

Continuous Threat Exposure Management
Bolster your vulnerability management strategy with CTEM and make sure no part of your infrastructure is left exposed.
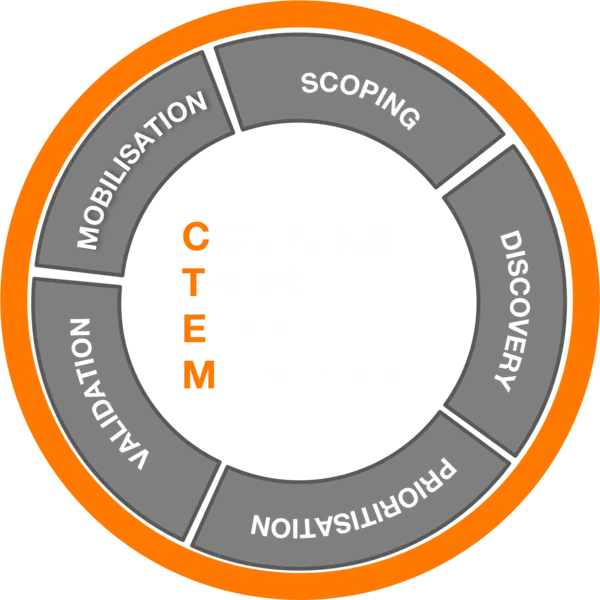
CTEM is composed of a structured approach to continuously identify, assess, and remediate an organization’s exposure to cyber threats.
CTEM aims to provide a proactive, risk-based methodology for reducing vulnerabilities and limiting the attack surface, improving an organization’s overall security posture. The key components are:
Scoping – defining the attack surface considered in this cycle.
Discovery – identifying all assets and their posture in the scope of the cycle.
Prioritization – pinpointing high-value assets and most critical risks.
Validation – confirming the exploitability and assessing the potential impact.
Mobilization – operationalizing according to the findings.
With CTEM, you'll gain enhanced visibility into your attack surface and the overlayed risks, which allows to better understand attack paths to business-critical assets. Like that, you can:
Prioritise Threats with real-world exploits
Understand where you don’t need to focus
Focus on Choke Points, not Dead Ends
Close the remaining easily exploitable attack paths


Cross-functional teams delivering vulnerability intelligence, global threat advisories, targeted threat intelligence and incident response services.

+9.000 customers worldwide, giving us a unique overview of the latest challenges and threats from cybercriminals.

1st private CERT in Europe with 140+ CERT experts globally continuously monitoring threats, vulnerabilities and attack trends.
Out team of experts is always ready to help.
Fill in the form to get in touch with us or to schedule a no-obligation consultation.


23 July 2020

28 December 2023

Security Navigator 2025 Research-driven insights to build a safer digital society, Adopt a proactive security posture based on cyber threat intelligence.