
Elevate Your Security Capabilities with Best-of-Breed Intelligence
Recognized by Gartner and Forrester as a leader in managed security services, Orange Cyberdefense offers an intelligence system for effective defense operations.
Equip your security teams to detect threats, conduct hunts, and report incidents with our expert Cyber Threat Intelligence (CTI).
Access our enriched intelligence database daily and enhance your operations, giving your analysts the tools to reach their full potential.
Boost Your In-House SOC
To assess all network observables accurately, your SOC team needs a robust operational intelligence database. Great security analysts also require strategic and tactical intelligence to link Indicators of Compromise (IoCs) to the bigger picture.
Understanding adversaries and their tactics helps create effective threat hunting playbooks, detection rules, and enriches SOC incidents.
Managed Threat Intelligence [detect] provides access to our proprietary CTI database, consolidating over 450 public and private sources. This includes IoCs, strategic advisories, and a threat actor library, broadening your SOC team's context. It simplifies intelligence-led security, eliminating the need for multiple sources, tools, or specialized teams.

First-hand intelligence and home-made TIP
1.
The Managed Threat Intelligence [detect] service is proposing you the access to Orange Cyberdefense home-grown Threat Intel Platform (TIP) in SaaS mode, designed to fit perfectly the needs of SOC analysts, and full of the content they need, from strategic to operational intelligence, continuously maintained and enhanced.
The data is qualified and enriched by our experts, it's ready to be consumed via API or its interface.
2.
The intelligence included is none of the less the best curation and enriched OS-INT you can find, but it's also some exclusive private sources from trusted partners and first hand intel produced by Orange Cyberdefense, like Command and Control reverse engineering IOCs, exclusive malicious domains and IPs linked to phishing, operational sightings, DNS data, strategic advisories, vulnerability database.
Benefit from industry-leading Cyber Threat Intelligence
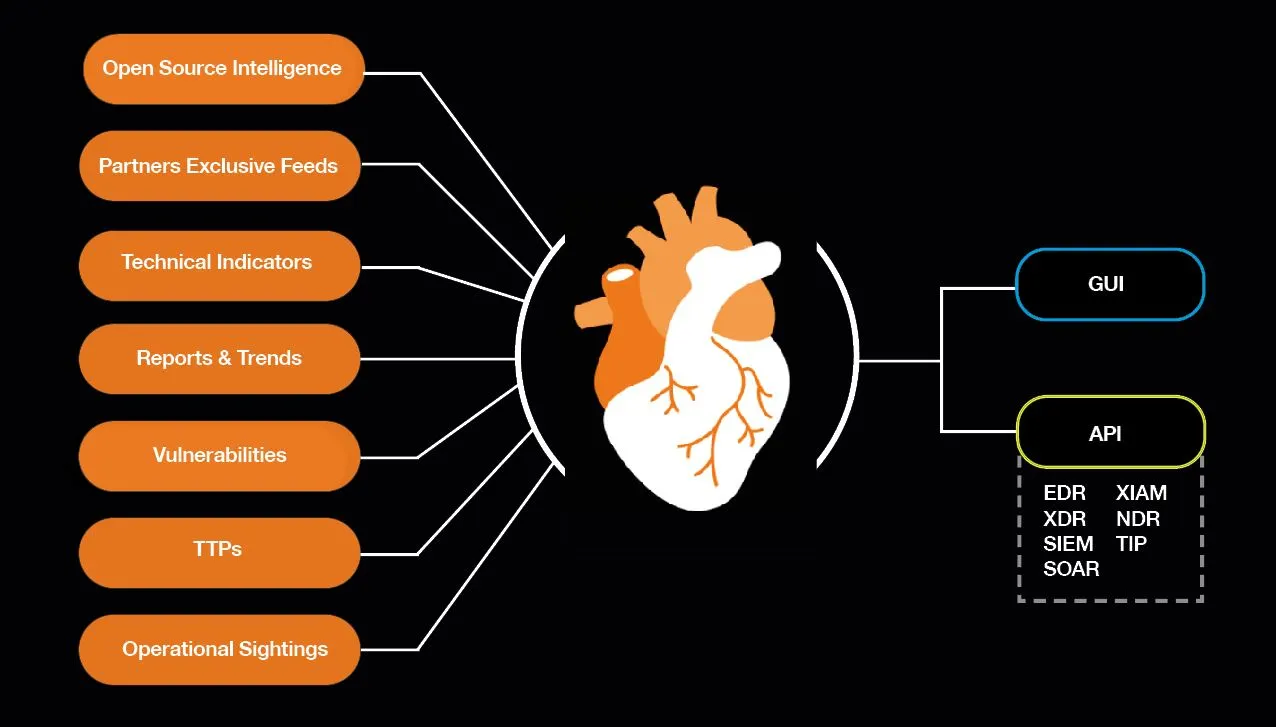
Our Intelligence ready to consume:
- Sightings from our SOC
- 700 000 new IoCs per day
- Orange DNS Data
- Orange Cyberdefense strategic advisories
- Orange Cyberdefense malware reverse engineering
- Orange Cyberdefense vulnerabilities database
- Proprietary scoring algorythms
- Easy to integrate with SIEM, SOAR, TIP, EDR, XDR, XIAM, NDR
- Powerful API to forge your own feed
- SaaS portal for easy search
- Long history of malicious indicators
- Unlimited users per licence
Obtain qualified and actionnable data about threats to better anticipate
Extend your threat detection
Create more and better detection rules for your SIEM, EDR or XDR
Speed up qualification of incidents
Decrease incident response times by using your SOAR to enrich your alerts with context
Time & money saving
Achieve better ROI on existing technology and teams via a single CTI service
Satisfy your SOC team
Give your analysts what they want and need to love their job
Deep dive into our datasheet:



![Managed Threat Intelligence [detect]](/fileadmin/_processed_/8/8/csm_mitreattack_0732c399ff.webp)


