Cyber war against Ukraine: Observations and recommendations.

What you should do. What we are doing
Updated 3rd March 2022
Following on from the initial leak of chat log data from the Conti Cy-X operation by the Twitter user @ContiLeaks, further data has continued to be leaked. The latest releases could prove to be a treasure trove for security analysts as they contain Conti’s source code along with a large amount of information including further chat logs, malware, victim information and their modus operandi. We currently have a team of experts analyzing the data; however, this will likely take several days due to the volume of information.
The French cybersecurity agency ANSSI has updated their recommendations, which now include advice recommending organizations to start thinking about replacing any Russian cybersecurity solutions, as it is anticipated they may be unable to maintain their products at the required security levels in the future. One such vendor mentioned is obviously Kaspersky, which has tried hard to remain neutral since the conflict escalated.
Proofpoint has released details of a phishing attack dropping a Trojan, dubbed “SunSeed” targeting a European government official working on the Ukrainian refugee’s issue. It is presumed the threat actors responsible are the Belarusian groups Ghostwriter and/or UNC1151.
ESET researchers have reported that wiper attacks continue to be seen with a basic worm component called “HermeticWizard” detected which attempts to deploy the “HermeticWiper” within a compromised local network. However, as it simply uses the SMB and VMI protocols to deploy it is not likely to be as prolific as previous worms such as EternalBlue for example. Another wiper variant, called “IsaacWiper”, has also been detected during a destructive attack on a Ukrainian government network. This variant shares no code similarities with HermeticWiper and is much less sophisticated.
Whilst there is no indication that either of the above wipers has been used against any country other than Ukraine, the risk is still there that threat actors may decide to deploy them against countries or entities supporting the Ukrainian government or imposing sanctions against Russia, remaining vigilant is therefore highly advised.
Other threats to non-Ukraine organizations going forward may well involve ransomware actors, with at least one on the famous RAMP forum recently looking for network access to companies from Ukraine but also NATO member countries.
For now, the most impactful attack against a Western company may have been the one against KA-SAT, a satellite connection service provider used by numerous clients in Europe and operated by ViaSat (a Viacom subsidiary). The service was down due to a “cyber event”, starting in Ukraine but also affecting other European countries. Unfortunately, no further information has been shared by the provider since first reporting it on February 24th. This day marks the launch of the war by Russian military forces; thus, the attack might well have been carried out purposely to disrupt specific communications capabilities in Ukraine.
Further hacktivism attacks against Russia continue to be reported although it is difficult to ascertain the accuracy of these reports. These reports include a group affiliated with Anonymous claiming they successfully attacked the control center of “Roscosmos”, the Russian Space Agency, resulting in Russia losing control over its satellites. Another example was from “AgainstTheWest” who claimed they attacked the Russian financial institution Sberbank and will soon be leaking DNS infrastructure data, private keys for SSL, Sberbank API, CLI and SDK’s. With the Russian government fully controlling the media coverage since the war started some hacktivists have got creative in their attempts to let Russian citizens know what is happening. One method used has been to flood restaurant reviews with anti-war/anti-Putin messaging.
A recording of a recent customer webinar can be found on our website here.
Links to our “Ransomware Can Be Beaten” guide, which we believe provides actions that can be taken which will also help you prepare in case of any collateral damage from any malicious activity from the war against Ukraine.
Updated 28th February 2022
The Internet is becoming more of a battlefield with a growing number of DDoS attacks, website defacements and data leaks. Possibly the most concerning activity was the announcement by the Conti ransomware (Cy-X) operation that they were siding with Russia and would attack critical infrastructure if Russia was targeted by any cyberattacks. They did later soften their message but that didn’t stop one of their members, presumably of Ukrainian descent, from leaking the group’s internal chat logs from the past year in an apparent act of hostility against the rest of the group.
Ukrainian authorities made an appeal for people to join an “IT Army” with easy-to-use guides made available to DDoS Russian targets, they also praised the Anonymous hacker collective for their activities against Russia. Anonymous was credited with taking the website of the state-run Russia Today TV channel down with a DDoS attack. Other attacks from unknown sources also resulted in Russian TV channels being hacked to broadcast pro-Ukrainian messages and songs.
Other “hacktivism” activities are continuing to be seen, with one of the latest attacks being carried out by the Belarusian group “Cyber Partisans” against the Belarusian rail network to disrupt Russian troop movements into Ukraine. Another attack targeted a Ukrainian border control station with wiper malware impacting the thousands of people currently trying to flee the country because of the war.
Following a direct request from the Ukrainian Vice Prime Minister, Elon Musk became an unexpected benefactor for Ukraine by announcing that SpaceX’s Starlink satellites had been activated in Ukraine and that more terminals were en route. This will help Ukraine maintain an online presence in the result that network infrastructure is destroyed by Russia. We expect hacktivism and ransomware activity to continue escalating as the conflict extends, but also remain alert for the escalation of direct and sophisticated state-backed activities targeting both of the primary protagonists, the accompanying threat of collateral damage to governments and businesses worldwide.
Summary
The war against Ukraine is developing by the minute, with clear implications to the cyber threat landscape. We would like to provide you with insights on what we have been observing, advise you on what you can do to protect yourself, and update you on what we are doing to keep our operations secure.
Several cyber-attacks have been observed since the beginning of the escalation of tensions. From disinformation campaigns on social networks to denial-of-service attacks on banking institutions and government sites.
It is important for businesses to monitor the situation daily and adapt to new and relevant information as it becomes available. Businesses that have direct ties to other businesses in Ukraine need to be particularly vigilant.
At this stage the primary goal of civilian businesses and organizations should be the stand-up, prepare and test Cyber Incident and Emergency Response capabilities. Prepare to ingest new intelligence and indicators of vulnerability, attack, or compromise from outside or inside your own organization, evaluate their potential impact make sound risk-based decisions and respond rapidly.
We believe that businesses that have implemented a strong and tested response to the ransomware threat are well-positioned to deal with any cyberattack that could potentially spill over because of the war against Ukraine. These controls will also help fend off any attackers that demonstrate state-level capabilities and skills like those that are likely to be active in and around this conflict.
Recommendations
Our primary recommendation involves developing and priming a robust Emergency- and Incident Response process, with trained people ready to execute it. If the threat level of this situation escalates further, or more specific intelligence becomes available, the key will be to enact a swift response, possibly under very adverse circumstances. If or when a specific elevated threat emerges, this may take the form of a completed compromise, malware, ransomware or wiperware infection, data leak, DDoS, misinformation or disinformation campaign, an imminent threat, or a vulnerability that needs to be patched. A response capability needs to be prepared to deal with any of the diverse situations listed above.
In addition, we recommend general defense-in-depth best practices for mitigating contemporary ransomware threats as a reasonable baseline for defense against a non-specific nation-grade attack:
- Identify and patch any internet-facing technologies, including especially Remote Access like VNC and Microsoft RDP, Secure Remote Access like VPNs, and other security technologies like Firewalls.
- Implement MFA on any internet-facing authentication interface.
- Frequent backups of business-critical assets complemented with offline backups.
- Test the integrity of these backups regularly by restoring critical functions.
- Endpoint protection and anti-malware
- Test these solutions and identify any blind spots.
- Defense against Distributed Denial of Service (DDoS)
- Implement a strategy that can protect networks and services exposed to the Internet from sustained large-scale network flooding that could cut the targeted network and services off from the Internet.
- Network Egress Filtering: Configure firewalls and other perimeter equipment to allow only the minimum of outbound traffic to the internet, especially from the DMZ and any internet-facing or critical systems. Monitor outbound traffic closely for anomalies.
- Monitor network for malicious activity
- The Mitre ATT&CK Matrix is a good reference to determine if you have any blind spots in your telemetry. This can help you expand on your detection capabilities, for example monitoring any execution of common built-in system utilities[1].
- Involve Incident Response teams as this can be useful to know what needs to be collected for forensic investigations.
- Continuous vulnerability management
- Prioritize patches based on whether vulnerabilities have known working exploits. This is applicable to infrastructure as well as end-user software or devices.
- Internet-facing services with known vulnerabilities must be patched.
- Network segmentation
- Identify trust boundaries and implement tight controls for services and users that want to cross into those zones.
- Least privilege concepts can also apply here.
- Least privilege
- Limit services to run with only the necessary privileges to perform their functions.
- Ensure staff has only access to what they require to perform their tasks.
- General Threat Hunting.
- In-house teams should schedule time to identify scenarios for threats applicable to the organization.
Our comprehensive vendor-agnostic guide to defending against the threat of ransomware can be found here.
This defense-in-depth guidance in the document above will also provide a robust defense against almost any threat that may result from a conflict between nations.
Risk Assessment
Threat Actor
The cyber landscape is populated by many capable and potential attackers. It is important that some threats are more applicable than others, but defenders must not lose sight of the entire threat landscape. A threat can be represented as follows:
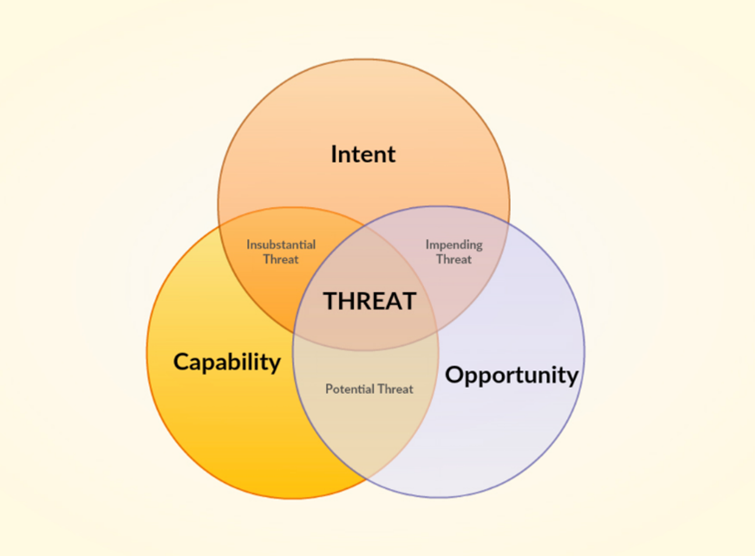
Threat Venn diagram by Rapid 7 [9]
Russia is currently seen as the primary aggressor in this conflict and cyberattacks by them will most likely be executed by groups or teams that are already well known to the cyber security community. These groups are sometimes referred to as Advanced Persistent Threats (APTs) or Threat Actors.
We’d like to stress that one should not solely rely on controls put in place that exclusively protect against specifically named threats. Controls should be put in place and matched against specific phases of the cyber kill chain based on the capabilities of the business [10]. If a business feels they are targeted by a specific group, then it makes sense to invest there. The best return on time and energy will be to put measures in place that will defend against a range of threats for a given part of the kill chain.
Threat Level
We are working with limited information and there are significant intelligence gaps. We do not fully know how far this conflict will escalate and what risks each party is willing to take. The best approach is to be alert and ready to respond when the situation turns for the worst.
One way to describe this is using the ”Cooper color code system” [11]. This system was developed for military application, but can be applied to civilian life. It consists of four states represented by the colors white, yellow, orange and red. These represent levels of awareness in an environment that may possibly contain threats.

White is a state where the entity has no awareness of any threat and is not trying to find any threats. Typically, this state is a result of “zero concern for personal safety”. Ideally, no one should find themselves in this state.
Yellow represents what should be considered as the normal state. An entity is making an active attempt to identify potential threats. This is manifested by self-awareness and self-reliance. This state does not constitute someone living in fear or constant paranoia, but rather someone that is looking out for possible danger.
The Orange state is when a threat has been identified and a solution is being calculated. The implications of this are that the entity that identified the threat will increase its mental effort to focus on the threat, thus potentially losing temporary sight of other threats. Maintaining this state is taxing.
Finally, the Red state signifies that the entity has devised a plan to navigate the threat. This leads to an intense reaction specifically focused to address the threat.
Following the Cooper color system, we assign an Orange state with the emphasis on being ready and devising plans to navigate scenarios identified.
The Orange state is when a threat has been identified and a solution is being calculated. The implication of this state increased mental effort to focus on the threat, thus potentially losing temporary sight of other threats. Maintaining this state is taxing.
At this threat level we, therefore, recommend that customers be aware, vigilant, and prepared to react, but without being distracted from the broader strategic priorities for building cyber resilience within their systems and businesses.
Potential Targets
Potential ‘targets’ for cyberattacks include:
- Ukrainian government institutions
- Defense & Military institutions including manufacturers
- Telecom sector & Internet traffic
- European media – propaganda
- European & US industries invested in Ukraine
- US, European and other governments allied with either party or imposing sanctions or other costs.
We should recall, however, that in the infamous NotPetya attack, the most damage was caused to organizations that were not specifically targeted, but rather became collateral damage when the NotPetya worm accidentally escaped its original targeting constraints. A repeat of this scenario should also be a cause for concern.
Cyberattack Methods
The predicted attack methods listed below are not exhaustive but represent a range of methods from most likely – Method 1- to least likely – Method 5 – that we can expect to be deployed in this conflict.
There is also of course the persistent threat of disinformation and misinformation campaigns around this conflict, but those are beyond the scope of this document.
Method 1 – Distributed Denial of Service (DDoS)
Breakdown
Denial of Service attacks can take multiple technical forms but the most common contemporary variant is the Distributed Denial of Service Attack, where multiple external systems are co-opted into flooding a single victim endpoint with enough network traffic to consume all available bandwidth or resources.
- High-volume traffic intended to saturate the Internet access of targeted enterprises Service inside the network
- Bandwidth attacks combined with attacks on firewalls or IPS (Intrusion Prevention System) security infrastructure and applications
- Attacks that target a large range of business applications (HTTP, HTTPs, VoIP, DNS and SMTP).
- Perimetric defenses are generally ineffective against these threats.
Overview
DDoS attacks are popular for their relative ease of implementation and are commonly deployed by state actors, hacktivists and cybercriminals alike. Various tools and techniques, including botnets for rent, enable an attacker to generate far more traffic than an average organization can process, resulting in platforms and services becoming unavailable to authorized users. Because the source of the attack is ‘distributed’ across multiple, unwitting agents, it is very difficult for the victim to manage the traffic and mitigate the attack.
It’s generally not considered enough just to protect the traditional ‘shop window’ from DDoS. Solutions are typically based on a notion of a ‘scrubbing center’. A scrubbing center is a cleaning center installed on the internet in front of an organization’s internet access, with the objective of centralizing and cleaning streams polluted by DDoS attacks before sending them on the to the legitimate target IP addresses.
This type of solution requires traffic to be forced towards the scrubbing center. Two deflection strategies may be considered: Diversion only if attacked – in which case, there is a delay between the time the attack is identified and when the filtering is effective – and Systematic deviation (always on mode) – in which case, the traffic is always forwarded to the scrubbing center.
Method 2 – Phishing
Breakdown
The attack will involve:
- Phishing to facilitate
- Credential Theft
- Malware drop
- Remote access through legitimate services (VPN) or specialized malware
- Elevation of Privileges
- Lateral Movement
Overview
The most likely and plausible attack involves what we have observed to be the simplest and most effective. In this approach, the attackers leverage spear phishing to either steal credentials or deploy malware on the endpoint.
Credential theft could be used to access services such as secure remote access or VPNs, alternatively services relying on exposed Remote Desktop Protocol (RDP) can then be accessed using legitimate credentials.
Other forms of attacks related to credentials compromise involve credential brute-forcing or credential stuffing. This type of attack is very noisy and could tip off defenders.
As stated above, phishing lures could also be used to drop malware on a victim’s machine. These types of phishing attacks will include an attachment that, when opened by the recipient, will result in malware executing on the host. The absence of endpoint protection and antimalware solutions will result in the attacker having remote code execution.
Gaining remote access to business infrastructure will allow the attacker to then move toward their objective. The attacker may seek to elevate their privileges or steal cached credentials that will enable the attacker to move laterally. Versions of common tools such as Mimikatz could be used to achieve this.
The attacker will propagate through the environment ultimately seeking to embed themselves in the infrastructure. Remote access trojans could be used or other specialized tooling such as the infamous Cobalt Strike framework has been popular of late.
Method 3 – Exploiting known vulnerabilities
Breakdown
State-backed actors, including those we see active around the conflict, are adept at finding and exploiting systems that haven’t been patched for known vulnerabilities.
- The primary target will be systems exposed to the internet
- Remote Access platforms like RDP and VNC are frequently targeted
- Several vulnerabilities on security products like VPNs and firewalls are also actively exploited in the wild
Overview
State-sponsored actors are skilled at finding and exploiting unpatched systems, and they have the necessary fieldcraft to pivot off the compromise of an internet-facing system to gain traction in the internal network and move laterally.
Any internet-exposed system, including especially remote access and security technologies, should be fully patched. But the US Cybersecurity and Infrastructure Security Agency (CISA) noted in a January 11 advisory [12] that some specific vulnerabilities were commonly targeted by actors in the region. These include:
- CVE-2018-13379 FortiGate VPNs
- CVE-2019-1653 Cisco router
- CVE-2019-2725 Oracle WebLogic Server
- CVE-2019-7609 Kibana
- CVE-2019-9670 Zimbra software
- CVE-2019-10149 Exim Simple Mail Transfer Protocol
- CVE-2019-11510 Pulse Secure
- CVE-2019-19781 Citrix
- CVE-2020-0688 Microsoft Exchange
- CVE-2020-4006 VMWare
- CVE-2020-5902 F5 Big-IP
- CVE-2020-14882 Oracle WebLogic
- CVE-2021-26855 Microsoft Exchange
Note that eliminating these specific vulnerabilities is not a substitute for general vulnerability management and attack readiness.
Method 4 – Supply Chain Compromise
Breakdown
This could possibly be as follows:
- An attacker compromises supplier(s) of a target
- Pivot on to target using:
- Direct network access
- Backdoor software distributed to target
- Abuse trusted relation of the supplier to phish target
Overview
A supply chain compromise is an effective means to gain access to a target by using a trusted third party. This type of attack is more complicated than method 1 as it requires multiple steps to execute and could take longer.
We will assume an attacker has access to an organization and the attacker believes that they can gain access to their target by exploiting the established relationship. This all depends on the type of relationship that exists.
Businesses such as Managed Service Providers might have remote access to a client’s network as part of their service delivery process. This could be as simple as a network route that allows traffic to flow between businesses, or more involved requiring access control. Either way, the attacker can jump from one network to another.
Another example of supply chain compromise involves compromising software or hardware that will be used by the target. The attacker plants malicious components or weakens existing components to allow it access in a predictable and reliable manner. The challenge for the attacker is that this kind of compromise may spill over to unintended targets. This may be irrelevant depending on the type of dormant component planted by the attacker. The likelihood of collateral damage increases if destructive malware was injected that indiscriminately damages systems. There are technical measures that attackers could implement to control the blast radius, but that may depend on the attacker.
As mentioned earlier, the type of supplier compromise could involve using social engineering. It could be as simple as the attacker using the compromised victim’s email system to send a malicious email to their target. For example, the attacker uses an existing email thread and injects some malicious attachment or link. Chances are that the recipient will be less on guard and fall for the deception much more easily. Also, the attacker can leverage that trust relationship to gather more intelligence before launching their phishing attack, increasing their chances of success.
Method 5 – Zero-Day
Breakdown
An attacker can exploit unknown weaknesses in:
- Services exposed to the internet
- Service inside the network
- Browsers
- Email Clients
- Mobile Devices and Apps
- Network Equipment
- IoT Devices
Overview
We mention zero-day vulnerabilities on the end of the scale as this is a likely possibility that a state actor with a known history of cyber aggression is involved. Highly resourced and well-trained teams with years of experience could possibly have access to zero-days that they are willing to burn given the stakes. It is important to note that zero-days are discovered rather than injected. Vulnerabilities of this class are discovered by skill and chance.
This attack method could be incorporated as part of methods 1 and 2, but it could also serve as the initial entry point. There is little that anyone can do to stop a highly motived and skilled attacker from exploiting an unknown vulnerability. The type of zero-day and the type of impacted application or device determines the usefulness of the zero-day.
Zero-days in internet-facing services such as email, web, or even security products such as secure remote access could contain a potentially dangerous unknown vulnerability. Depending on the nature of this flaw, the attacker could gain access to the underlying operating systems of the host, steal sensitive information or chain the vulnerability with something else to trigger a malfunction resulting in a denial of services.
Zero-days in browsers, email clients, and messaging applications can be particularly valuable as these could be exploited through watering hole attacks or merely sending a malicious message to their victim.
We do know that exploiting fully patched mobile devices that receive regular security updates will be difficult to exploit. Mobile device exploitation is useful for surveillance, and this could be a means to an end, but it is unlikely that this type of zero-day will be used in mass exploitation. Instead, it will be directed at specific targets as part of information gathering.
What we are doing to keep our customers secure
Orange Cyberdefense has taken action to protect our customers and operations, in coordination with the Orange Group via the following:
- Activated the group-wide Crisis Management process and ream consisting of our CERT, Research capabilities, detection and scanning operations, communications, internal security, and representatives from potentially impacted countries.
- All relevant and actionable intelligence is being automatically distributed to relevant operational teams and customers via our standard mechanisms – World Watch Advisories, Vulnerability Watch Advisories and our CTI Datalake.
- Our operations teams – CERT, CyberSOC, SOC, Vulnerability Scanning, and CSIRT – have been placed on high alert and are being updated as any concrete intelligence is available.
- We hold regular briefings with relevant internal teams to provide updates and gather intelligence on the situation as experienced by them and their customers ‘on the ground’.
- Detailed technical guidance has already been developed in advance of the crisis and will be regularly updated as the need arises.
- Our detailed technical ‘World Watch’ advisories regarding the situation are distributed to all clients as the need arises.
- Confirmed Indicators of Compromise and Attack are being shared on the public internet via our Github site as a contribution to greater community defense efforts.
Conclusion
Any national conflict has far-ranging implications for the world at large, and cyberspace is no exception. Apart from the specific threats to organizations ‘directly’ involved in the conflict, it has the general effect of ‘inflating’ the risk for everyone.
While we can identify some specific actors and methods that are likely to come into play during this specific conflict, it is this more general inflation of the risk that most organizations should focus their attention on.
The response to this exaggerated risk is to assume a state of general readiness while continuing to pursue a robust strategy of robust defense in depth that will position us for a diversity of threats that may emerge from this conflict or elsewhere.
References
| [1] | Mitre, “Matrix – Enterprise | Mitre ATT&CK,” [Online]. Available: attack.mitre.org/matrices/enterprise/. [Accessed 31 January 2022]. |
| [2] | K. Zetter, “Inside the Cunning, Unprecedented Hack of Ukraine’s Power Grid,” March 2016. [Online]. Available: www.wired.com/2016/03/inside-cunning-unprecedented-hack-ukraines-power-grid/. |
| [3] | K. Zetter, “The Ukrainian Power Grid Was Hacked Again,” Motherboard by Vice, January 2017. [Online]. Available: www.vice.com/en/article/bmvkn4/ukrainian-power-station-hacking-december-2016-report. |
| [4] | A. Greenberg, “New Clues Show How Russia’s Grid Hackers Aimed for Physical Destruction,” Wired, 12 September 2019. [Online]. Available: www.wired.com/story/russia-ukraine-cyberattack-power-grid-blackout-destruction/. |
| [5] | L. Loeb, “NotPetya Operators Installed Three Backdoors on M.E.Doc Software Server Before Activating Malware,” Security Intelligence, 10 July 2017. [Online]. Available: securityintelligence.com/news/notpetya-operators-installed-three-backdoors-on-m-e-doc-software-server-before-activating-malware/. |
| [6] | L. Harding, “Ukraine hit by ‘massive’ cyber-attack on government websites,” The Guardian, 14 January 2022. [Online]. Available: www.theguardian.com/world/2022/jan/14/ukraine-massive-cyber-attack-government-websites-suspected-russian-hackers. |
| [7] | K. Zetter, “Wiper in Ukraine Used Code Repurposed From WhiteBlackCrypt Ransomware,” 26 January 2022. [Online]. [Accessed 31 January 2022]. |
| [8] | R. Lakshmanan, “Massive Cyber Attack Knocks Down Ukrainian Government Websites,” 14 January 2022. [Online]. Available: thehackernews.com/2022/01/massive-cyber-attack-knocks-down.html. |
| [9] | Rapid 7, “Using Threat Intelligence to Mitigate Wanna Decryptor,” 15 May 2017. [Online]. Available: blog.rapid7.com/content/images/post-images/63249/Screen%20Shot%202017-05-15%20at%207.35.41%20PM.png. |
| [10] | Lockheed Martin, “The Cyber Kill Chain,” [Online]. Available: www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html. |
| [11] | K. T, “The Cooper color code and threat assessment,” SoftRep, [Online]. Available: sofrep.com/news/the-cooper-color-code-and-threat-assessment/. |
| [12] | www.cisa.gov/uscert/ncas/alerts/aa22-011a |
