series vs BIG-IP iSeries 7000
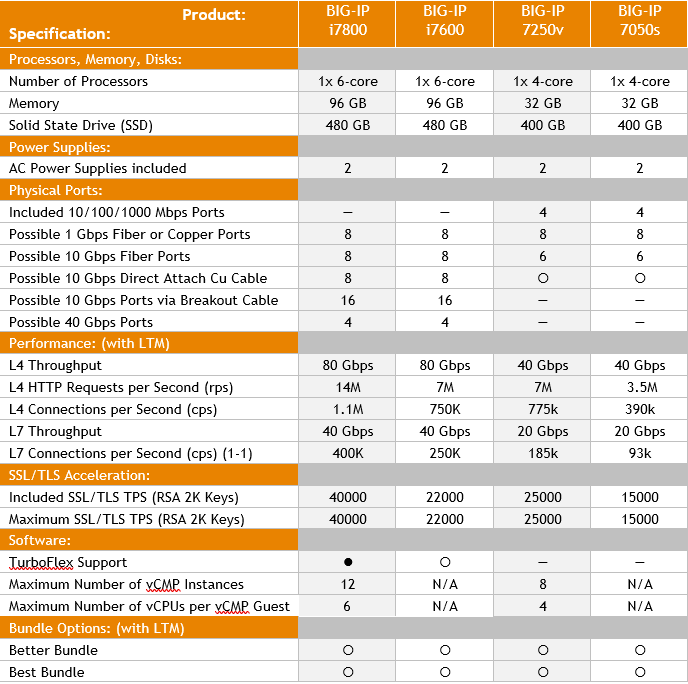
Management features of BIG-IP 15.1
Improved management of BIG-IP system services
With this release of version 15.1, many system services within the BIG-IP system have been improved with respect to bootup time, ease of debugging, and ease of configuration. Affected services include daemons such as httpd and sshd, several F5 daemons, Sysinit scripts such as f5-sysinit, and platform daemons such as bcm56xxd and chmand.
Behavioral DoS Dashboard Improvements
The Behavioral DoS Dashboard includes additional charts and finer granularity on existing charts.
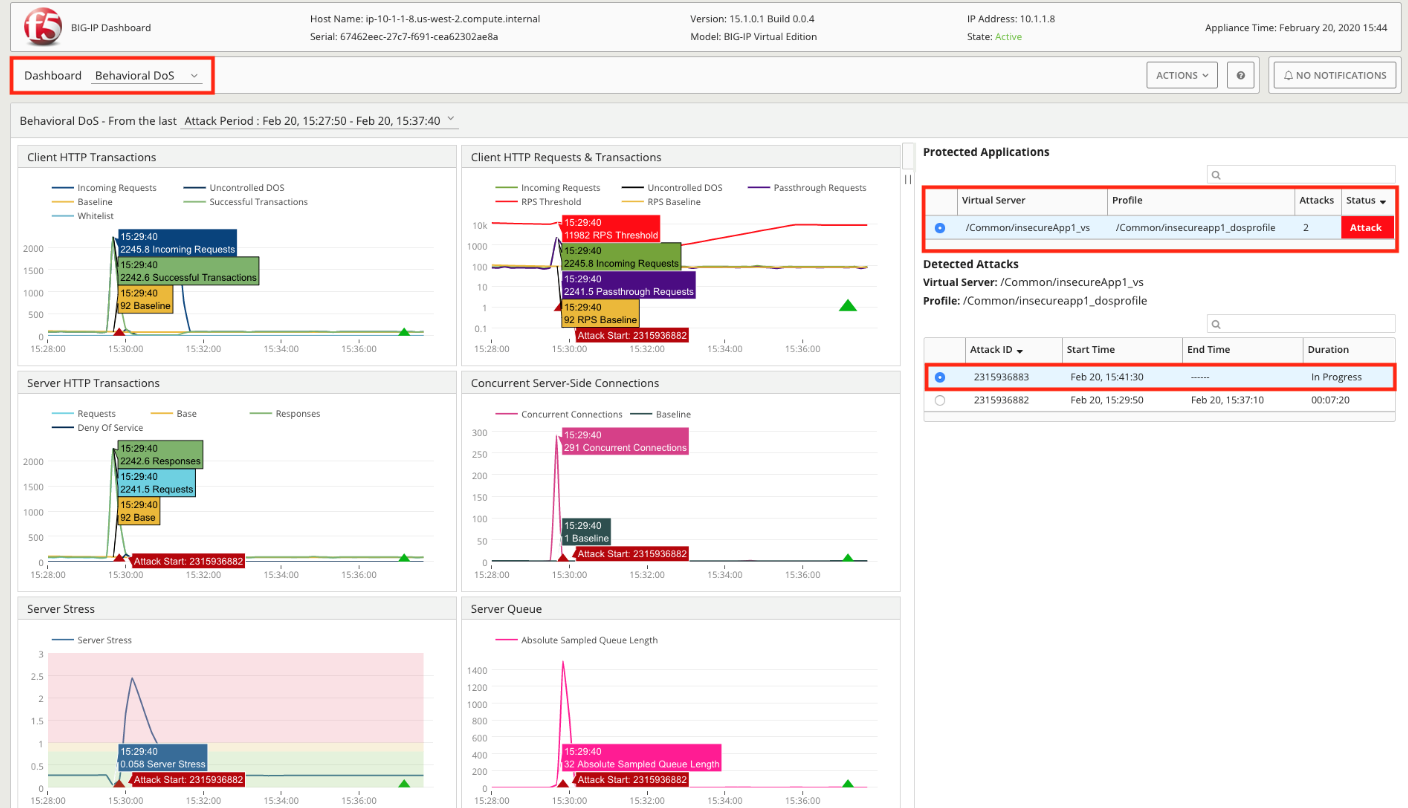
Additional data collection options for AFM DoS reports
The reporting settings for AFM DoS attack information now includes additional reporting options. These options allow you to configure more granular report coverage for your protected objections, once a DoS attack is detected. The added network firewall information improves DoS firewall protection visibility on external reporting tools, such as BIG-IQ Centralized Management.
Application Visibility Report DoS attack
AVR DoS attack reports now include the total packet size, bytes per second, and bytes per packet values.
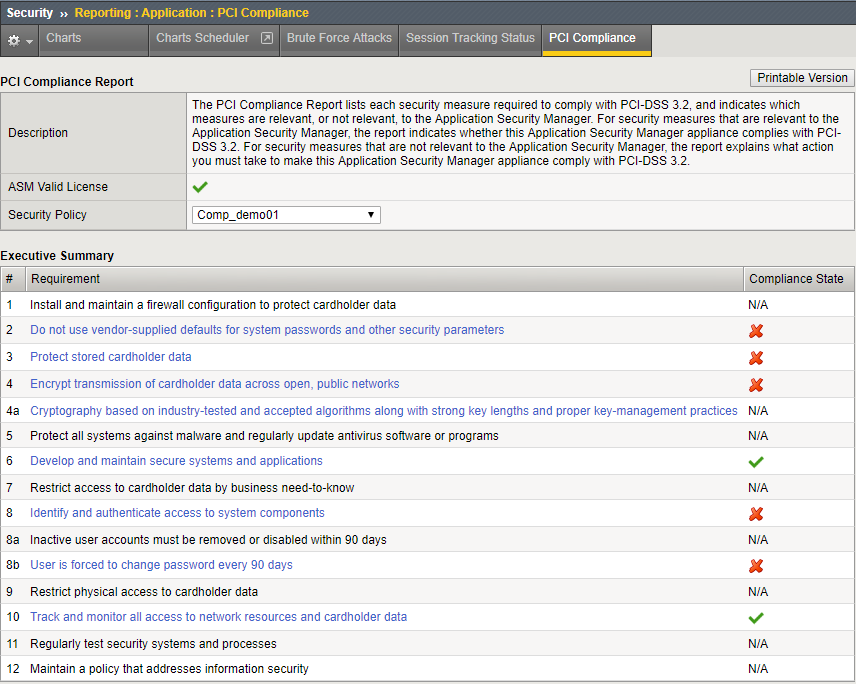
PCI Compliance 3.2 check
The PCI Compliance reporting includes 2 options to automatically fix compliance issues to support PCI Compliance 3.2.
- Encrypt transmission of cardholder data across open, public networks: A PCI compliant Client SSL profile is assigned to all virtual servers that have no or an insecure SSL profile.
- User is forced to change password every 90 days: All password expiration periods are set to 90 days.
Security features of BIG-IP 15.1
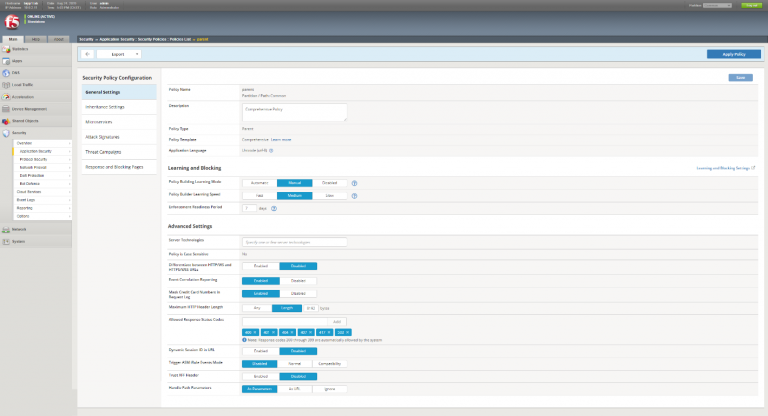
Policy Builder Reorganization
The policy building process has been consolidated into a single tabbed screen containing the configuration for a policy’s:
- General Settings
- Inheritance Settings
- Microservices
- Attack Signatures
- Threat Campaigns
- Response and Blocking Pages
The Policies List now displays the name, enforcement mode, attached virtual servers and OWASP compliance for each policy.
New Security Violation Attack Types
New, more precise, security violation attack types have been added for better triage and investigation of attacks. The new attack types:
- Are associated with attack signatures
- Are available in REST API for an attack-type resource query
- Can be used in user-defined signatures
- Are displayed in the GUI signature screen
- Are displayed in the request log for requests that have these attack signatures
- Can be used as search criteria to filter signatures and request logs
The new attack signatures are:
- XML External Entities (XXE): This is a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser.
- Insecure Deserialization: This is an attack against an application that receives serialized objects. An application which does not restrict which objects might be deserialized could be exploited by attackers sending specific objects, called “gadgets”, that could trigger arbitrary code execution when deserialized.
- NoSQL Injection: NoSQL databases are non-relational databases, and even though they do not use the SQL syntax, non-sanitized input might let attackers control the original query via a database specific programming language.
- Insecure File Upload: Many applications allow uploading files to the server, such as images or documents. An application that does not correctly restrict the type of the uploaded files or the upload folder path can be exploited by attackers to upload files, called “WebShells”, containing malicious code that later will be executed or override the server configuration.
- Server-Side Template Injection: Some applications use server-side templates for better modularity. This attack occurs when a non-sanitized input containing template directives is embedded into a server-side template which then leads to execution of the injected code when rendered.
- Server-Side Request Forgery (SSRF): Some applications receive a URL as input and use it to submit data to or read data from. An attacker could provide special URLs to read or update internal resources such as localhost services, cloud metadata servers, internal network web applications or HTTP enabled databases.
Reduce False Positives
An algorithm identifies potential false positive signatures, reducing the amount of manual policy fine tuning needed. The identified false positive signatures do not block requests. Violation details include the Unblock Reason and the value is Likely false positive.
CAPTCHA Sound Support
A default CAPTCHA response sound file is included for audio reading of the CAPTCHA challenge to provide accessibility to the visually impaired. This file can be replaced with a custom sound file.
Modernized Customization of APM Client UI
You can now create access profiles and per-request policies with a new customization type of Modern. Modern policies have a new, up-to-date look for the client logon page, webtop, and other elements that can be customized. This is now the default type when creating access or per-request policies.
Improved Actor Intention Behind the same IP Address (NAT)
Using TLS fingerprints identification, the system can now distinguish between bad and good actors behind the same IP (NAT) and only block traffic from bad actors. When TLS fingerprints identification is disabled, any attack behind the NAT treats all users behind the NAT as attackers.
Network features of BIG-IP 15.1
Session persistence in HTTP/2 full-proxy configurations
For HTTP/2 full-proxy configurations, version 15.1 now includes support for all session persistence types except Hash and SSL persistence. Also added to this release is support for both the HTTP Cache feature and BIG-IP Application Security Manager (ASM).
Hybrid SSL Acceleration
BIG-IP platforms with hardware SSL accelerators can split the SSL offload between the hardware accelerator and the system CPU.
Enforcement of RFC compliance for the HTTP protocol
The BIG-IP system can now perform basic RFC compliance checks on HTTP traffic as described in the latest RFC for the HTTP protocol.
When you enable the Enforce RFC Compliance setting on an HTTP profile and then assign the profile to a virtual server, the BIG-IP system attempts to reject non-RFC-compliant HTTP traffic and reset the connection.
Need Assistance ?
Do you have any questions or do you want more information on this subject?
Please do not hesitate to contact via our F5 Networks contact page or via +32 3 641 95 95.
