Impact of the transition from the CVSSv3 to CVSSv4 norm

Summary
A little over a year ago, on November 1, 2023, the Forum of Incident Response and Security Teams (FIRST) officially launched version 4.0 of its CVSS standard after several months of work within the CVSS-SIG working group, of which Orange Cyberdefense is a member.
This new version succeeds CVSSv3, which has established itself as the reference standard for vulnerability scoring for nearly a decade (CVSSv3.0 was published in 2015, and CVSSv3.1 in 2019).
This blog post aims to provide feedback, as a CERT, on the use of CVSSv4.0 and its impact on vulnerability scoring. Indeed, we at CERT Orange Cyberdefense have implemented this scoring for all clients of the Vulnerability Intelligence Watch service alongside version v3.1.
This feedback will primarily focus on the scoring discrepancies between CVSSv3.1 and CVSSv4.0. The purpose of this post is not to reiterate what CVSS is, its new features, strengths, weaknesses, or implementation methods (which could be the subject of a dedicated post), but rather to present the impact of transitioning from CVSSv3.1 to v4.0.
In recent months, we have scored thousands of vulnerabilities using CVSSv4.0: the statistics presented are based on 2024 data, and the metrics used come from the vulnerability database of CERT Orange Cyberdefense.
Not so hard
We can immediately say the following: "The Base score is good, but the Threat score is much better!"
Let’s take a brief look back: everyone can recognize that the CVSSv3.1 score provided an upward evolution from CVSSv2.0, with an average increase of 40% in vulnerability scores, both for the Base Score and the Temporal Score. Spoiler: the increase will not be as significant between CVSSv3 and CVSSv4.
Even today, a significant portion of companies chooses to use only the Base CVSS score for their Patch Management, although this proportion is gradually decreasing. This choice is generally driven by three reasons:
- Ease of use
- Alignment with the vendor's score (with few exceptions, vendors only use Base metrics)
- The score is often highlighted in regulations applicable to certain sectors (SWIFT, PCIDSS, etc.)
This score indeed has its advantages, but also its limitations:
- No consideration of risk
- No consideration of the exploitability status of a vulnerability
- No consideration of the environment in which the vulnerable system may reside – and thus no real risk
The first difference we identified is that, overall, the CVSSv4.0 score is slightly higher than the CVSSv3.1 score, except for:
- Vulnerabilities with a very high score (> 9)
- Vulnerabilities with a very low score (< 4)
Outside of these bounds, CVSSv4.0 has an average score that is about 10% higher.
However, the major innovation with CVSS version 4.0 is the more significant gap between the Base score and the following metrics (Temporal for v3.x and Threat for v4.0).
CVSSv3.1 Base/Temporal: Not a Big Deal!
Whether one is a beginner or an experienced user, it is clear that even if a vulnerability is not exploited, the difference in scores between Base metrics and Temporal metrics in CVSS version 3.1 is minimal – leading users to prefer additional standards such as EPSS.
The consequence of this is the near non-adoption of these metrics, even though they should have allowed for widespread use due to the presence of the exploitability status of the vulnerability.
The notion of vulnerability exploitability in the temporal score can be associated with:
- The publication of a proof of concept
- The publication of exploit code
- Evidence of the vulnerability being exploited in the wild (either targeted or widespread)
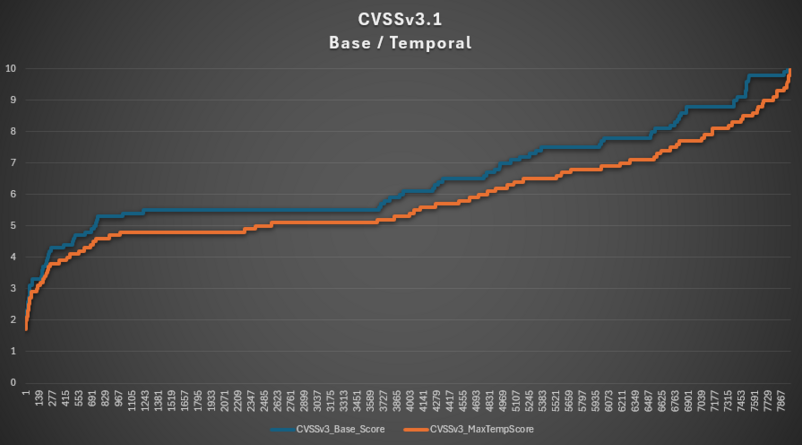
Scoring on Base and Temporal Metrics in CVSSv3.1
Note: Graph Legend:
- X-axis: Vulnerability ID (X on the ~8000 vulnerabilities used in this graph)
- Y-axis: CVSS score of the vulnerability
The vulnerabilities used in this graph have been sorted from the lowest score to the highest.
CVSSv4.0 Base/Threat: Harder, Better, Stronger
One of the significant differences between CVSSv3.1 and CVSSv4.0 is the strategic change in the mathematical model used.
During the development of CVSSv4.0, the working group chose to involve members of the CVSS-SIG, leveraging their expertise in vulnerability knowledge, management, and potential impact. Based on thousands of responses from various use cases, a new model – based on "Equivalence Groups" – emerged.
One consequence of this new model is the non-linearity of scoring gaps between Base metrics and Threat metrics – demonstrated in the graph below.
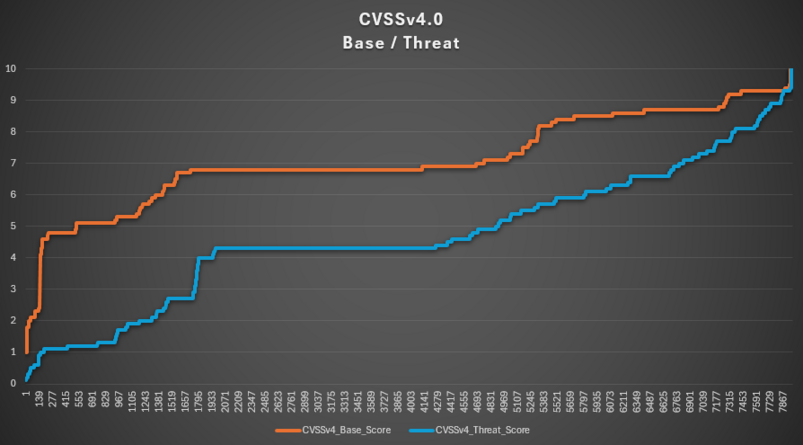
The graph above illustrates a significantly larger gap between the Base score and the Threat score compared to what was observed with CVSS version 3.1.
This significant difference indicates that the use of Threat metrics in CVSS version 4.0 allows users to prioritize their vulnerabilities more effectively than in version 3.1.
Scenario from 7.0
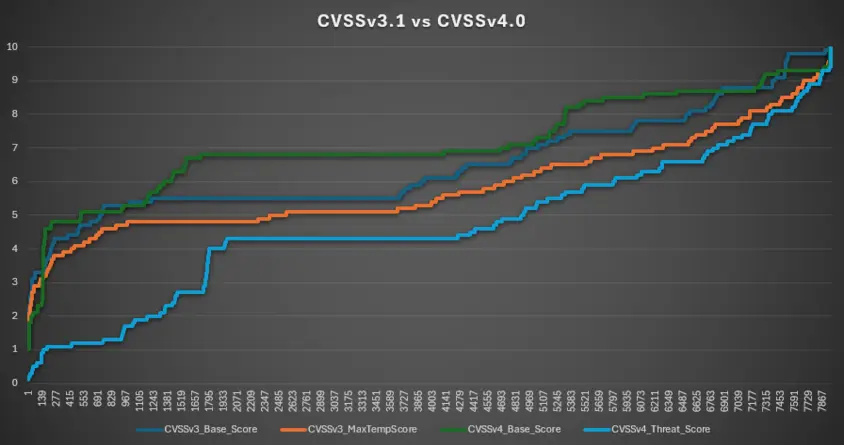
Assuming the user needs to address all vulnerabilities starting from 7.0 (from the ~8000 vulnerabilities used):
- CVSS v3.1 – Base Metrics: 3028 or 38%
- CVSS v3.1 – Temporal Metrics: 1775 or 22.3%
- CVSS v4.0 – Base Metrics: 3288 or 41.3%
- CVSS v4.0 – Threat Metrics: 1177 or 14.8%
Using temporal/threat metrics results in a reduction of:
- CVSSv3.1: -40% of vulnerabilities to address
- CVSSv4.0: -65% of vulnerabilities to address
Scenario from 8.0
Now, assuming the user needs to address all vulnerabilities starting from 8.0 (from the ~8000 vulnerabilities used):
- CVSS v3.1 – Base Metrics: 1449 or 18.2%
- CVSS v3.1 – Temporal Metrics: 818 or 10.3%
- CVSS v4.0 – Base Metrics: 2643 or 33.2%
- CVSS v4.0 – Threat Metrics: 631 or 7.9%
Using temporal/threat metrics results in a reduction of:
- CVSSv3.1: -43% of vulnerabilities to address
- CVSSv4.0: -76% of vulnerabilities to address
This is more easily demonstrated in the graph below, which aggregates CVSSv3.1 and CVSSv4.0 data.
CVSSv4.0: Apply Now
Despite these developments and numerous advantages, change remains challenging to implement.
The challenge of migrating from CVSSv3.1 (which remains the reference today) complicates the transition to this new version.
Although many vendors have made the leap (kudos to Palo Alto Networks for being the first to publish advisories solely in CVSSv4.0 – even before MITRE adopted this standard), many well-known vendors have not yet adopted it (Red Hat, Microsoft, Cisco, Oracle, etc.) – currently only offering CVSSv3.1 scores in their security bulletins.
Due to lack of priority, time, or internal tooling complexity, this unfortunately has a negative effect on the adoption of version 4 by a broader audience, both from vendors and end users.
Nevertheless, in a note of optimism, it is clear that all the positive feedback gathered through a survey published by the CVSS working group, as well as client feedback, demonstrates the interest in migrating to this version of the standard. The training module established by the CVSS-SIG working group has also trained a large number of users.
In the coming months, the CVSS-SIG group will look into potential evolutions, which could include:
- New additional metrics
- Incorporation of EPSS into the Threat score
- Review of the scoring logic for Environmental metrics
- Integration of "Supply Chain"
- Visibility of exploit codes (Private/Public)
- Consideration of the "Undefined" vector chain
- Integration of the notion of "Reachable Equipment" (Frontend/LAN/Offline, etc.)
What About CVSSv4 at CERT Orange Cyberdefense?
The CVSS 4.0 standard is used as the scoring metric for all vulnerabilities in the Vulnerability Intelligence Watch service, providing vulnerability monitoring services.
