Top Cy-X Threat Actors impacting Germany in 2023 and how to defend against them

In this first part of the article, we look at the top 5 Cy-X threat actors that OCD identified for Germany in 2023. In addition to the ransomware used by these threat actors, we also look at the top tools used by at least top 3 Cy-X threat actors out of the top 5 Cy-X adversaries. Subsequently, recommendations for action are made for the top tools and the top MITRE ATT&CK techniques that result from the research, such as how to write robust detection and hardening recommendations for ransomware.
Just a short reminder why Cy-X. We propose to use the term ‘Cyber Extortion’, abbreviated to ‘Cy-X’ (pronounced ‘sigh ex’):
“Cy-X is a form of computer crime in which the security of a corporate digital asset (confidentiality, integrity or availability) is compromised and exploited in a threat of some form to extort a payment.”
The ultimate act of extortion involves the commitment of more than one crime, including the unauthorized access to computers and data on the one end of the spectrum, and the act of extorting a ransom near the other.
To emphasize the importance of our research we take also the latest information from German authorities like BSI. The BSI published the latest figures this October 2023 a view days ago. Ransomware groups continues to be the biggest threat to companies in Germany. According to the report, the BSI is aware of 68 successful ransomware attacks on companies, 15 of which were also directed against IT service providers. On average, 2 ransomware attacks on local governments or municipal operations were reported per month. Further OCD research results will be soon available in a detailed version in our current Security Navigator 2024.
In Germany, Orange Cyberdefense counts already 379 victims of Cy-X threat actors as of September 2023. If we look at the statistics for Germany in 2023, it quickly becomes clear why LockBit was classified as the most dangerous group by the BSI. With 25% of all attacks of the LockBit3 ransomware variant, LockBit is the lone leader, followed by Cl0p with 15%, Play 11%, as well as Royal with 8% and ALPHV (BlackCat with 5%). Not only are we seeing another increase in the number of victims, but we are also seeing a new record of 50 threat actors.
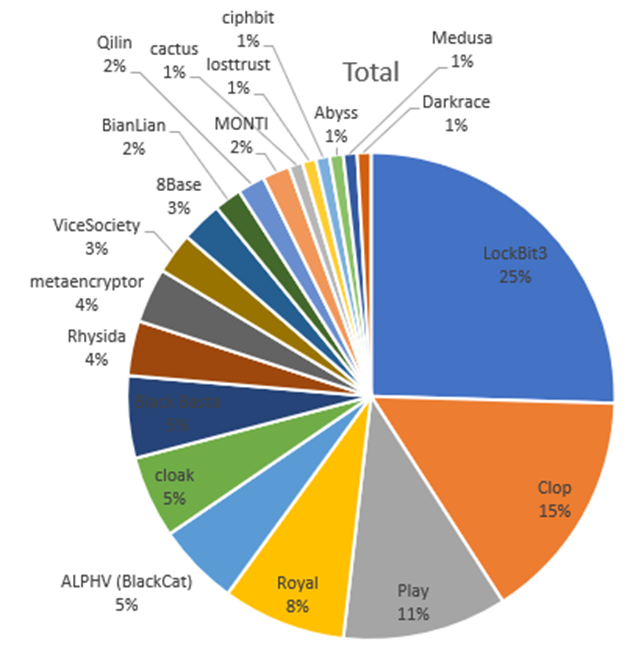
Top Cy-X groups for Germany 2023
In addition to the ransomware used and the associated MITRE ATT&CK techniques of the campaigns, we also look at the top tools that the attackers used and map them as well to understand their capabilities. The criterion for top tools is that at least 3 of the top 5 attackers must have used the software. This results in the following top tools for Cy-X groups for Germany in 2023:
· AdFind
· Cobalt Strike
· Any Desk
· Mimikatz
· Process Hacker
· PsExec
· Rclone
· SoftPerfect Network Scanner
In order to supplement the top 5 Cy-X threat actors as well as other relevant Cy-X threat actors in Germany in 2023, further ransomware software variants are added to the matrix. This results in 20 matrices of ransomware software from all relevant top adversaries and the above-mentioned top tools from the following Cy-X groups, which OCD is able to determine for Germany in 2023:
· Medusa
· Black Basta
· Rhysida
· LockBit 3.0
· Cl0p
· Play
· 8Base
· BianLian
· Royal

If we look at the matrix as showed above, we now have an overview of all top MITRE ATT&CK techniques for the Cy-X groups. Here, it is mainly a matter of understanding that the threat actors could use certain MITRE ATT&CK techniques more frequently (prevalence of techniques) in combination with their capabilities, means their top tools. This is correlated with the actual data and clear indicator for successful attacks. It is especially helpful to multilayer tools and ransomware if you are not sure if the MITRE ATT&CK technique is the right one you’ve chosen during your reaseach process. It ensures that you avoid analytical errors and possibly not overlook, misinterpret or even choose the wrong TTPs because of lacking technical understanding or missing information. In addition, one is often biased with regard to attack patterns and adversarial behavior. Multilayering thus compensates for analytical errors.
Top MITRE ATT&CK Cy-X threat actors used in 2023
T1133 External Remote Services and T1078.002 Domain Accounts are the most common Initial Access MITRE ATT&CK techniques for the top Cy-X threat actors for Germany in 2023
For the tactic execution, we see clear peaks at:

For persistence and privilege escalation, we see T1543.003 Windows Service and T1569.002 Service Execution another two important technique that Cy-X groups use.
When it comes to defense evasion, there are a few techniques that are important to consider:
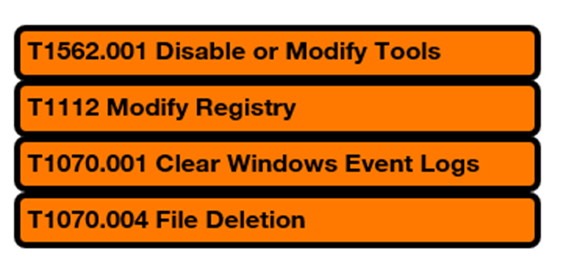
To understand defense evasion and how to disable or modify tools, please read my blog article about ransomware & data extortion landscape.
At Credential Access one of the top techniques that we seen for Cy-X groups as well as for APTs is once again the T1003.001 LSASS Memory.
If you want to detect Cy-X groups in time before they move laterally, you should pay specific attention to the following discovery techniques:
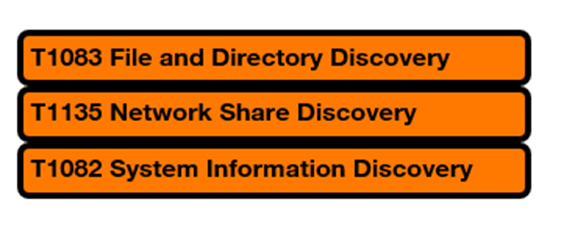
For lateral movement, the adversaries prefer T1021.002 SMB/Windows Admin Shares.
Top Command & Control techniques are T1105 Ingress Tool Transfer followed by T1071 Application Layer Protocol and here specifically the Web Protocols T1071.001.
Exfiltration is usually done via T1567.002 Exfiltration to Cloud Storage but could vary.
With the Impact, you can see similar behaviors to those of wipers. Before the system is encrypted — T1486 Data Encrypted for Impact, the Volume Shadow Copy is usually deleted — T1490 Inhibit System Recovery and one or more services have been stopped — T1489 Service Stop.
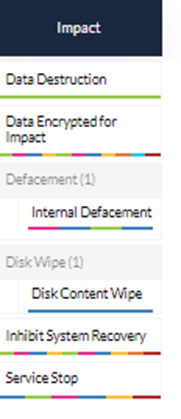
Depending on the ransomware, some threat actors use for the encryption the safe mode boot - T1562.009 like Cy-X threat actors LockBit3.0, Snatch, Black Basta or Medusa, mainly to prevent detection.
Recommendations to take action from the top tools and TTPs mentioned above
Let’s start with the tools. As we have seen, Cy-X groups are specialized in T1133 in External Remote Services and T1219 Remote Access Software (RMM Tools) such as Any Desk.
Any Desk
Any Desk can be tested both the installation and the execution with Atomic Red Team with the Atomic Test #2 — AnyDesk Files Detected Test on Windows.
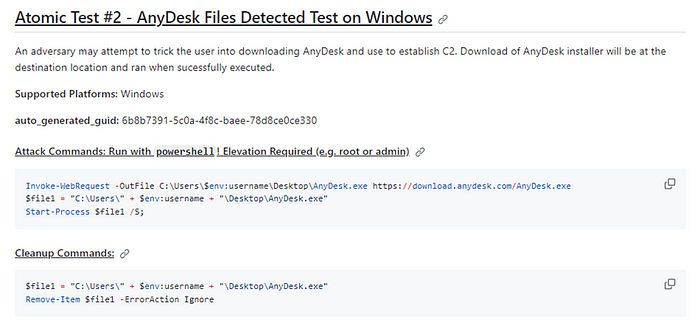
An adversary may attempt to trick the user into downloading AnyDesk and use to establish C2. Download of AnyDesk installer will be at the destination location and ran when successfully executed.
Invoke-WebRequest -OutFile C:\Users\$env:username\Desktop\AnyDesk.exe https://download.anydesk.com/AnyDesk.exe
$file 1 = “C:\Users\” + $env:username + “\Desktop\AnyDesk.exe”
Start-Process $file 1 /S;
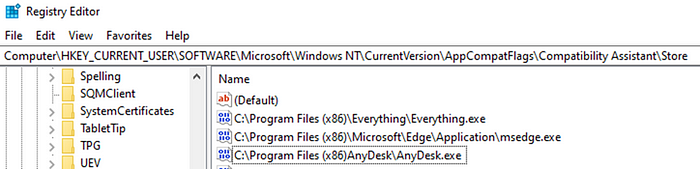
I definitely recommend testing AnyDesk with your own telemetry to create robust detection. For example, during testing, I found that a specific name PIPE creation for /adprinterpipe shows up in the telemetry during installation, which can be uniquely mapped to AnyDesk. Furthermore, specific registry entries are created and parameters with AnyDesk appear in the command line.

The registry key shows just one artifact in the current version directory as an example. If you don’t have the resources to test the behavior in your own environment, you can also get more information from Virus Total about the paths and artifacts for AnyDesk. In the Active Summary for e.g, the Sigma rule for Remote Access Tool is suggested with “AnyDesk Execution From Suspicious Folder”.
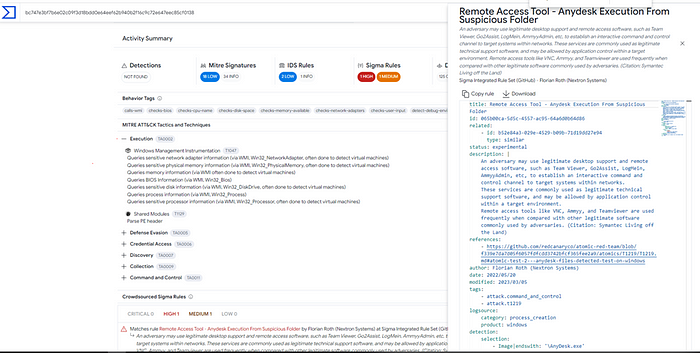
For the installation itself, there are already pre-built Sigma rules for AnyDesk like the one for silent installation:

And here you can see the telemetry for the test installation with Sysmon EID 1 (executed with Atomic Red Team)
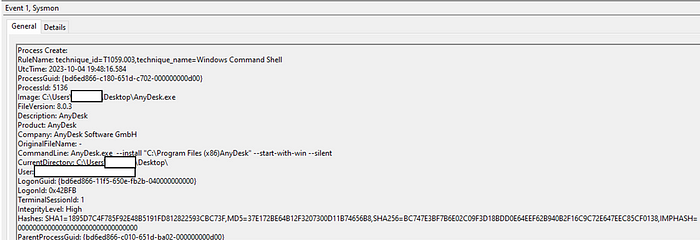
If you translate recommended Sigma rules from VT with SOC Prime uncoder.ai, you can start threat hunting right away depending which security tool you’ve got in your environment.
Another recommended Sigma Rule for T1219 would also be “DNS Query To Remote Access Software Domain” and highly recommended for threat hunting (all relevant RMM tools in the wild):
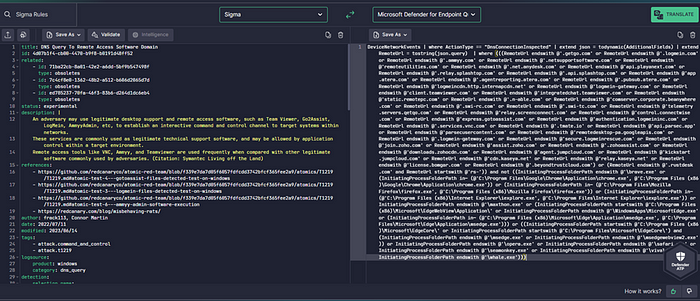
To learn more about RMM tools used by Cy-X threat actors, you find a great research presentation with the title “analysis on legit tools abused in human operated ransomware” from Trend Micro here.
Cobalt Strike
Cobalt Strike is still a popular hacking tool for attackers. If you want to find direct system calls from Cobalt Strike BOFs 0xFF14, I recommend the article by Giijs Holestelle from FalconForce and the corresponding FalconForce GitHub repository. The article explains which APIs Cobalt Strike abuses and how to detect such system calls with Sysmon.
Additionally Atomic Red Team has 5 tests for Cobalt Strike within the MITRE ATT&CK technique T1559.
Corresponding IOCs can also be analyzed and detected in Sysmon. It is recommended to write a rule group in Sysmon related to the PIPEs and MITRE ATT&CK techniques like showed above.
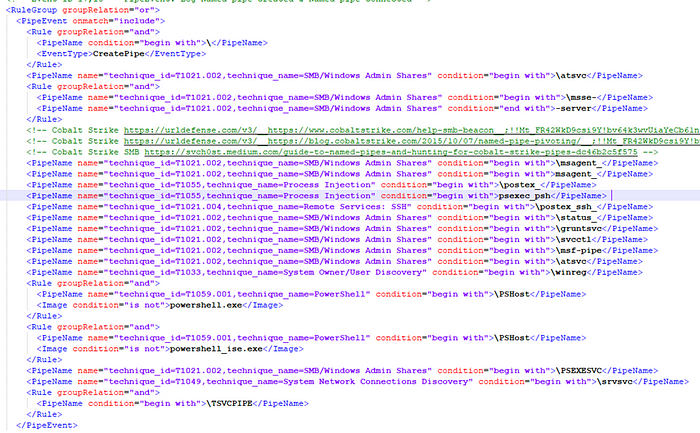
And to hunt with Florian Roth’s CobaltStrike Named Pipe Sigma Rule, you can approve your test and try to find :
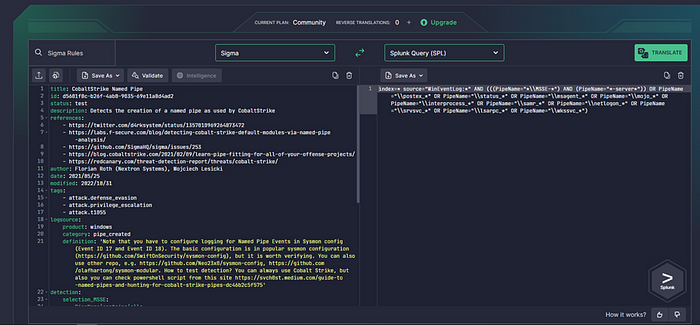
In addition, A detailed Defender’s Guide was published by the legendary team of The DFIR Report.
Adfind
AdFind is a free command-line query tool that can be used for gathering information from Active Directory. There are 5 different MITRE ATT&CK techniques that AdFind can be assigned to:
AdFind can enumerate domain users.
AdFind can enumerate domain groups.
AdFind can gather information about organizational units (OUs) and domain trusts from Active Directory.
AdFind has the ability to query Active Directory for computers.
T1016 System Network Configuration Discovery
AdFind can extract subnet information from Active Directory.
Cy-X groups like Play have got the AdFind tool in their discovery playbook like shown in the attack flow below.
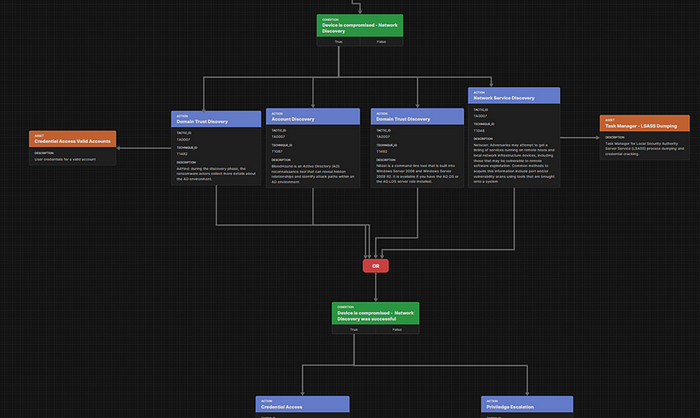
To detect AdFind, we recommend the Sigma rule for remote system discovery “PUA -AdFind Supsicious Execution”, which detects several flags:

More valuable information about detection suggestions can be found from Red Canary in the 2023 Threat Detection Report here: https://redcanary.com/threat-detection-report/techniques/domain-trust-discovery/
PsExec
I have already written a detailed article about PsExec, which can be found on Medium at my summiting the pyramid article.
PsExec is a free Microsoft tool that can be used to execute a program on another computer. It is used by IT administrators and attackers.
As an S0029 tool stored in the MITRE ATT&CK, you can mainly assign five MITRE ATT&CK techniques to the software:
T1136.002 Create Account: Domain Account
PsExec has the ability to remotely create accounts on target systems.
T1543.003 Create or Modify System Process: Windows Service
PsExec can leverage Windows services to escalate privileges from administrator to SYSTEM with the -s argument.
T1570 Lateral Tool Transfer
PsExec can be used to download or upload a file over a network share.
T1021.002 Remote Services: SMB/Windows Admin Shares
PsExec, a tool that has been used by adversaries, writes programs to the ADMIN$ network share to execute commands on remote systems.
T1569.002 System Services: Service Execution
Microsoft Sysinternals PsExec is a popular administration tool that can be used to execute binaries on remote systems using a temporary Windows service.
Cy-X groups predominantly use PsExec to deploy the ransomware. How, for example, LockBit did it with the batch file 123.bat and was described in my article on defense evasion techniques of ransomware groups.
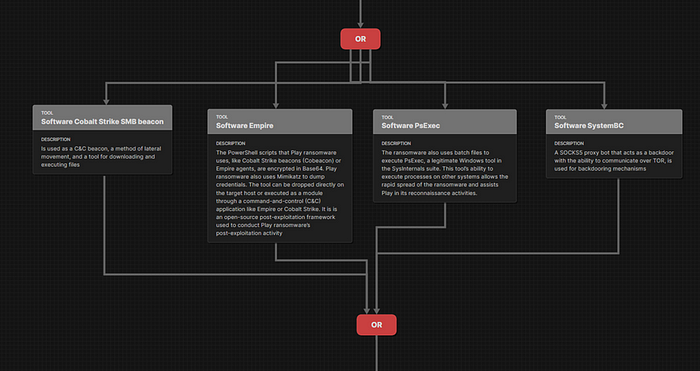
You can abuse the Sysinternals tool to move laterally. Since you can upload and download files with PSExec, it is definitely recommended to monitor the tool and create corresponding detections. A very good starting point for threat hunting is Cyborg Securities HUNTER with the following LOLBAS query:
This package utilizes a list of commonly abused LOLBAS which an attacker or malware would execute in quick succession. The presence of multiple executions of the programs within the list can be indicative of an infection or malicious activity occurring on a victim host. To reduce false positives, distinct counts per process name can be utilized to ensure over 5 unique processes from the list were executed versus just checking more than 6 events were generated on the host.
Another recommended Sigma rule is the PSExec Remote Execution File Artifact Sigma rule, which specifically detects when a PSExec command has been executed.
selection: TargetFilename|startswith: C:\Windows\PSEXEC- TargetFilename|endswith: .keycondition: selection
Rclone
Once the threat actors have turned their attention to the systems they are interested in, they collect the data present on them and try to filter it out of the victim environment using utilities such as Rclone, WinSCP, and FileZilla.
Rclone is used to exfiltrate the data towards “MEGA” cloud storage services. Detailed documentation on how to detect ransomware groups is available from The DFIR Report with an example as follows:

Red Canary has also dealt in detail in an article “Rclone Wars” and explains the software as well as the detection advantages resulting from the analysis.
Essentially, when executing Rclones from the command line of PowerShell, here’s how to hunt in Microsoft Defender for Endpoint:
DeviceProcessEvents | where ((InitiatingProcessVersionInfoFileDescription =~ @’Rsync for cloud storage’ or ProcessVersionInfoFileDescription =~ @’Rsync for cloud storage’) or (ProcessCommandLine contains @’ — config ‘ and ProcessCommandLine contains @’ — no-check-certificate ‘ and ProcessCommandLine contains @’ copy ‘) or (FolderPath endswith @’\rclone.exe’ and (ProcessCommandLine contains @’mega’ or ProcessCommandLine contains @’pcloud’ or ProcessCommandLine contains @’ftp’ or ProcessCommandLine contains @’ — progress’ or ProcessCommandLine contains @’ — ignore-existing’ or ProcessCommandLine contains @’ — auto-confirm’ or ProcessCommandLine contains @’ — transfers’ or ProcessCommandLine contains @’ — multi-thread-streams’)))
To test the exfiltration, the MITRE ATT&CK technique T1567.002 with the Atomic Test #1 — Exfiltrate data with rclone to cloud Storage — Mega (Windows) is recommended. This review also refers to the DfirReport, where you can find more helpful tips.
Mimikatz
If you look at the attacker profile of top Cy-X groups like LockBit, they mostly use Mimikatz in connection with the MITRE ATT&CK technique T1003.001 to gain access to LSASS. Here, access can then be detected via Ox1410 or 0x1010.
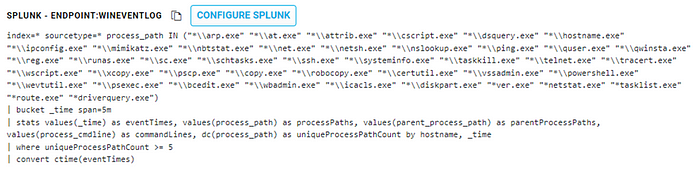
A corresponding query in Splunk might look like this:
index=* source=”WinEventLog:*” AND(TargetImage=”*\\lsass.exe” AND(GrantedAccess=”0x1410" OR GrantedAccess=”0x1010")) | table ComputerName,User,SourceImage
HUNTER from Cyborg Security once again offers an excellent starting point for further hunting packages, with which you can hunt for Cy-X groups in the Community Edition:
For example, with the Mimikatz Non-Interactive Execution
Cyborg Security | HUNTER
Edit description
Using the example of Crowdstrike EDR
(TERM(sekurlsa) OR TERM(kerberos) OR TERM(crypto) OR TERM(vault) OR TERM(lsadump)) (CommandLine IN (“*sekurlsa*” “*kerberos*” “*crypto*” “*vault*” “*lsadump*”) CommandLine=”*::*”)
| rename ComputerName as hostname CommandLine as proc_cmdLine ImageFileName as process RawProcessId_decimal as processId ParentBaseFileName as parentProcess ParentProcessId_decimal as parentProcessId
| stats min(_time) as firstSeen max(_time) as lastSeen list(process) as process list(processId) as processId list(parentProcess) as parentProcess list(parentProcessId) as parentProcessId values(proc_cmdLine) as proc_cmdLine by hostname
| convert ctime(*Seen)
Or in the premium Mimikatz Driver Installed.
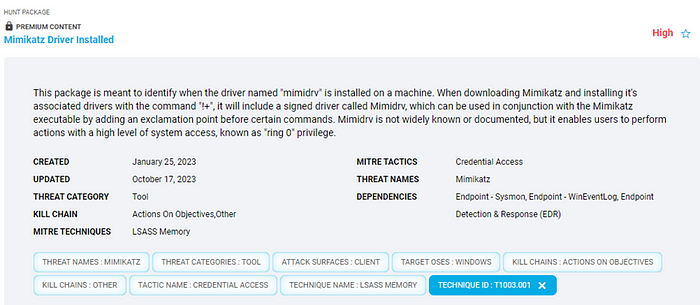
SoftPerfect Network Scanner
The SoftPerfect Network Scanner is often recommended for download as a PUA on various websites. The tool can ping computers, scan ports, recognizes shared folders, and provides information about network functionalities such as WMI, SNMP, etc. Such tools should not have users, only administrators on their machines. If normal users use this application, the incident responder should definitely ask why the tool is executed on the device, as it is potentially also an invitation for any top attacker to abuse the application. To find suspicious use of the software check for netscan.exe or the remote url www.softperfect.com and if the tool is targeting ports like 445 and 3389 like in seen with the use of Qakbot the initiating parent process would be explorer.exe and the command line would contain netscan.exe the local port and a remote port like 445, 3389 and 2179. Additionally, periodic requests to api.ipify.org were observerd throughout the instrusion by the SysWOW64\Explorer process and by the ATERA agent (ATERA is another RMM tool that adversaries likely use to gain access to the victim’s systems). https://thedfirreport.com/2022/10/31/follina-exploit-leads-to-domain-compromise/
Process Hacker
In this case, too, the tool may be used legitimately. Here it should be clarified to what extent the application is needed. Since it is actually used for monitoring purposes, it can also be misused for hacking, which is why it is often also detected as RiskWare as by Malwarebytes. Process Hacker can be for e.g., abused to kill processes including AV and EDR applications.
Top MITRE ATT&CK Techniques and Curing Recommendations
Now that we have looked at the most common and successful software application and tools of the top Cy-X attackers for Germany in 2023; let’s focus on a few essential MITRE ATT&CK techniques and how we can harden them to prevent Cy-X attacks.
First of all, let’s summarize all the most important techniques of top Cy-X groups that stand out in particular for 2023 in Germany:
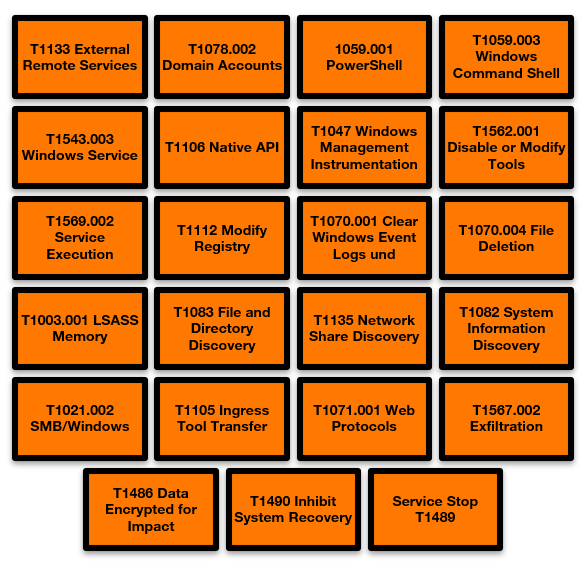
First of all, ask yourself how ransomware can be distributed on the devices in the first place. To get a better understanding, Mandiant for e.g., defines two key components that you can find in their Ransomware protection and containment strategies guide:
1. Manual distribution by a threat actor after they have infiltrated
Attackers are active in one environment and, by and large, have administrator-level permissions throughout the environment:
• Run encryption programs manually on the target systems.
• Deploy throughout the environment using Windows encryption programs
Batch files (provide C$ shares, copy and run the encryptor). ready with the Microsoft PsExec tool.
• Deploy encryption programs using Microsoft Group Policy Objects (GPOs).
• Deploy encryption programs with existing software deployment tools that
used by the victims’ organisation.
2. Automated dissemination:
• Extraction of credentials or Windows tokens from disk or storage.
• Trust relationships between systems — and use methods such as Windows Management Instrumentation (WMI), SMB, or PsExec to bind to systems and execute payloads.
• Unpatched exploitation methods
Remote Services and Lateral Movement
Let’s start with T1021.002 and T1047 in the context of lateral movement.
In order to successfully prevent lateral movement, firewall rules already help. Mandiant recommends that all specific applications that may require inbound connectivity to end-user endpoints should have an on-premises firewall policy configured with specific IP address exceptions for origin systems that are authorized to initiate inbound connections to such devices.
Here is an overview of the recommendation for hardening your remote services with specific Windows firewall rules for SMB, RDP and WMI.
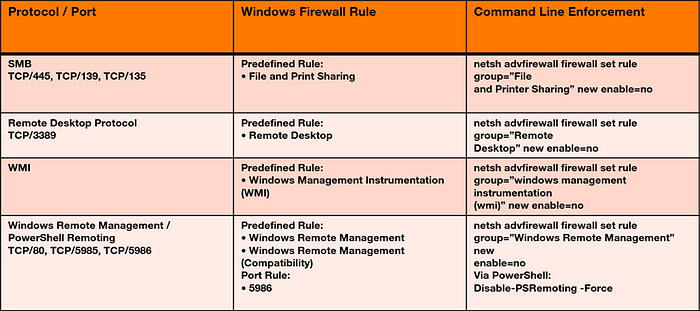
If you can’t disable RDP, you should be able to detect port tampering, for example if an attacker changes port 3389. Furthermore, you should be careful not to configure any RDP ports for the cloud with any any. This is an invitation for any attacker to access the virtual machine via bruforce password spraying.
If your detection is alerting adequately, you can test executing the following Atomic Red Team test:

In addition to Multi-Factor Authentication (MFA), connections should only be allowed with Network Level Authentication.
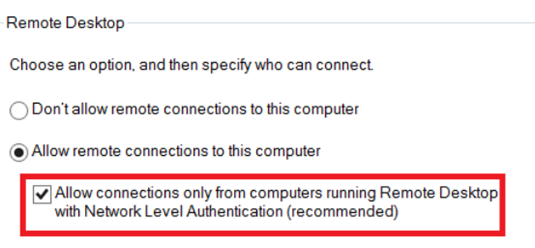
Mandiant also recommends requesting user authentication for remote connections using network-level authentication.
To prevent hidden shares, you can make the following changes for workstation:
HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters DWORD Name=”AutoShareWks” Value=”0"
And for server:
HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters DWORD Name=”AutoShareServer” Value=”0"
For the purpose of detection, there are now many events to detect the misuse of SMB Windows Share. Here, for example, you can detect on EventID 5145 file creation admin shares and hunt as follows (Splunk Query):
Look for SMB non-system accounts that access a file using an administrative share (for example, C$) with a write access mask (0x2):
index=Windows* source=”WinEventLog:Security” AND ((EventCode=”5145" AND ShareName=”*C$” AND AccessMask=”0x2") AND NOT SubjectUserName=”*$”)
Metasploit would be recognized for SMB as follows with Event ID 4625 and 4624 With Logon Type 3 as well as NTLM and EventID 4776:
SecurityEvent | extend LogonType = iif(isempty(LogonType) and EventData contains “LogonType”, extract(@’LogonType”>(.*?) <’, 1, EventData), LogonType) | extend AuthenticationPackageName = iif(isempty(AuthenticationPackageName) and EventData contains “AuthenticationPackageName”, extract(@’AuthenticationPackageName”>(.*?) <’, 1, EventData), AuthenticationPackageName) | extend WorkstationName = iif(isempty(WorkstationName) and EventData contains “WorkstationName”, extract(@’WorkstationName”>(.*?) <’, 1, EventData), WorkstationName) | extend ProcessName = iif(isempty(ProcessName) and EventData contains “ProcessName”, extract(@’ProcessName”>(.*?) <’, 1, EventData), ProcessName) | extend Workstation = iif(isempty(Workstation) and EventData contains “Workstation”, extract(@’Workstation”>(.*?) <’, 1, EventData), Workstation) | where ((EventID in (4625, 4624) and LogonType == 3 and AuthenticationPackageName =~ @’NTLM’ and (WorkstationName matches regex @’(?i)^[A-Za-z0–9]{16}$’)) or (isempty(ProcessName) and EventID == 4776 and (Workstation matches regex @’(?i)^[A-Za-z0–9]{16}$’)))
Furthermore, you should think about to disable SMBv1 on clients or server. You can do this on the one hand, in the registry and on the other hand, in the Group Policy. For this, I recommend following Mandiant’s hardening guidance on pages 13 and 14.
Windows Management Instrumentation and Remote Services
The Windows Remote Management is part of the Window Management Instrumentation as well as PowerShell Remoting. If you do not want to use PowerShell Remoting, it should be disabled according to the Disable-PSRemoting -Force. If you don’t want Windows Remote Management at all, you can disable it using the Stop-Service WinRM -PassThruSet-Service WinRM -StartupType Disabled. If you want to prevent connections over port 80, you can do so with the following command:
Set-NetFirewallRule -DisplayName ‘Windows Remote Management (HTTP-In)’ -Enabled False
If you want to test your optimized security controls, it is recommended to test it with Atomic Red Team performing test #1 to #4 for MITRE ATT&CK technique T1021.002.
Additionally you can benefit of the latest ATT&CK BZAR project uses the Bro/Zeek Network Security Monitor to detect ATT&CK-based adversarial activity.
The BZAR project uses the Bro/Zeek Network Security Monitor to detect ATT&CK-based adversarial activity.
MITRE ATT&CK is a publicly-available, curated knowledge base for cyber adversary behavior, reflecting the various phases of the adversary lifecycle and the platforms they are known to target. The ATT&CK model includes behaviors of numerous threats groups.
BZAR is a set of Bro/Zeek scripts utilizing the SMB and DCE-RPC protocol analyzers and the File Extraction Framework to detect ATT&CK-like activity, raise notices, and write to the Notice Log.
In the second part of my article about top Cy-X groups in Germany, we will look at further MITRE ATT&CK techniques and give you hardening recommendations, as well as ways to simulate and emulate attacks with the goal to write robust detection.
