
Palo Alto Networks RedLock
Palo Alto Networks
Do you have a state-of-the-art firewall from Palo Alto Networks today?
In this rapidly-evolving technological world, it is crucial to check whether your firewall can still face current and future threats. Our Palo Alto experts have created a checklist with 7 items to help you protect your organization.
Go to the checklistPalo Alto Networks RedLock is a platform that offers comprehensive protection in multi-cloud IaaS and PaaS environments through API-based integration. It provides both compliance monitoring and security analytics.
Knowledge of all the built-in security controls specific to the various cloud service providers is a vast, almost unrealistic challenge for many companies. Redlock differs from other platforms on the market since it also reads event logs and can analyze them over a time interval.
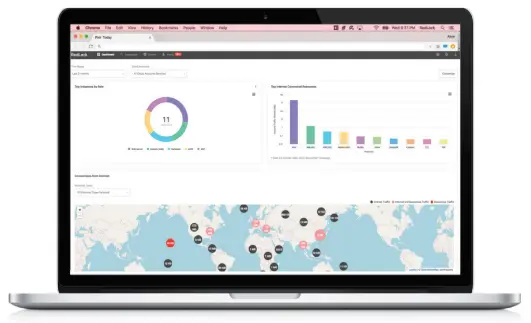
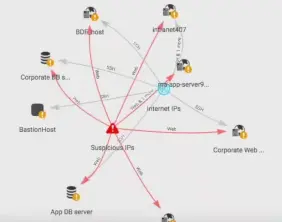
More information (and therefore context) leads to better decisions in the security policy. RedLock discovers dynamic changes that are made in public cloud environments such as AWS, Azure and GCP. It constantly collects information from the available sources of logs through these environments. Using machine learning, user activity logs, and configuration logs, traffic logs are correlated and enriched with threat intelligence and vulnerability feeds to form an overall picture of the risk you are running.
You will be informed about risky configurations, suspicious end-user activity, network breaches and exposed workloads (missing patches, unrestricted access, etc.).
Possible threats are arranged on an intuitive scale and shown through interactive diagrams. This means that the necessary priorities can be quickly established based on the severity of the threat. RedLock provides a dashboard that gives the security status and a compliance overview in real-time.

Is your Palo Alto Networks Firewall still Next Generation?

Is your firewall configured according to current security best practices?
Palo Alto Networks developed a Best Practice Assessment tool to verify this.
read more
Your Next-Generation firewall as Zero-Trust framework enabler?
How do you transfer your security policies to the cloud? Do you have a ‘single pane of glass’ for your entire perimeter?
Read More
Does your firewall already have an extension to the cloud?
Palo Alto Networks developed a Best Practice Assessment tool to verify this.
Read More
Is your firewall Artificially Intelligent?
Can you automatically detect whether your users or IoT devices have strange behavior? Do you know when your network undergoes a cyberattack?
Read More
Are all security functionalities active on your firewall?
Have you activated all software licenses?
Read More
Does your firewall support PAN-OS10.0 or higher?
Do you know the latest features for your Palo Alto Networks firewall? Can your Palo Alto Networks firewall support the latest PAN-OS version?
Read More
What information does your firewall have for your CISO?
Which questions from your CISO can you easily answer?
Read More
Cortex platform as the cornerstone for MicroSOC Managed Threat Detection & Response
Get the most out of your Cortex XDR platform by adding threat analysis and incident response services.
Read More