Building protections against Business E-mail Compromise (BEC)
1. Introduction
Trust is a fundamental concept on which human relations are built, it allows us to connect, engage and foster meaningful relationships. For businesses, establishing and maintaining that trust is paramount. Building up trust is a lot of work and takes a while, destroying that trust, however, can be done in the blink of an eye. All it takes sometimes is a mouse-click.
Email, for example, has not been built with security as its primary focus. Yet we rely on it daily to help us build business and personal relationships. Its foundation lies in an assumption of trust between the sender and the recipient.
This reliance on trust creates vulnerabilities that threat actors seek to exploit. They can impersonate trusted senders, use social engineering tactics to manipulate recipients, or intercept emails to gain access to sensitive information. Because email lacks built-in security features, it is the primary attack vector for various cyber threats including phishing, malware distribution, and business email compromise (BEC) scams.
Our internal Orange Cyberdefense CSIRT reported that Business Email Compromise (BEC) stands as the second most prevalent cause of incidents within our customers' environments.
Moreover, our latest Security Navigator report identifies spear phishing as the fourth most prevalent threat action observed.
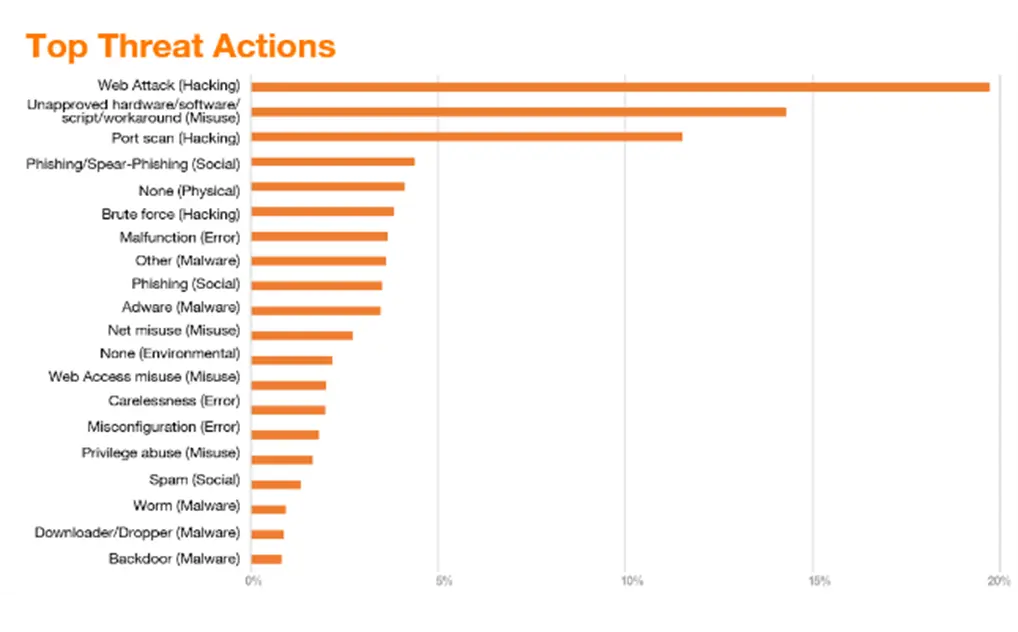
For several months now, our Managed Threat Detection teams have encountered numerous campaigns leveraging phishing emails including QR code as initial access vectors, highlighting the growing sophistication and diversity of cyber threats. The QR codes typically redirect to malicious pages either designed to harvest credentials or to launch the download of malware payloads.
In this blog post, we will focus on how business email compromise scams work, and we will explore the capabilities that exist within the Microsoft security portfolio to protect businesses against these attacks.
2. Understanding the Threat: How does BEC work?
In short, a business email compromise (BEC) scam is a type of cyber-attack where attackers impersonate specific individuals within an organization, such as an executive, to trick employees, customers, or partners into taking particular actions. These actions could include transferring funds, disclosing sensitive information, or executing other harmful tasks.
BEC attacks often involve social engineering tactics and can result in significant financial losses and reputational damage for the targeted organization
To protect businesses against these types of attacks, it is important to understand how a typical BEC scam operates.
- Gather information: Attackers conduct thorough research on their targets before engaging. They often utilize publicly available information from various sources such as social media platforms, company websites, news articles, and public records. This information can include details about the target's job role, responsibilities, colleagues, interests, recent events, and affiliations.
- Email Spoofing: The attack often involves email spoofing, where the attacker creates an email that appears to be from a legitimate email address or domain, such as a company executive, a bank, or a trusted business partner.
- Compromised credentials: In some cases, attackers gain unauthorized access to a legitimate business email account. Once they have taken control, they can easily impersonate the owner of the account whilst bypassing essential security controls.
- Social Engineering: The email usually contains a sense of urgency or importance to prompt the recipient to take immediate action. It could request sensitive information, instruct a wire transfer, or ask the recipient to download an attachment.
- Financial Fraud: Once the recipient complies with the fraudulent request, such as transferring funds or sharing confidential data, the attacker exploits it for financial gain. They may redirect funds to their own accounts or use the stolen information for further attacks or identity theft.
- Consequences: The consequences of falling victim to a BEC scam can be severe. It can result in financial losses for the company, damage to its reputation, legal liabilities, and even job losses for employees involved in the incident.
In essence, a BEC scam preys on trust and human error within organizations, making it crucial for employees to be aware of unusual requests, even if they appear to come from trusted sources. This is why user awareness training is a critical component of a defense in depth strategy when it comes to these types of attacks.
3. Deconstructing BEC: Identifying the MITRE Techniques
The MITRE ATT&CK framework provides us with a database of adversary tactics and techniques that may be used during various stages of a cyberattack. When it comes to Business Email Compromise (BEC) scams, multiple MITRE techniques are relevant. Once identified we can counter these techniques with proper mitigations and security controls.
The following is a non-exhaustive list of some of these techniques.
- T1566.001- Spearphishing Attachment: In this technique, attackers send emails with malicious attachments to specific individuals within an organization. These attachments may contain malware or other malicious payloads designed to compromise the recipient's system or steal sensitive information.
- T1566.002 - Spearphishing Link: Like spearphishing via attachments, this technique involves sending emails containing links to malicious websites or resources. These links may lead to websites hosting malware or phishing pages designed to steal login credentials or other sensitive information. The hyperlink might be replaced with a QR code to bypass traditional URL filtering.
- T1566.003 - Spearphishing via Service: This technique involves crafting emails that appear to be from reputable organizations or services to trick recipients into taking desired actions, such as providing sensitive information.
- T1213 - Data from Information Repositories: Attackers may gather information about targeted individuals or organizations from publicly available sources or data breaches. This information can be used to personalize phishing emails and increase their effectiveness.
- T1078 - Valid Accounts: In some cases, attackers may compromise legitimate email accounts belonging to individuals within an organization. By gaining access to these accounts, attackers can send convincing phishing emails to other employees or external contacts, increasing the likelihood of success.
- T1114 -Email Collection: Before launching a BEC attack, attackers may conduct reconnaissance to gather email addresses and other relevant information about targeted individuals or organizations. This information can help attackers tailor their phishing emails to increase their chances of success.
These are just a few examples of MITRE techniques that may be associated with Business Email Compromise attacks. It's essential for organizations to be aware of these techniques and implement appropriate security measures to detect and mitigate BEC threats effectively.
4. Bolstering Defenses Against BEC: Implementing Mitigations
Once we know how BEC scams operate, countering them with appropriate mitigations and security controls is key to reducing the risk of falling victim to these attacks. Regular security assessments and policy updates are also crucial to staying current as these attacks evolve.
The good news is that the security features required are already included in the most prevalent M365 licensing that many organizations have.
In the following sections, we'll correlate MITRE techniques with their corresponding mitigations, along with specific Microsoft solutions and features. Since certain mitigations are effective against multiple MITRE techniques, this approach aids in prioritizing implementation based on impact and relevance.
User Awareness Training
As stated in the beginning of this article, user awareness training plays a critical role in protecting organizations against cyber-attacks and Microsoft Defender XDR includes attack simulation training out of the box.
This mitigation is applicable to various techniques involving social engineering, such as spear phishing (T1566.001, T1566.002, T1566.003), where users are often the first line of defense. It is also effective against techniques targeting valid accounts (T1562) as users can be trained to recognize and report suspicious account activities.
Setting up an Attack simulation
Attack Simulator allows you to run realistic attack scenarios in your organization to identify vulnerabilities. Various social engineering techniques are available, and Microsoft leveraged the MITRE ATT&CK framework when developing these.
For instance, the credential harvest technique will present users with a URL leading to a fraudulent login page, prompting them to enter their credentials.
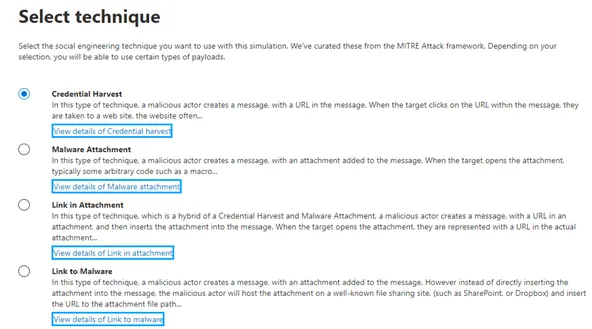
You can select the payload which is the link or attachment in the simulated phishing email message that's presented to users. There is a built-in payload catalog available, but you can also create custom payloads that work better for your organization.
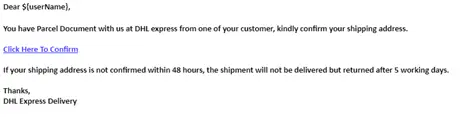
This phishing email appears to be from DHL and includes a message informing the recipient that a package delivery is scheduled. It prompts the recipient to click on a link for more details about the shipment. Upon clicking the link or opening the attachment, the recipient is directed to a fake login page. The default login page is designed to resemble the Microsoft login page, complete with logos, branding, and input fields for username and password.

After selecting the type of phishing simulation and payload, you can target specific users. Additionally, you have the flexibility to assign training to all target users or exclusively to those who clicked on the payload.
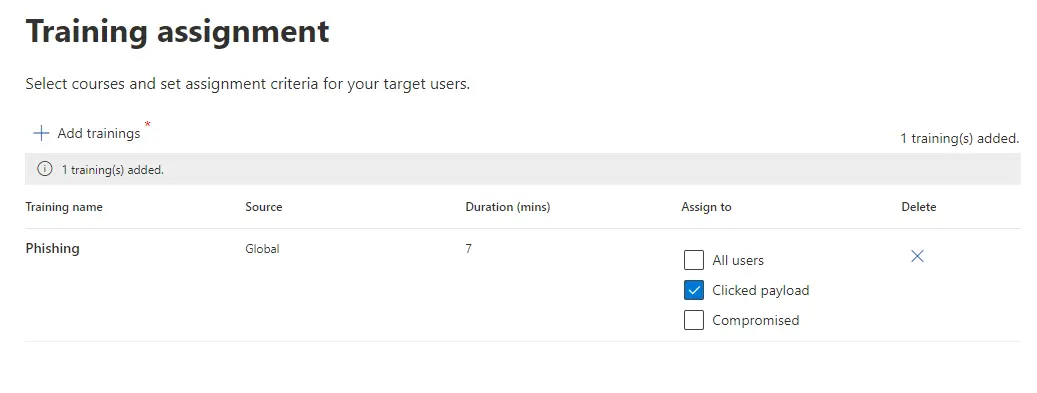
The Phish landing page serves as the webpage users are directed to after opening the payload in the simulation. It offers a valuable learning opportunity and can be tailored to specific needs. Furthermore, you have the option to configure end-user notifications, reminding users to complete the assigned training.
Insights and reports
There are additional steps you should take after running an attack simulation to ensure that your resiliency against business email compromise scams increases:
- Review Results: Analyze the results of the phishing simulation to understand how employees responded. Identify trends, such as common phishing techniques that were successful or areas where employees may need additional training.
- Offer Training: Provide targeted training sessions or resources to address any gaps identified during the phishing simulation. This could include cybersecurity awareness training, phishing awareness modules, or interactive workshops on recognizing and reporting phishing attempts.
- Test Regularly: Schedule regular phishing simulations to continually assess and improve the security awareness of employees. Use different scenarios and techniques to keep training fresh and relevant.
To review your users' performance, navigate to the "Attack Simulation Training" menu. From there, select "Simulations," then click on the name of a specific simulation. This will provide detailed insights into how your users engaged with the simulation and their responses.
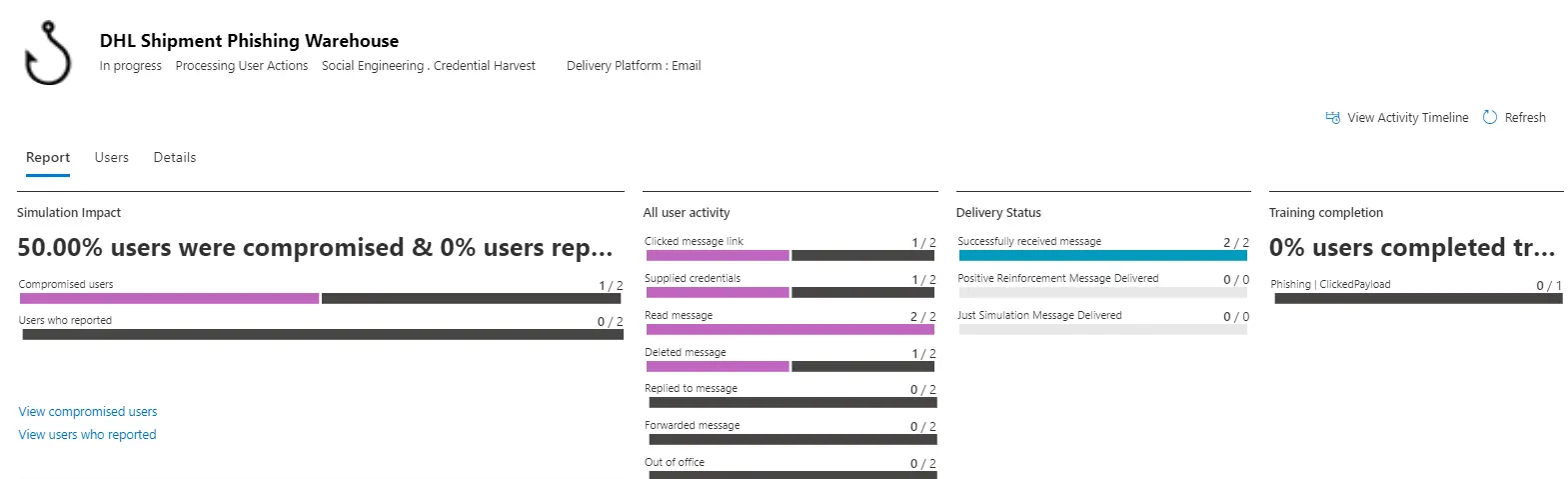
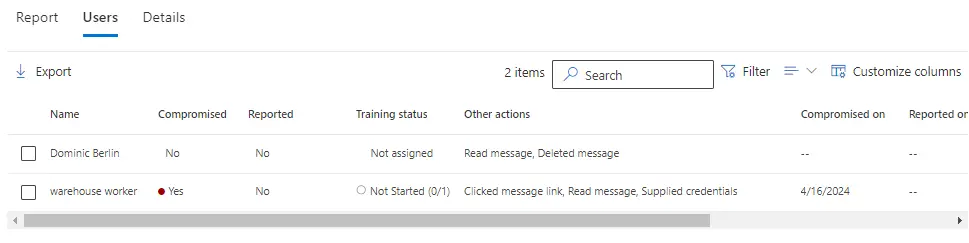
You can view each user's actions, including whether they deleted the message, clicked on the payload, or entered their credentials on the fake login page. This granular insight allows you to assess individual user behaviors and tailor training accordingly.
Implementing security controls
Implementing multiple technical security controls through Defender for Office 365 is crucial in mitigating BEC scams effectively. These controls include connection filtering, anti-malware policies, anti-phishing policies and more.
This layered approach is paramount as it enables the organization to address a diverse array of adversary techniques associated with phishing (T1566). By deploying multiple defenses, organizations can bolster their resilience against evolving threats and enhance overall security posture.
Email Authentication (Anti-Spoofing)
Email authentication plays a crucial role as an anti-spoofing measure, and setting up SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) are the initial steps organizations should take to prevent malicious actors from spoofing their domains and impersonating users.
By implementing these measures, organizations not only protect their own systems and data but also contribute to safeguarding their reputation.
SPF allows domain owners to specify which mail servers are authorized to send emails on behalf of their domain. When an email is received, the recipient's email server can check if the sending server is listed in the SPF record for the sender's domain. If not, it might flag the email as suspicious. However, SPF only validates the envelope sender, not the actual content of the email.
DKIM adds a digital signature to emails using a private key associated with the sending domain. The recipient's email server can then verify this signature using the public key published in the sender's DNS records. DKIM ensures that the email content hasn't been tampered with and that it genuinely originated from the claimed domain.
To add custom domains to your Microsoft 365 (formerly Office 365) tenant and set up the relevant DNS records such as SPF (TXT) and DKIM (CNAME), follow these steps:
- Go to admin.microsoft.com.
- Navigate to "Settings" and then select "Domains."
- Choose the custom domain you want to manage.
- Look for the option to "Manage DNS," which will guide you through the necessary steps to create both the SPF and DKIM records.
- These records need to be added to you DNS hosting service so the exact procedure of adding these records varies.
After configuring the SPF and DKIM records within your DNS hosting console, it's crucial to validate that all records are correct. Here's an example from our demo tenant:
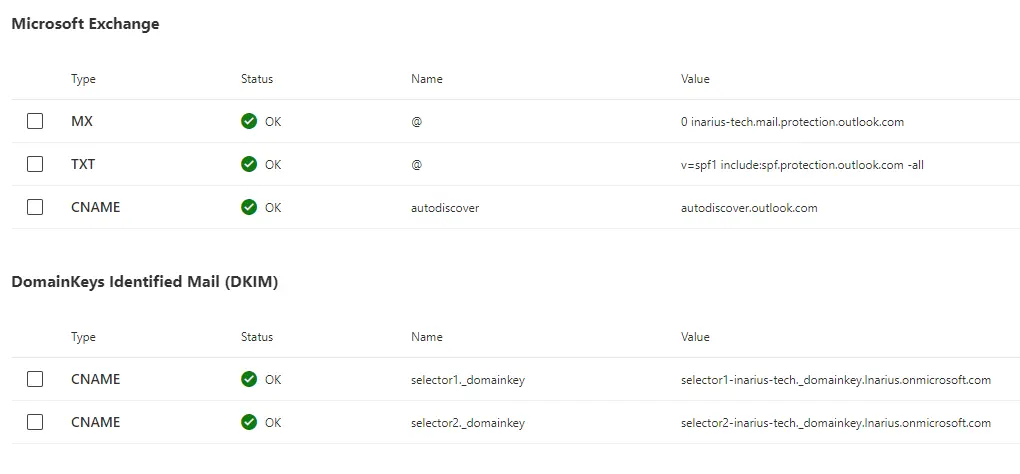
To sign outbound email messages for your domains, follow these steps:
- Navigate to the Defender portal.
- Go to "Policies & rules" and then select "Threat policies."
- Locate and click on "Email authentication settings."
- Within the Email authentication settings, navigate to the "DKIM" tab.
- Select your custom domain from the list of domains.
- Enable the option specified for DKIM settings. This option may involve enabling DKIM signing for your domain or configuring other DKIM-related settings as required.
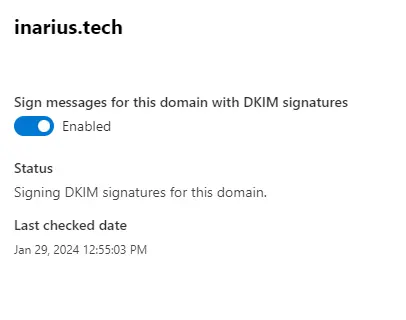
While SPF and DKIM are essential for email authentication, DMARC fills several critical gaps compared to relying solely on SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail).
DMARC also performs alignment checks between the domain found in the SMTP envelope (also known as the "MAIL FROM" or "Return-Path" domain) and the domain found in the "From" header of the email message. You can implement policy enforcement by specifying how Exchange online should handle messages that fail SPF or DKIM alignment.
DMARC can also provide domain owners with detailed reports on email authentication results, including information on which emails pass or fail SPF and DKIM checks. These reports offer valuable insights into unauthorized use of their domain and can help identify sources of phishing attacks. This visibility enables organizations to take proactive measures to secure their email infrastructure and mitigate risks effectively.
Instructions on how to set this up in Microsoft 365 can be found here:
Configuring threat policies
Microsoft offers preset security policies to configure anti-spam, anti-malware, and anti-phishing measures according to their best practices. This allows organizations to quickly implement a broad range of settings. A common scenario is to enable the standard preset policy for all users, and then enable strict security for more sensitive mailboxes such as your executives or people handling financial transactions for example. When both policies are enabled, the strict settings always win.
The actual policy settings in these presets are documented here:
Defender for Office 365 also includes features such as Safe Links and Safe Attachments. Defender for Office 365's Safe Links feature can help protect against spearphishing links by scanning URLs in emails and blocking access to known malicious websites. Both these features are activated when you enable the preset security policies.
You can of course create custom policies for each of the above-mentioned features but do know that the preset policies take precedence if the user, group, or domain is targeted in multiple policies.
For instance, the configuration to honor the DMARC policy for inbound email messages can be set within a custom anti-phishing policy.
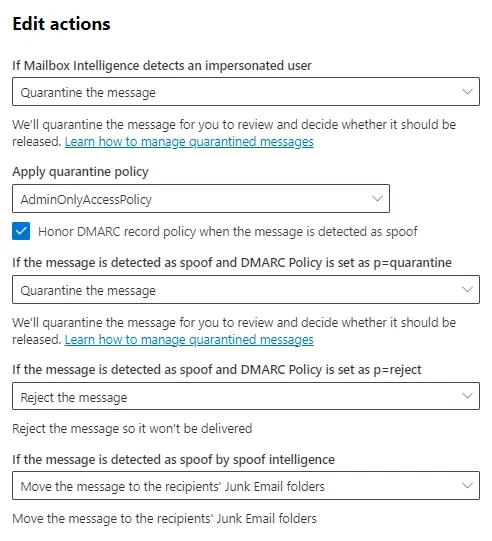
Spoof intelligence is another feature that is part of the anti-phishing policy, capable of detecting implicit failures. This means that a message can be detected as spoofed even if it has passed the DMARC policy.
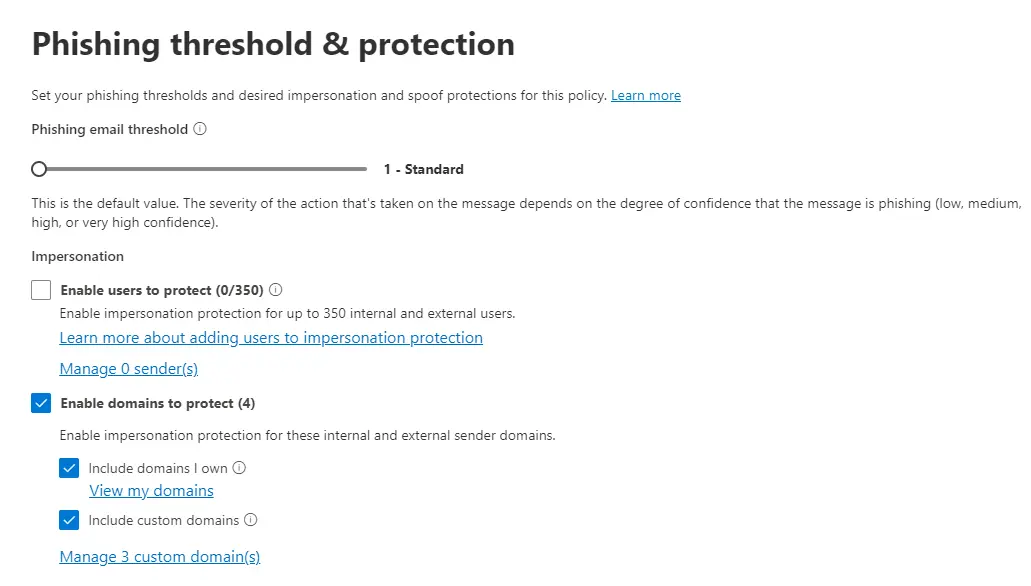
In phishing scams, attackers often attempt to impersonate trusted entities such as financial institutions, e-commerce platforms, government agencies, and other reputable organizations. Impersonation protection can detect email addresses or domains that are similar to legitimate ones.
In the Standard or Strict preset security policies, your owned domains are automatically covered by impersonation protection, while users or custom domains requiring this safeguard must be explicitly specified.
A good exercise is to list the domains of key suppliers and partners that fall under these categories and add them to the list of protected domains under the impersonation protection feature.
To configure impersonation protection within Defender for Office 365, follow these steps:
- Log in to the Microsoft Defender portal.
- From the dashboard or the left-hand navigation menu, locate “Policies & Rules” and select “Threat policies”.
- Create a custom Anti-Phishing Policy
- Within the anti-phishing policy settings, look for the section related to impersonation protection.
- Depending on your organization's requirements, customize the impersonation protection settings.
- Once you've configured the impersonation protection settings to your satisfaction, save your changes to apply the policy.
Regularly monitor the effectiveness of your impersonation protection settings and adjust them as necessary based on feedback, insights from threat intelligence, and evolving security requirements.
The Threat Within
Protecting your organization against phishing and other social engineering techniques originating from outside your environment is one thing, but Business Email Compromise (BEC) scams often leverage compromised accounts to achieve their objectives. By gaining access to legitimate email accounts, attackers can monitor internal communications, gather intelligence, and identify potential targets and opportunities for financial fraud. They may then impersonate executives, vendors, or business partners, requesting urgent wire transfers, changes to payment details, or sensitive information.
Conditional access policies
Entra ID conditional access provides a powerful set of controls and policies to secure identities and accounts within your organization which help to mitigate risks associated with various attack techniques, including valid accounts (T1562).
Two conditional access policies that are pertinent to business email compromise (BEC) scams are implementing MFA for all users when they access their applications and disabling legacy authentication. Both can be implemented by starting from a policy template when accessing the Entra ID portal.
Legacy authentication refers to older methods of authentication that rely on protocols such as Basic Authentication, NTLM, and POP3/IMAP, which do not support modern authentication mechanisms like OAuth 2.0. These legacy protocols often require users to enter their username and password directly into applications or services to authenticate.
Limiting Oauth Consent
Consent refers to granting authorization to an application to access protected resources on behalf of users. Administrators or users may be prompted to provide consent for accessing their organization's or individual's data, such as their Exchange Online mailbox. However, attackers can exploit this process by deploying malicious apps to request permissions, potentially gaining access to a user's mailbox. This unauthorized access enables them to send fraudulent emails from within the organization, bypassing crucial security controls.
Make sure that you limit the permissions for which a user can consent without administrator approval and regularly monitor these applications and the permissions that they have.

One approach is to restrict users' ability to consent to apps only from verified publishers, and only for permissions deemed to have low impact. For additional details, refer to Microsoft's documentation. Configure how users consent to applications.
5. How can Orange Cyberdefense help you?
While the mitigations mentioned in this article are by no means exhaustive, by prioritizing these versatile controls, organizations can establish strong foundational defenses against a wide range of cyber threats including business email compromise (BEC) scams. By addressing common attack vectors, we can maximize the impact of our security efforts.
However, setting up these controls is one thing, maintaining them is another which is why Orange Cyberdefense offers pro-active services to help customers improve and maintain their security posture.
- The Microsoft 365 Security Assessment service offers a comprehensive analysis to identify potentially risky or insecure configuration settings. By increasing visibility into the organization's exposure and vulnerabilities to Microsoft 365 threats, it enables proactive awareness of security challenges.
- Orange Cyberdefense also delivers upon a great number of Microsoft Security workshops with the aim of illustrating how to put next-generation Microsoft Security tools to work for you in the mitigation of threats, including Business E-mail Compromise (BEC).
- Managed Workspace Protection for Microsoft Defender XDR is a managed security service provided by the Orange Cyberdefense Global SOC that provides continual security enhancement of the M365 workspace and operational management of the Microsoft Defender XDR Modules, so clients get the best of their Microsoft security technology investment.
In this blog post, we underscored the significance of the "protect" pillar within a comprehensive security framework. In part 2, we delve deeper into the detect and respond capabilities, leveraging solutions such as Microsoft Defender for Endpoint and Microsoft Defender for Office 365 within Microsoft Defender Extended Detection and Response (XDR). We'll illustrate how these tools play a pivotal role in combatting business email compromise scams.
