How to find the right balance between prevention, detection, and response
When it comes to counter threats, like all things in life, it is a question of balance. Here is our advice.
A shift in the cybercrime industry
Around 15 years ago, the adversary motives started to shift from fame and curiosity (for example Love Letter, Nimda) to move more towards a criminal business model and ecosystem. This caused a tactical change. Cybercriminals needed to stay under the radar.
And in the past decade breaches have accelerated. By just looking back 5 years, we could read about major breaches once or twice per year. Today the pace is more or less once or twice per week…
There has been a shift and research in this area points in the direction that organized cybercrime revenue soon has exceeded crime revenue in the “real world”. According to cybersecurityventures.com, cybercrime costs have risen worldwide from $3 trillion in 2016 to $6 trillion this year. In 2025, it is expected to reach $10,5 trillion. The commoditization of ransomware 5-6 years back has further increased the “opportunity” to make money.
Ransomware has gone from being something that in most cases could be seen as collateral damage for the enterprise (as the target was not primarily the company but instead the individual) to much more of an enterprise-wide issue today. When it was individuals, restoration of systems and lost productivity was of course painful and somewhat costly but could in most cases be solved by restoring backups.
What we see today is a shift where the adversaries have a foothold for weeks, months, or sometimes even years in a customer environment before carrying out a coordinated ransomware attack across multiple systems, often the most critical ones. In some cases, even using the customer’s distribution tools to propagate the ransomware.
Part of this attack scheme is also that the adversaries are looking for (and often find) the intellectual property or the “crown jewels” in the customer environment. This data could later be sold or even be used as a second leverage point if the customer refuses to pay the initial ransom demand, meaning that even when the attackers are gone and have released the encrypted systems – are they ever really gone? Using ransomware at the end of the attack is also a way to cause chaos across the target business and an effort to cover the tracks of that data that has been stolen.
Prevention as a first step
“Prevention is ideal, but detection is a must“, said Dr. Eric Cole, a well renowned SANS fellow and security consultant. Related to how breaches have become almost inevitable, this quote has become more relevant than ever. Indeed, when an adversary passes through your defenses it may not lead to a disaster if you can discover it promptly.
An extension of the quote is also: “detection without response has minimal value”, meaning that detecting without understanding what you see or having the ability to respond properly could also be the difference between damage and disaster.
Prevention investments are not enough
Historically, cybersecurity has been focused so much on prevention. Today, that is where the most investments still are. However, investing only in this area becomes irrelevant with time.
In the beginning, the security level increases. But it flattens out over time because of the lack of investment in the abilities to detect and respond to the threats that could not be prevented. Get more out of your security budget, balancing out the scale with detection and response.
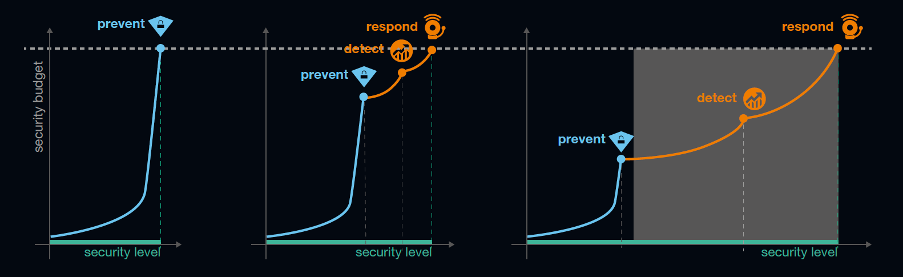
Source: Orange Cyberdefense
As we’ve seen, prevention is important, but not enough. There is more than ever a need for detection capabilities to be able to see what passes through defenses.
The SOC-triad
In 2015, Anton Chuvakin, who was, at the time, an analyst at Gartner, came up with the SOC-triad concept. The SOC-triad is built around the idea that a SOC should have the following main pillars for the best possible visibility coverage:
Ideally, any company should have all of the above even if, of course, each detection pillar has its strengths and weaknesses.
In our experience, the quickest way to get visibility of your environment is to start with the endpoints. The endpoint is central for an attacker and is often the focal point of an attack. It is the place where you can pick up the most comprehensive information about how an attacker is operating. And so when it comes to getting visibility fast, a good Endpoint Detection and Response (EDR) agent has the least dependencies on the end-user organization to provide the broadest coverage of breach detection.
Like most cases in cybersecurity though, it is not only a technology choice but also equally important to have the right skills and processes to be able to understand the visibility given by the technology.
Endpoints and prevention
Always strive for the best possible prevention, the more effective it is, the more you will filter out through prevention systems, and the less there will be to analyze which passes through in the detection end.
For instance, many of the major enterprise breaches have affected companies that have invested a lot in security teams (including people and processes), and they have had detection technology and there have been alerts generated indicating the breach. But the people, process, and technology have not been aligned causing floods of alerts which makes it hard for analysts to find the breach needle/s in the haystack of alerts.
Processes should be repeatable (and automated wherever possible), consistent and most of all, should be understood and regularly practiced by those tasked to deliver them. When it comes to detecting and responding to threats – like anything – practice makes perfect.
Endpoints and detection
Without detection capabilities, you will have no ability to see what is passing through your defenses. And the absolute best possible point to see everything is on the endpoint as you will be able to monitor processes, memory, users, traffic (before it’s encrypted), etc.
There are a lot of technologies out there that have the capabilities to collect telemetry data from endpoints but the key point from a technology perspective is how the collected data points are being processed in the next step. Having a technology that is built to aid the analysts to find the breach “needles in haystacks”, connecting the dots into a timeline, will save a lot of time and effort in the analysis phase.
The only drawback is that you cannot install a sensor or agent on all devices in your network, hence the SOC-triad makes for more complete visibility and coverage in the longer term.
So whilst the endpoint is often a good place to start, you must also have an eye on the future. How will you build a detection strategy? What established frameworks will you use to help guide that strategy? And how will you deliver once you have that visibility?
These are all questions Orange Cyberdefense helps its customers to answer – either through guidance and a consultative partnership or more often than not, to also be involved in delivering on this strategy and extending the teams of our customers through Managed Detection and Response services.
Detection without response has little value
Time to detect is crucial. But time to provide an appropriate response to limit the damage of a breach is also important.
Response could be anything from isolating affected endpoints, resetting user passwords to starting a more thorough incident investigation. But also, more process-related tasks like when to escalate an incident to management, how to communicate with external parties (such as law enforcement, media, etc.), and how to handle different types of cybersecurity incidents (a phishing incident will likely be handled very different to a DDoS attack for example).
The key point is that you need to know your response capabilities and also how to use them even if your IT systems are down; for the latter do you have contact details for key stakeholders only in a digital format or also printed? This also touches on the importance of a BCP (Business Continuity Plan), but that is a subject for another post.
Conclusions
In today’s threat landscape, detection and response capabilities are a must. It is also crucial that this follows the endpoint as much as possible regardless of where they are (on/off-premise). This is driven even more in these COVID-19 affected times where the remote workforce has vastly increased causing a lot of challenges to control and manage endpoints.
Reach out to us if you want to discuss the detect and respond aspect of your security strategy further.
