Pan-OS 10.0: Network features
Palo Alto networks
Do you have a state-of-the-art firewall from Palo Alto Networks today?
In this rapidly-evolving technological world, it is crucial to check whether your firewall can still face current and future threats. Our Palo Alto experts have created a checklist with 7 items to help you protect your organization.
OverviewClustering between more than 2 devices
Palo Alto Networks firewalls support sessions being synchronized across more than 2 device/clusters of Palo Alto Networks firewalls.
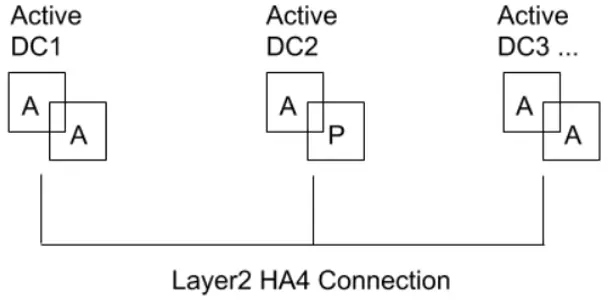
Multi datacenter failover
The goal is that in case a datacenter fails the sessions fail over to a different datacenter causing no impact.
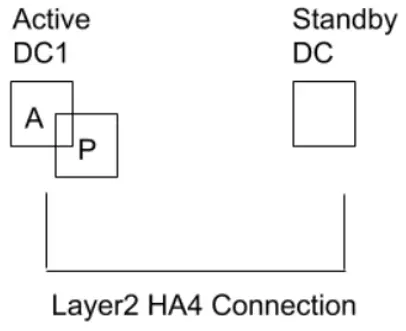
Active Passive datacenter failover
A different use case is where 2 datacenters are in active passive mode. In case the active datacenter fails the passive datacenter can take over and sessions will not be interrupted.
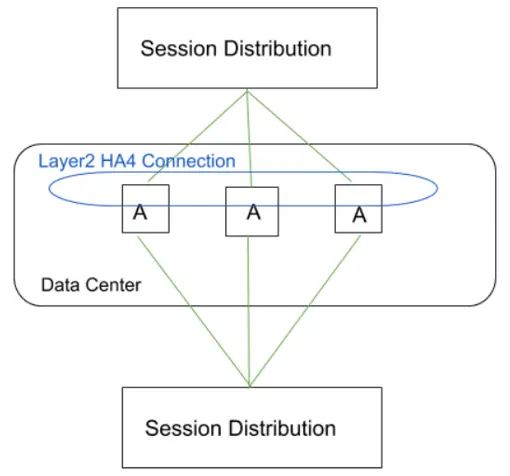
Horizontal scaling
In this scenario we want to have multiple devices in one datacenter to scale up the performance. Depending on the hardware type the total number of devices varies that can be used to scale. A requirement is to have a device that is distributing the sessions across the multiple Palo Alto Networks devices.
On the following Palo Alto Networks firewalls this feature is available:
- PA-3200 maximum of 6 devices in one cluster
- PA-5200 maximum of 16 devices in one cluster
- PA-7050 maximum of 6 devices in one cluster
- PA-7080 maximum of 4 devices in one cluster
- VM-300 maximum of 6 devices in one cluster
- VM-300 maximum of 6 devices in one cluster
- VM-700 maximum of 16 devices in one cluster
HA clustering for horizontal scaling of firewalls.