Exploring the muddy waters between ransomware and hacktivism

As ransomware tactics evolve and blend with other forms of attacks, the lines blur, driven by geopolitical tensions and an ecosystem in constant flux. Understanding these dynamics is essential for defense.
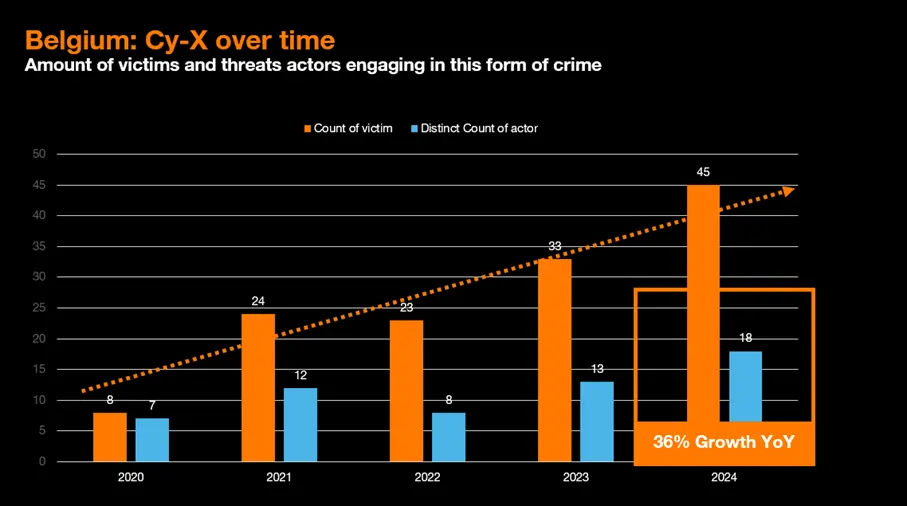
At the beginning of 2024, a renowned Belgian beer producer was hit by a ransomware attack. The incident was later claimed by Stormous, a notorious cyber extortion group and a member of a hacker collective known as The Five Families (after the infamous mafia gangs in New York).
We deliberately use the term Cyber Extortion (Cy-X) because ransomware no longer fully describes the scope of the issue. While ransomware has been around for ages, the concept of double extortion emerged a few years ago. Instead of merely encrypting data, attackers began stealing their victim’s data and threatening to expose it on self-developed leak sites. Today, cyber-attacks often skip the encrypting part altogether and directly launch an extortion campaign. Therefore, cyber extortion is now a more appropriate umbrella term that includes ransomware attacks.
Financial versus political motivation
When we think of ransomware, we usually picture a straightforward, linear attack where a hacker infiltrates and moves through the network, identifies valuable assets, and demands ransom. However, attacks are often more complex and dynamic, involving multiple actors with different roles. In Orange Cyberdefense's latest Cyber Extortion and Ransomware report called the CyXplorer, we observe a new disturbing trend where a victim’s stolen data is reposted multiple times and on various occasions. Our investigations uncovered over 400 occurrences of someone reposting, mostly on the same day but sometimes up to 3.5 years after the original leakage.
Speaking of our report, we have been collecting data on cyber extortion since 2020 – when most groups began setting up leak sites. While the pattern remained consistent in the initial years, it shifted in 2022 when the war against the Ukraine broke out. The reason? Despite many cyber extortion groups claiming to be solely financially motivated, they began taking political stances and aligning with one particular side in the conflict. It started when Conti, one of the most prolific groups, declared their support for Russia. Stormous, the group behind the attack on the Belgian beer producer, also allied with this pro-Russian actor .
Our latest Security Navigator report reveals that North America and Europe are impacted the most by Cy-X attacks. Since a few years now, we see so called “anti-targeting” patterns where threat actors pledge to not attack certain regions or countries.
These developments show how Cy-X and ransomware have become a political tool and cannot only be considered as purely financially motivated forms of crime. It suggests that the impact of politically motivated campaigns is increasing, which brings us to another term: hacktivism.
Modern hacktivism
Hacktivism as a word is derived from “activism”. It means that someone is campaigning for social or political change, while using technology and hacking techniques. To qualify as hacktivism, an attack must be politically motivated, online, and non-violent. As soon as someone accepts the risk to endanger human life, cause severe financial damage, or harm physical property, it crosses over into cyber terrorism.
When the war in Ukraine began, the local Minister of Digital Transformation called for a powerful IT army to fight against Russia. As mentioned before, many stakeholders, including cyber extortion groups, decided to choose sides in the conflict. Among them are some very familiar names. In the war against Ukraine, no less than 138 different groups were identified, while another 189 groups got involved in the Israeli-Palestine conflict. Rather than being hacktivists, these groups act as fronts for governments or other professional entities, responding directly to geopolitical events and aligning with government interests.
For the cybersecurity industry, the impact of these attacks is not measurable, unlike cyber-attacks on organizations that cause downtime and business disruptions. However, we should not underestimate the effects. One of the most active, pro-Russian hacktivist group that we continuously monitor, consistently targets entities on Russia’s unfriendly countries list, particularly those supporting Ukraine. Their attacks focus on government sites, public transportation, and other targets that score headlines.
Influencing public opinions
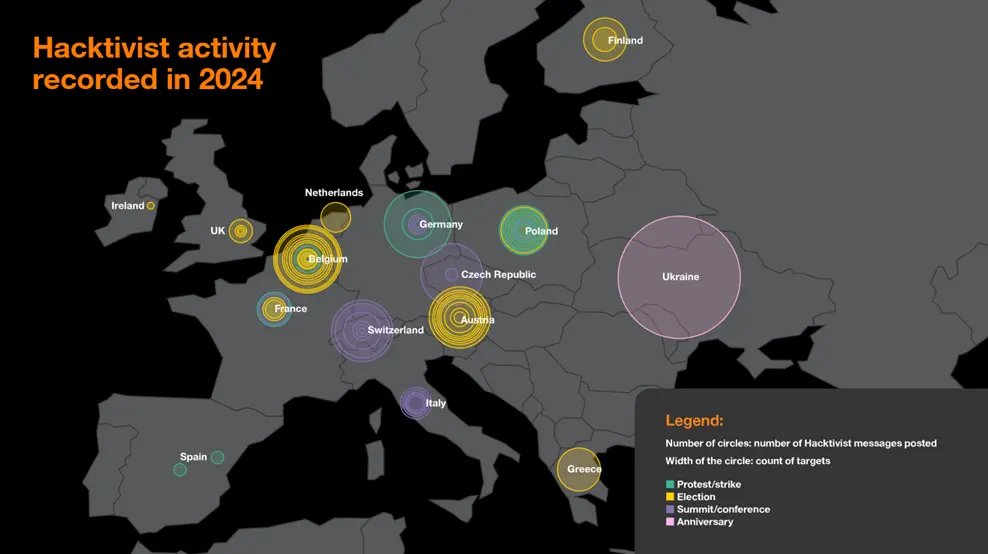
In our latest Security Navigator report, we analyzed over 6,000 so-called hacktivist attacks, using Distributed Denial of Service attacks to gain the public attention. Here we found that many of the attacks were strategically times, trying to erode trust and influence public opinions. As can be seen below, we created a map of all attacks in 2024 that matched keywords and thus campaigns communicated by the threat actors to disrupt locally held elections, conferences and summits or targeting countries’ local anniversaries and showing “presence”. We found that Belgium’s institutions, both from the public and private sector were attacked 87 times between August 2022 and August 2024.
What can we do?
In conclusion, the threat landscape is more complex than ever, especially as we see more cross-overs between financially and politically motivated threat actor groups. Information campaigns pose a real threat, but are even harder to detect and defend against. Fortunately, the techniques used by attackers (e.g. remote access, exploiting vulnerabilities, social engineering, etc.) have remained consistent over the years. This means organizations can make significant strides by addressing cyber security basics , such as creating regular backups and providing user awareness training, enabling multifactor authentication and introducing password complexity.
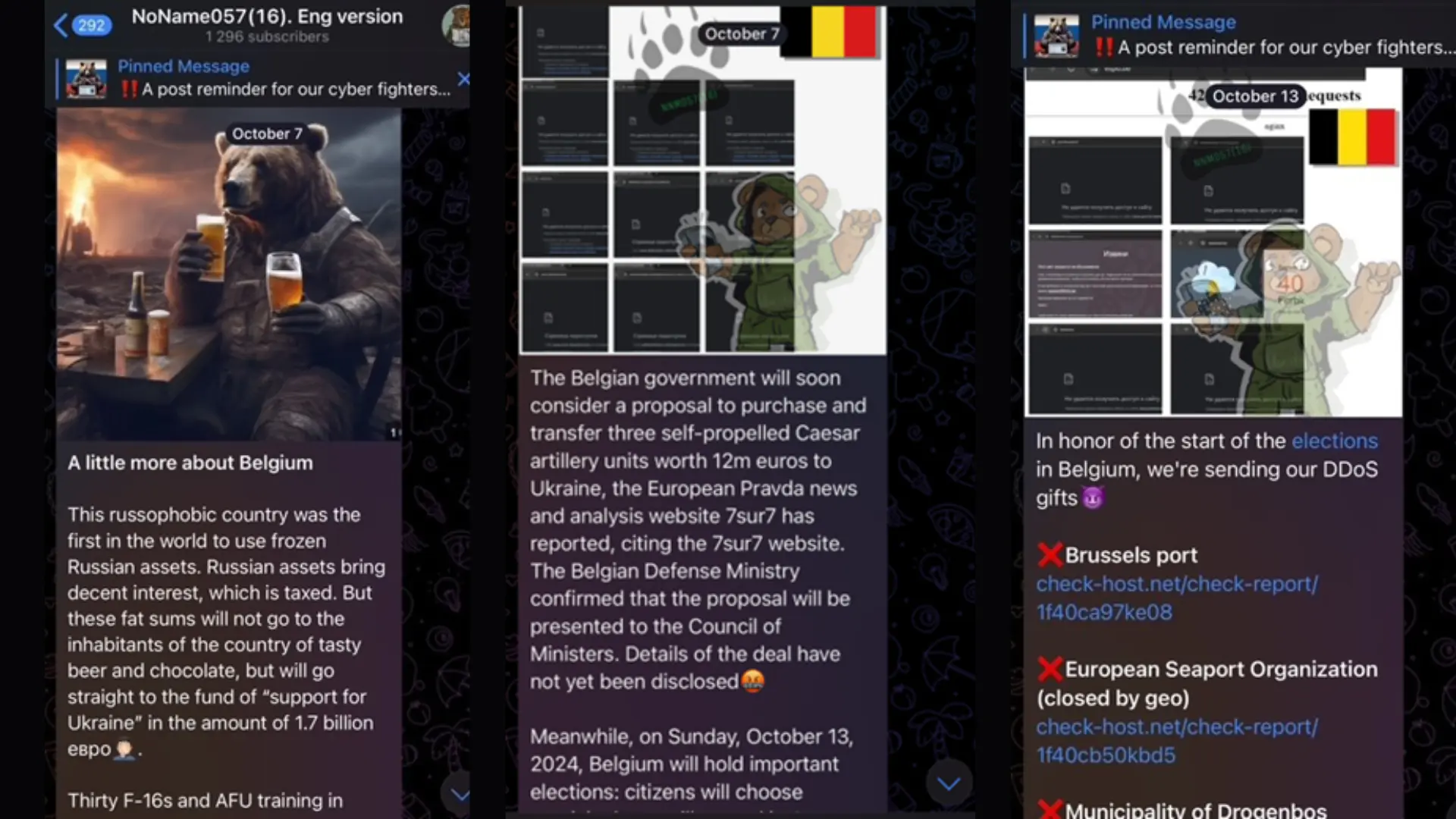
The attack on the Belgian beer brewer is not a one-time event. In fact, just a few days after the attack, a nearby coffee roaster was also hit by ransomware. Ultimately, we must hope for the best but prepare for the worst. Most cyber-crime is opportunistic, and targets victims based on variables such as their security posture, awareness, and insufficient cybersecurity practices. Even in this complex environment, getting the basics right will take you a long way.

