
Cyber Extortion (Cy—X): the actors and the victims

A new definition of cyber criminology
The term ransomware has become a commodity in the media as we daily read about it in the papers. To counter the ransomware threat, we do have to make an important distinction that is often not elaborated on in the stories. Ransomware itself is the end of an attack. An attack is not done by ransomware, you are being deployed with ransomware. Ransomware describes a form of malware, not a form of crime.
Ransomware is just a way of extortion. When organizations are increasing their security posture, it might be difficult for the adversaries to gain access to an organization. But attackers could put an organization under extortion by a D-Dos attack of simple data theft.
We propose to use the term ‘Cyber Extortion’, abbreviated to ‘Cy-X’ (pronounced ‘sigh ex’):
“Cy-X is a form of computer crime in which the security of a corporate digital asset (confidentiality, integrity or availability) is compromised and exploited in a threat of some form to extort a payment.”
The ultimate act of extortion involves the commitment of more than one crime, including the unauthorized access to computers and data on the one end of the spectrum, and the act of extorting a ransom near the other.
Taking a closer look
Now that we have determined the terminology for this criminology, we can take a further look at the threat landscape and its actors and victims. Who are the players in this field and to which industries or countries do they cause the most damage?
Cy-X is a unique form of cybercrime in that we can observe and analyze some of the criminal action via ‘victim shaming’ leak sites.
Through our own research, analyzing and enriching data scraped from the various Cy-X operator and market sites, we can provide direct insights into the victimology from this specific perspective. We’ll refer to the listing of a compromised organization on a Cy-X leak site as a ‘leak threat’.
Since the start of January 2020, we identified and documented 3,027 unique ‘leak-threats’ of this kind across 67 distinct actors. As the dark web is by definition not indexed, we can only record the threats we do see. But we do see a substantial increase, with an almost six-fold increase in leak threats from the first quarter of 2020 to the third quarter of 2021.
The actors
As in any other business that proves profitable, competition start to arrive. It is, therefore, no wonder that the number of distinct actors has continued to grow. Interesting to notice here is that the growth in threats and actors observed is not linear, as can be seen in the chart below.
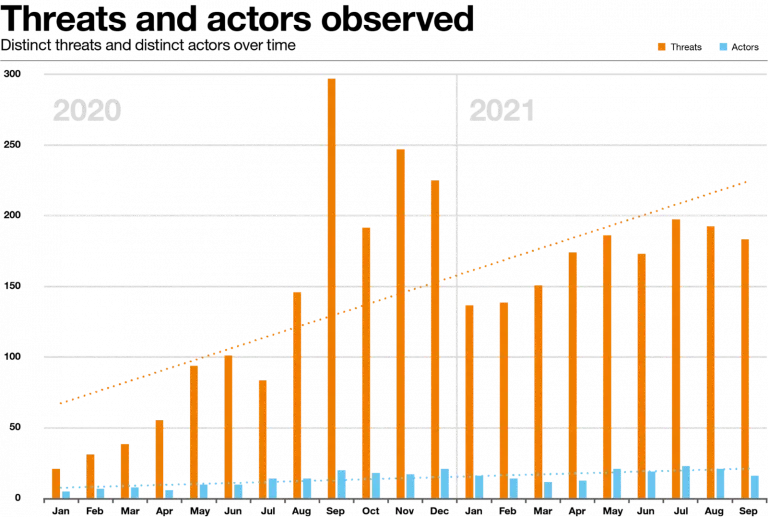
There is also a large difference in “size” in the field. Almost 50% of all threats can be attributed to just five ‘alpha’ actors - Conti, REvil, Maze, Egregor and LockBit 2.0. From a different perspective, the other 50% of all threats are attributed to a second tier of 58 different groups, 30 of which have made more than 10 threats in the last two years.
The victims
Returning now to the 3,027 records in our leak site threat data, let’s take a look at the industries and countries the victims operate in.
When looking at the different countries, one conclusion we can draw is that the relative number of victims in a country is simply a function of the number of online businesses in that country which can be traced back to the relative GDP of that country. The bigger the economy, the more victims it is likely to have.
This conclusion does not mean however that businesses in other countries are not targeted. Globally, there is an even probability that a business in any given country will fall victim. Logically, the more businesses a country has, the more victims we will see.
Same as the spread over different countries, leak threat victims can be found in any industry. However, we can identify two industries significantly ranking the highest, which are Manufacturing and Professional, Scientific and Technical Services organizations.
There are several explanations that could apply to this ranking. Perhaps criminals think that these sectors are more likely to pay, or they think that their overall cybersecurity posture is not as robust as others.
If actors were targeting specific industries, we’d expect to see at least some level of specialization. The fact that we don’t, suggests that these most-featured industries are not being specifically targeted, but rather have something else in common. We propose that the common denominator is simply that they are less prepared to stave off attacks.
Conclusion
The Cy-X threat actor landscape is complex and dynamic. The total number of actors is growing steadily even as individual actors come and go over time. While a handful of ‘alpha’ players are responsible for about half of all the crimes, there are dozens of other ‘smaller’ players to contend with also.
Cyber Extortion continues to evolve, not only in the technology it deploys but also through its business model. As new forms of extortion continue to become more prominent, we should prepare to adjust our technical defenses and other countermeasures accordingly.
This blog is an extract of our 2022 Security Navigator. For more in-depth details, figures, and background stories on Cy-X you can download the report here.
Watch a recording of our Security Navigator webinar


