CyberSOC, effective response model for cyber threats


Gavin Xie
Solution Architect, Orange Cyberdefense China
For cybersecurity personnel, SOC (security operations center) is a familiar term. However, people may not be so familiar with what CyberSOC is. Today we will decode CyberSOC so that everyone can better understand the latest progress in cybersecurity operations.
In the past few years, enterprises have mainly relied on security products and technical components, including firewalls, WAFs, SIEMs, etc., to build SOCs to identify and prevent network threats and provide protection for enterprises' digital assets. The SOC manages security from a "technical perspective." Typically, the SOC is staffed with security product experts and provides services such as release management, configuration management, and signature updates. With the emergence of new cyber threats such as Advanced Persistent Threats (APT) and ransomware, enterprises have found that technology-led security methods alone are no longer enough to deal with the evolving cyber threats. To address the challenges in the new cyber threat landscape, enterprises need to adopt a new cybersecurity operations framework and model called Cybersecurity Operations Center (Cybersecurity Operations Center), or CyberSOC for short. It is also called an advanced SOC and involves leveraging the most advanced Threat detection and analysis technology and cyber security operation methodologies to enhance and upgrade the traditional SOC framework.
What is CyberSOC?
CyberSOC is a department responsible for centrally handling security issues at the organizational and technical levels. It consists of a team of cybersecurity experts who work together. The mission of CyberSOC is to identify, analyze, prevent, and respond to cyber threats faced by organizations. These tasks include protecting assets from threats such as hackers, ransomware, distributed denial-of-service (DDoS) attacks, and advanced persistent threats (APTs). CyberSOC provides end-to-end solutions to protect an organization's digital assets. They provide real-time threat detection and analysis and help reduce losses by providing fast and effective responses.
Not all CyberSOCs are the same, they depend on the specific requirements and architecture of the organization. However, they usually have the following characteristics:
• Threat Intelligence: The main purpose of CyberSOC is to protect organizations from cyber threats. To do this effectively, it needs to stay up to date on the latest cyberattack tactics, techniques, and procedures (TTPs) used by cybercriminals.
• Risk identification: CyberSOC identifies potential risks through regular security assessments of assets and develops targeted security strategies to mitigate and eliminate risks.
• Threat Monitoring: Continuous monitoring of an organization’s network is critical to detect and prevent any potential threats.
• Incident response: CyberSOC must respond quickly and effectively to any breach or threat. This involves identifying the cause and scope of a security incident and implementing mitigation strategies.
From the characteristics of CyberSOC, we can find that a mature CyberSOC must have accurate and comprehensive threat intelligence, efficient and continuously optimized threat detection capabilities. These capabilities cannot be provided and generated only from the product and technology perspective and need to utilize security incident analysts. Including personnel skills to provide services such as alert triage, risk analysis, incident handling and business impact assessment, thereby extending and enhancing the functions and capabilities of traditional SOC. The successful operation of CyberSOC thus relies heavily on the teamwork of skilled professionals. As shown below, these professionals include:
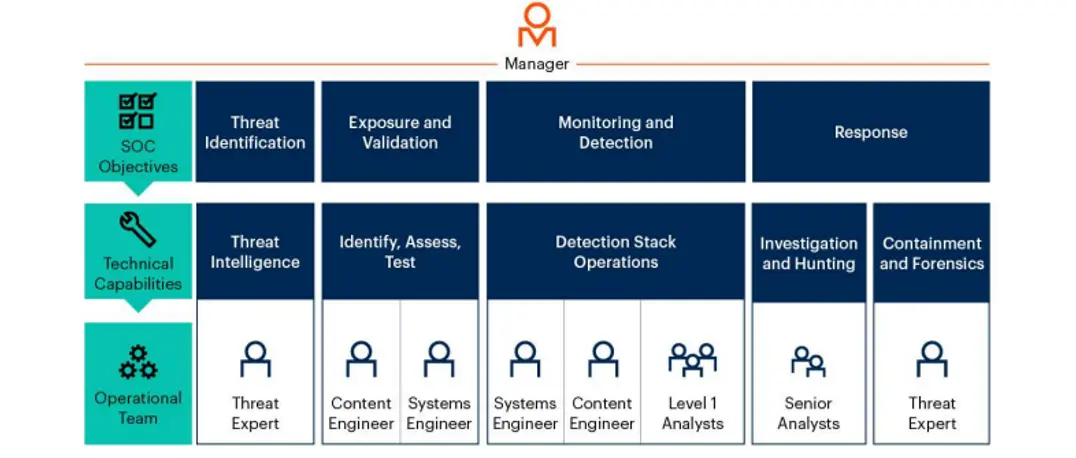
• SOC Manager: Oversees day-to-day operations and manages team members.
• Security Analysts: Tier 1 security analysts are responsible for threat detection, and senior security analysts use advanced analysis tools to conduct in-depth investigations of threats and are responsible for security incident response and threat hunting.
• Security Engineer: Including detection/content engineers and system engineers, responsible for digital asset risk assessment, maintenance of SIEM platform and development of threat detection rules.
• Threat Expert: Responsible for the analysis and verification of threat intelligence, serving as a digital detective to investigate the cause and impact of vulnerabilities.
How to build and operate CyberSOC?
While a modern CyberSOC is critical to an enterprise's cybersecurity operations, building and operating a CyberSOC is no simple matter. There are the following challenges in terms of technology, personnel and process:
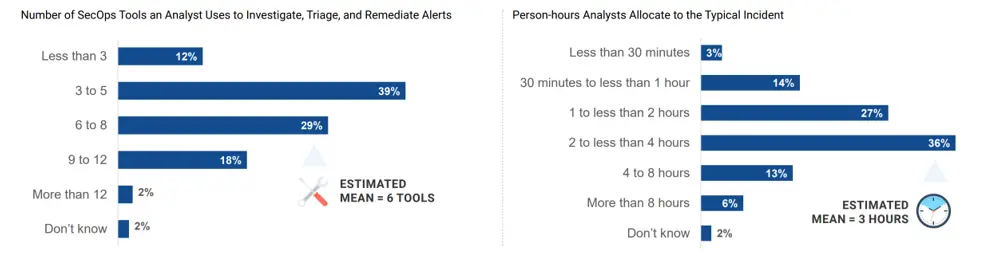
• Technology: Threat detection and analysis today requires many tools and a lot of time. According to the ENTERPRISE STRATEGY GROUP survey report, security analysts need to use an average of 6 tools and spend 3 hours to conduct an investigation and analysis of typical security incidents.
• People: In the SOC Market Trends Report, 89% of respondents' organizations are affected by a shortage of cybersecurity skills. The most in-demand skills include data science, collaboration, communication and knowledge sharing within security operations teams.

• Process: In the SOC Market Trends Report, 94% of respondents' organizations face one or more of the following security operations process challenges.

For these reasons, relying solely on an organization's own team to build and operate a CyberSOC is a costly and slow-to-pay-off investment. Based on the organization's business needs and security strategy, purchase appropriate security services from external vendors such as managed threat detection and response, risk exposure management, data forensics, security incident response, etc., and implement them to fully adapt to the organization's existing security team capabilities. The hybrid security operation model is the best option to build the organization's network security operation capabilities effectively and efficiently.
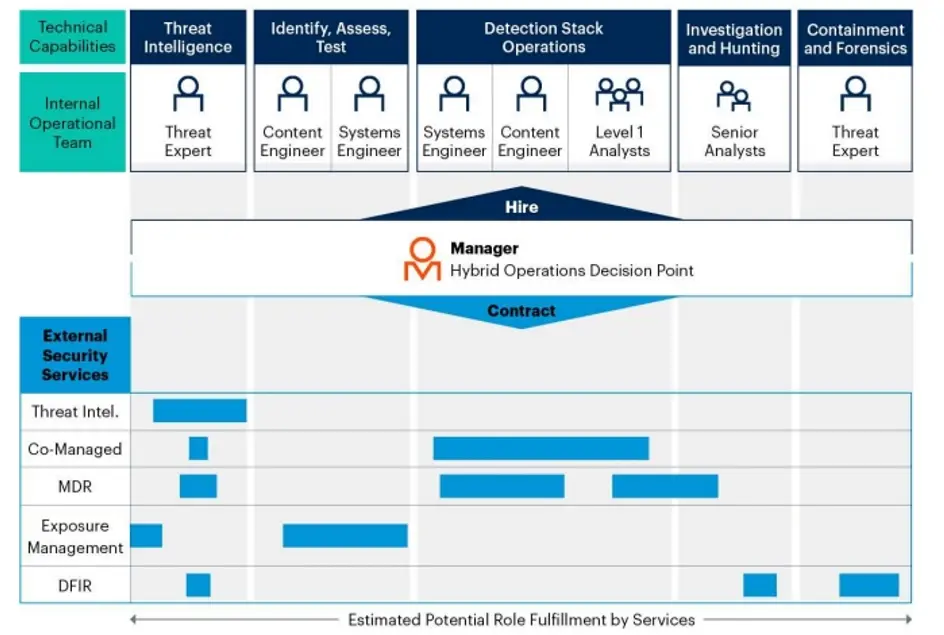
Orange Cyberdefense has rich experience and a large number of successful cases in helping customers effectively and efficiently build CyberSOC and continuously optimize cybersecurity operation capabilities through managed threat detection response, risk exposure management, and other security services. Please reach us by email or phone if you want to know more about our cybersecurity services and solutions.
