4 Palo Alto Networks’ tools you have to discover!
This blog will showcase 4 Palo Alto Networks’ tools that will make your daily life easier.
Palo Alto Networks - Configurator
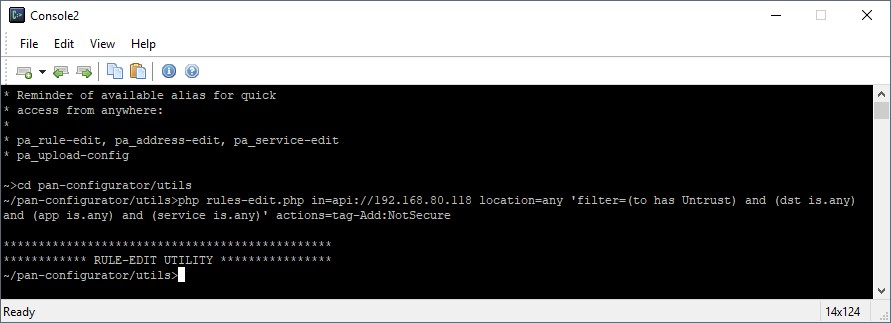
What is it?
PAN-Configurator is a PHP library aimed at making PANOS config changes easy. It may seem a little complex compared to the GUI based approach of the Palo Alto platform, but the commands are straightforward and the documentation provides some examples to get you started.
The tool can be used to manage large rulebases, execute complex rule merges, track unused objects and other actions which are not directly offered by the standard GUI.
The PAN configurator allows you to:
- Add a security profile (group) to all security policies which match certain characteristics like Zone, Dervice, Tag, … Example: Apply a stricter security profile to all policies which allow outbound web traffic.
- Find duplicate objects and replace or merge them.
- Tag rules and objects based on match criteria to create a more structured rulebase or highlight unsecure policies which need reviewing.
Where can I find the PAN-configurator?
The tool comes as a free download at GitHub.
More information can be found on the Palo Alto Networks Live platform.
Palo Alto Networks - Best Practice Assessment (BPA) Tool

What is it?
The Best Practice Assessment (BPA) tool, created by Palo Alto Networks, evaluates a device’s configuration by measuring the adoption of capabilities, validating whether the policies adhere to best practices, and providing recommendations and instructions for how to remediate failed best practice checks. The tool performs more than 200 security checks on a firewall or Panorama configuration and provides a pass/fail score for each check.
The BPA tool is easy to use and provides an instant report.
- Use it to (regularly) review existing customer’s configuration and pinpoint insecure policies.
- Use it as a check list for new installations.
- Evaluate which remarks are valid, or which are not relevant for a specific environment.
Please note that best practices always depend on a customer’s environment. The results should always be interpreted by an experienced engineer. The tool is fast, easy to use and provides an excellent starting point for a more secure and above all consistent configuration.
Where can I find the BPA tool?
Upload config files to the BPA tool at the Palo Alto Customer Success portal.
Palo Alto Networks - MineMeld
What is it?
MineMeld is an open-source application that streamlines the aggregation, enforcement and sharing of threat intelligence. The tool consists of 3 components.
- Miners which extract list of indicators (of compromise) from known sources.
- Aggregators which manipulate these lists to include, exclude or merge objects.
- The output component which provides a list readable by the Palo Alto Networks firewall using external dynamic lists (or dynamic address groups).
MineMeld is a great tool for SOC-based operations and can help with automating some daily (NOC) tasks.
- Track all IPs and URLs associated with Office365 and all its sub-components (Skype for Business, SharePoint online, Yammer, …) to create specific URL filtering profiles, or Policy based Forwarding policies to route certain traffic.
- Use an existing file hosted on a SharePoint to populate URL allow and block lists. This provides fully managed customers the ability to control their own URL lists without the need for login credentials to the Palo Alto Networks firewalls.
- Increase the security of your appliance by leveraging external threat intelligence sources and creating block policies based on indicators of compromise (IOCs) seen in the wild.
Discover more about Response & Detect
Where can I find MineMeld?
MineMeld is available for all users directly on GitHub, as well as pre-built virtual machines (VMs) for easy deployment.
Palo Alto Networks - Load config partial
What is it?
Technically it is not really a tool, “load config partial” is a command that can be used via the CLI. It provides a quick and safe way for copying or merging different firewall configuration. The XML export of a Palo Alto Networks firewall or Panorama appliance can be edited using any text editor, but blindly copying and pasting xml parts can and will lead to mistakes. Using the CLI you can merge configurations with ease. Upload the xml configuration of any firewall: this includes other device models or a Panorama config. You can then choose to merge all the address objects, interfaces, global protect config, … into your current candidate config. After a review using the GUI you can commit your changes. The load config partial command provides validation of the configuration to make sure the xml remains valid. Another practical use case is moving objects between device groups or templates in a Panorama environment.
Where can I find the Load Config Partial?
More information about the command and its parameters can be found here.
