The hidden network: How China unites state, corporate, and academic assets for cyber offensive campaigns
Authors: Piotr Malachinski, Marine Pichon
Special thanks to Kevin Ziadeh and the World Watch team
Explore directly our interactive map here and read the associated report here.
Between 2023 and 2024, our World Watch Cyber Threat Intelligence team issued over 35 advisories and updates concerning zero-day vulnerabilities exploited by Chinese threat actors. These account for 41% of all advisories with a high or very high threat level (above 4/5 based on our scoring scheme), representing a substantial portion of the critical threats potentially facing our customers. Whether aimed at directly compromising organizations for intelligence gathering or broadly infecting edge devices to build botnets or operational relay box (ORB) networks, the exploitation of vulnerabilities by Chinese state-linked threat actors underscores their considerable offensive capabilities.
Given China's authoritarian governance, characterized by extensive party control over social, political, and economic spheres, one might assume that cyber operations by these APT groups remain strictly in the hands of the state. However, China’s offensive cyber capabilities are, in fact, supported by a complex and multi-layered ecosystem involving a broad array of state and non-state actors.
In February 2024, a leak at a Chinese company Sichuan i-SOON provided further evidence of the extensive public-private cooperation in support of Chinese state cyber operations. From official contracts to internal communications, the leaked documents exposed i-SOON's role as a long-time contractor for the MSS, carrying out cyber campaigns against targets in over 70 countries, from France to Rwanda or Nepal.
China’s engagement with non-state actors is not confined to private companies. The government has a longstanding tradition of integrating top universities into national security efforts. The "Seven Sons of National Defense", for instance, are key academic institutions affiliated with the Ministry of Industry and Information Technology, contributing significantly to the state’s defense R&D efforts. As it turns out, this collaboration also extends to cyberspace, as the academia increasingly supports state-sponsored cyber campaigns, often focused on espionage to advance China's political and economic interests.
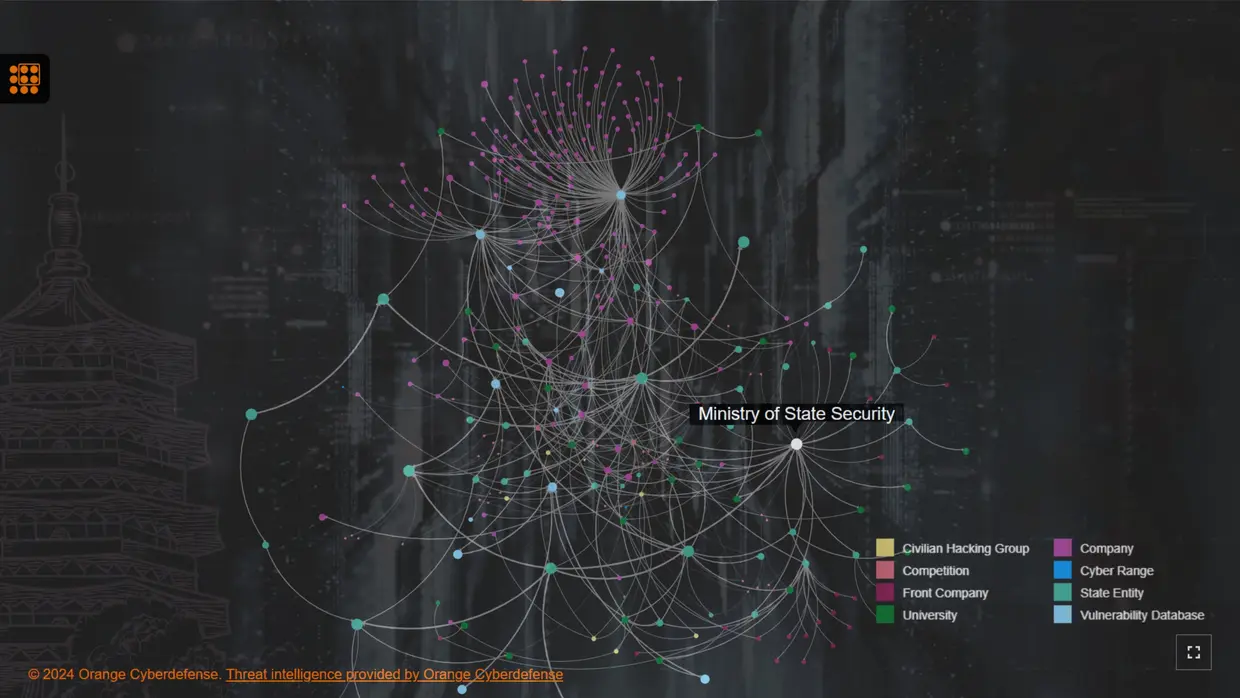
For several months, Orange Cyberdefense CERT worked on better mapping China’s cyber threat landscape, with a particular focus on the integration of civilian and military cyber capabilities. The result of this research is the release of an interactive map which is designed to illustrate the complex relationships within the Chinese cyber ecosystem.

This interactive map contextualizes threat actors’ activities and builds on existing research by leading experts and insiders, including Dakota Cary, Adam Kozy, Eugenio Benincasa, the Natto Thoughts research team, and the Intrusion Truth group.
As of October 2024, the map includes over 315 nodes, namely:
- Chinese state entities (42)
- Vulnerability Databases (12)
- Private companies (171)
- Front companies (19)
- Universities (24)
- Cyber Competitions (39)
- Civilian Hacking groups (7)
- Cyber Ranges (2)
The map is fully interactive, allowing users to easily explore nodes using mouse navigation or search filters such as tags, location, and pipelines. Tags include identifiers of intrusion sets and/or known threat groups, including:
| APT1 | APT14 | APT27 | APT41 | Stalker Panda |
| APT2 | APT17 | APT30 | Circuit Panda | Karma Panda |
| APT3 | APT19 | APT31 | Nomad Panda | Ethereal Panda |
| APT10 | APT26 | APT40 | Dragnet Panda | LuckyCat |
Locations refer to both the specific city (if known) where the node is located, as well as the broader region. We have chosen to regroup these locations into five theaters, aligned with the military theater commands of the PLA. This consolidation can be particularly insightful as it illustrates the distinct focuses and areas of targeted operations, including for non-PLA nodes.

More than 400 relationships are featured and detailed, each represented by clickable arrows that link the nodes, as well as listed in each node’s description. Each relationship is accompanied by a detailed description and a confidence level (low, medium, high), based on our assessment of the source’s overall reliability or relevance.
The data for these nodes and relationships come from a broad analysis of publicly available academic publications, open-source intelligence (OSINT), and CTI literature on the Chinese cyber ecosystem. This project is the result of more than 5 months of research, data collection and analysis. However, it is important to remember that the map will never be exhaustive, due to our limited visibility and to the very nature of this obscure threat ecosystem.
