Mobile phones: what are the most frequent cyber-attacks?
Hackers compete with imagination. Here are their main techniques of attacks on mobiles.
Request for permissions
This is probably the most used technique for Android malware. It allows an application to request authorizations from a user by hiding behind a fraudulent window.

Source: ©Android, Orange Cyberdefense
On the right, a legitimate permission request leaves the user the choice to allow it. On the left, the same request is hidden by an information window that leaves the user no choice but to accept the authorization. This fake information page is often displayed before the attack because all of the hacker’s next actions will require sensitive authorizations, such as access to SMS or phone memory in particular, which the phone owner will grant in the thought of validating information pages.
Keylogger
The purpose of the keylogger is to retrieve all the actions performed by a user and store them in a file. This file will be sent back to a server to extract sensitive data. For example, if the user types his credentials to connect to Facebook, the keylogger will retrieve them.
The most common technique to make a keylogger is frame overlay. This consists of superimposing small invisible squares (one on each keyboard) on the user’s keyboard. Thus, when the user clicks on a key, he will click on one of these small squares.
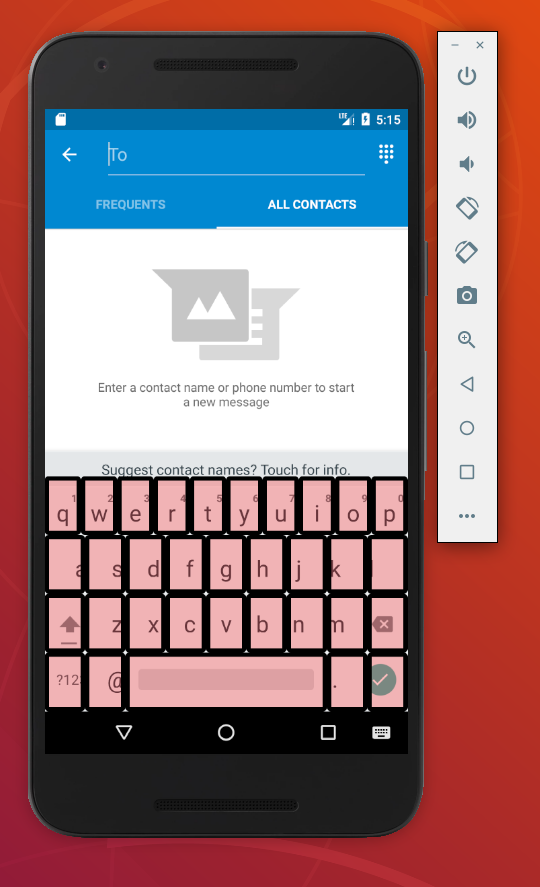
Source: ©Android, Orange Cyberdefense
A second method consists of tracking the different events sent by the system and, more specifically, those three: “Clicked,” “Focused,” and “Text.” The first one will know which button the user has clicked on, the second one on which web page he is surfing. The last one records all the texts he composes.
Overlay of forms
This technique has the same purpose as the keylogger, with the difference that it will retrieve only the usernames and passwords of a particular page. To do this, a fake login overlay is overlaid on an application without the user realizing it. For example, if the user is trying to connect to eBay, the photo on the left will appear legitimate.
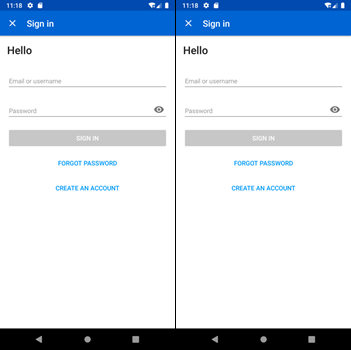
Source: ©Android, Orange Cyberdefense
If the corresponding overlay is present in the malicious application, the right photo will appear: true copy, but it is a fake. The user’s credentials will be sent to the hacker.
Recovery of messages (SMS grabber), calls, and contacts
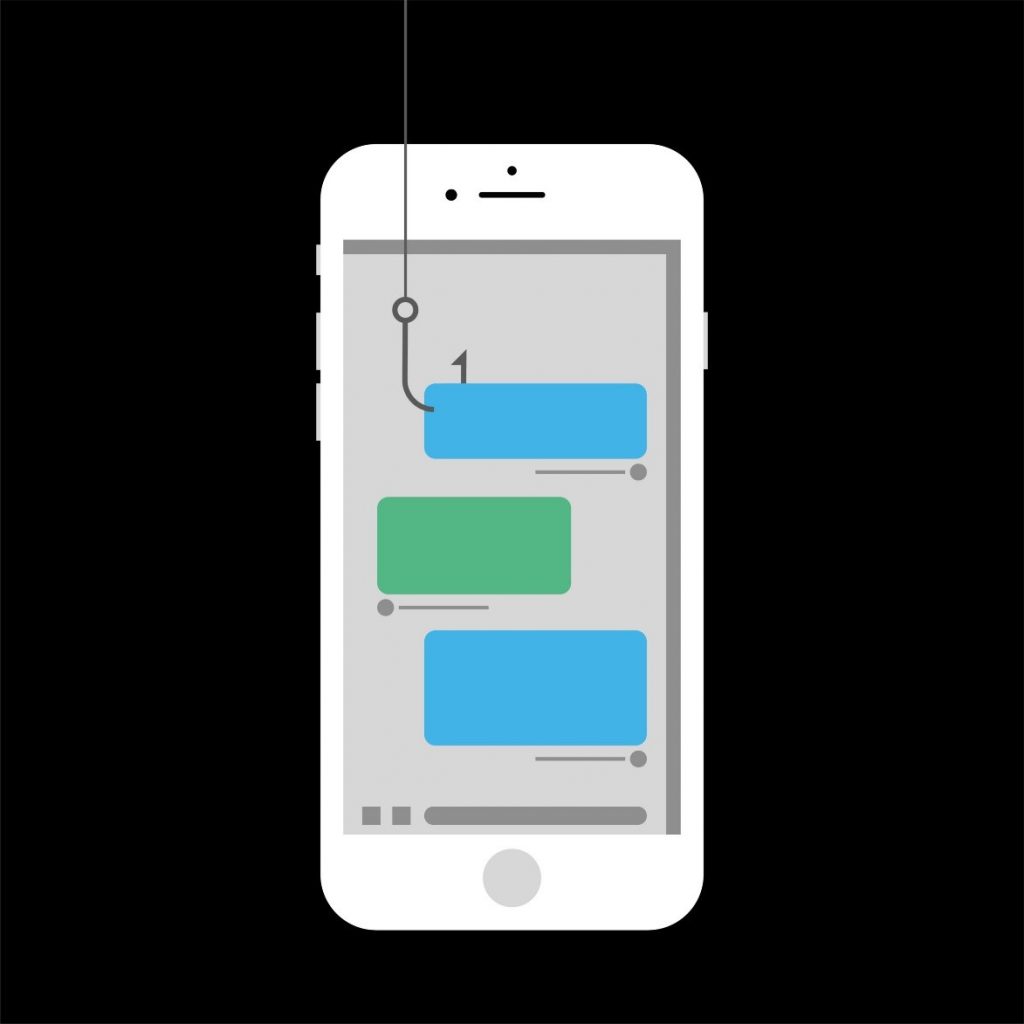
Source: Orange Cyberdefense
Malware is often used to retrieve (and even send) SMS messages, access contacts, and listen to a user’s phone calls. Authorization to read, send SMS, make calls, access contacts are requested by the virus.
Indeed, recovering SMS becomes essential for bank malware to steal usernames, passwords, or other useful information, especially when the bank sends a control SMS for double authentication when shopping on the Internet. The malware can then retrieve the code sent by the bank and use it to validate a transaction.
Malware also sometimes sends an SMS to the hacker to verify that it is a working phone and not a dummy phone.
Finally, retrieving the contact list allows the malware to spread by SMS or email.
Ransomware
Ransomware will encrypt a file or entire directories of a phone. Usually, the user receives an SMS or a link asking for a fee to retrieve his data.
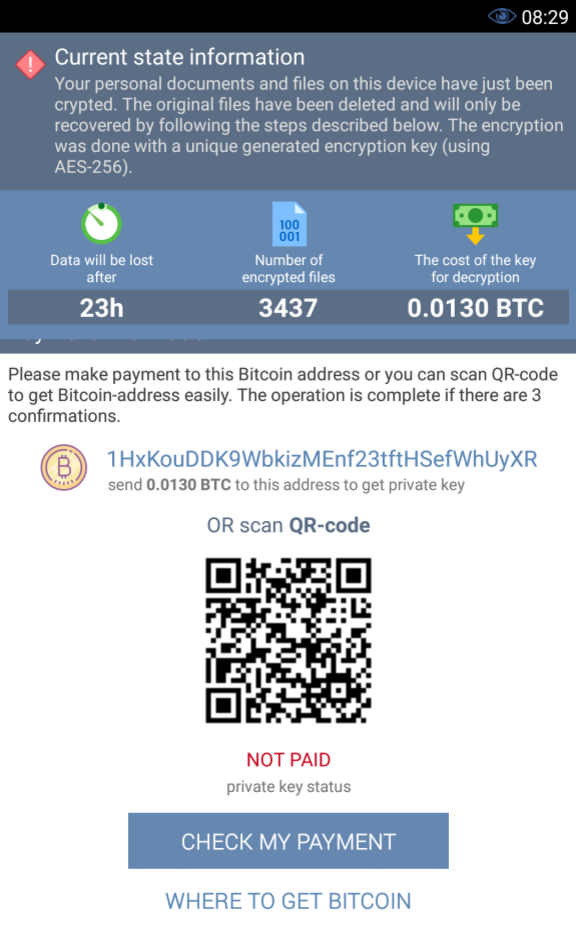
Source: ©Android, Orange Cyberdefense
Adware
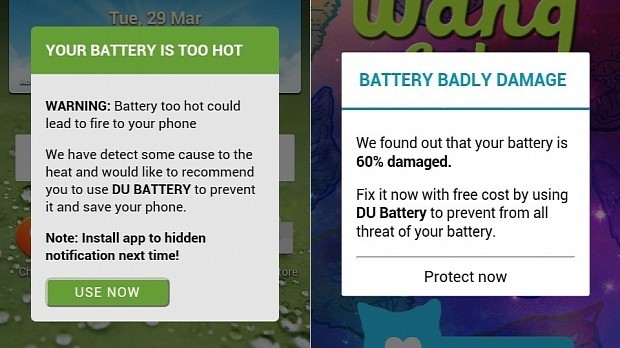
Source: ©Android, Orange Cyberdefense
The purpose of adware is to display a maximum of ads on your phone and mainly in a browser or a notification bar. They are often downloaded via little known websites.
Note that fake apps are also used to display ads. However, they are injected into all applications present on the phone. This technique is rarer.
Because the ads’ origin is less controlled, these ads can lead the user to install other malicious applications.
Camera spy and localization tracker
Telephones are permanently in government officials or business leaders’ pockets and play a key role in espionage. Two features are exciting in this use case:
The spying by the camera phone or camera spy permits to capture video and sound. To do this, the phone will simply ask for permission. To make the mobile owner less suspicious, this technique is usually hidden behind a legitimate application, such as those that allow customizing photos.
The location tracker retrieves the user’s geographical position to send it to a server, even if geolocation is not enabled. To do this, the malware just needs the authorization to access the phone’s location.
Many applications today require this kind of permission; it is important to know that by granting it, a hacker can know in real-time (and especially permanently) where the phone is.
Cryptojacking/Cryptominer
Cryptomining consists of using the resources of a phone to “mine” crypto-money (validate transactions). The process starts in the background, which will result in a loss of performance and battery life for the user.

Source: Orange Cyberdefense
Data stealer

The data stealer will search for specific files in the phone to retrieve them and send them to a server. They are installed on phones through malicious applications.
The exfiltered data can be used for blackmail or industrial espionage.
Conclusion
Most of these techniques abuse the permissions given by the user to an application. To convince the user to provide his access rights, the application will often do something legitimate and useful for the user but, in the background, will perform malicious activities.
To discover some simple techniques to protect your mobile, check out this blog post.
