
Looking at cyber extortion (Cy-X) data in Q2 2023

Author: Diana Selck-Paulsson
Summary
- We recorded 1,000 businesses being victimized on cyber extortion leak sites
- Q2 has seen an increase of 26% in victims.
- H1 2023 has seen an increase of 57% in comparison to H1 in 2022.
- Over 188 victims became victim because of the MOVEit vulnerability exploited by Cl0p
- The top 5 cyber extortion groups contributing to the Q2 2023 victims were: LockBit3 (24%), ALPHV (aka BlackCat) (12%), Cl0p (9%), BianLian (8%), Play (7%), and Others (40%)
- English speaking countries in top 3 (US, GB, CA) followed by Germany, France & Italy
General Trends
While we reported Q1 2023 to be the quarter with the highest recorded victims, Q2 has seen even more. We have registered 1,000 organizations that have fallen victim to cyber extortion (Cy-X) between April and June 2023. One explanation for this is that Q2 has seen the most active amount of threat actor groups / leaksites. One year ago, Q2 2022 saw 23 different leaksites actively naming and shaming victims on their darkweb blogs. In Q2 2023, we saw a 52% increase of leaksites posting victim organizations. Hence, it makes sense that when we see an increase of actors, we also register an increase in victim count.
We then would like to explore the question whether the ecosystem has been growing substantially or if certain groups operate several variants or extortion operations in parallel and thus make the ecosystem seem bigger than it actually is (as we have argued previously). For this we turn to our ransomware map maintained by Orange Cyberdefense’s CERT team, which can be found here. By mapping the leaksites that we call ‘Distinct Count of actor’ in the figure above to the ‘Ransomware operations’ of the Ransomware map, we find that the majority of actors in this field don't seem to operate several leaksites/ operations in parallel. In fact, we are only able to identify 3 operations that are most likely connected to the same threat group that operate 2 leaksites. However, there are two things that are important to bear in mind. First of all, attribution is always difficult. And secondly, for the majority of leaksites/ Ransomware operations/distinct actors that actively named and shamed victim organizations in Q2, we were unable to find a connection to any threat group (see below). This is especially the fact for this year since we added much more new leaksites / operations to our tracking than we have ever before. In fact, we see a lot of movement in this criminal ecosystem right now. While we monitored about 40 unique leaksites in 2022, we have already registered 36 new sites in 2023, and we are only half way through. Most likely, time will show how sophisticated these new operation are and how much we can learn about them.
Another trend that has shown its face in 2023 and made an appearance in Q2 again is the exploitation of 0-day vulnerabilities. While in Q1 2023, Cl0p exploited the GoAnywhere vulnerability and claiming over 130 victims through that; in Q2 they repeated their modus operandi exploiting the MOVEit vulnerability. This time, Cl0p made a general post on their leaksite, informing the public about the MOVEit vulnerability and asking the victim organizations to reach out to them to handle the data extortion incident. This is unusual, since threat actors normally leave ransom notes with instructions to get in contact with them. This time, most likely to the sheer volume of victims, they ask the organizations impacted by the MOVEit vulnerability to reach out to them, adding the deadline of the 14th of June.
At the time of writing, we observed 189 victims. Other reports state as many as 231[1] victims, but we cannot confirm the latter.
Threat actor activity
In Q2, we saw 35 different operations victimizing organizations around the world. Similar to Q1, the top 3 threat actor groups remain unchanged. LockBit3 caused ¼ of all victims in Q2, followed by ALPHV(BlackCat) with 12% and Cl0p causing 9% of all victims. As we mentioned above, Cl0p exploited a vulnerability (again), and thus started exposing victim organizations on their leaksite mid-June. However, of the 188 victims that we are connecting to the MOVEit vulnerability, 89 victims were posted in June, an additional 99 in July, up until the 18th of July/ the time of writing this blog post.
Of the 35 threat actors that we observed to have victimized organizations during Q2, 17 were operations that we discovered in 2023 and added to our tracking. This means that half of the cyber extortion operations are new, or began new under a new brand. The other 18 were operations that we have been tracking already, some from 2021, others from 2022.
Victimology of Q2 2023
We observed a small shift in industry distribution, however the top 2 industries impacted by Cy-X remain the same. 1/5 of all victims were from the Manufacturing sector, and Professional Services.
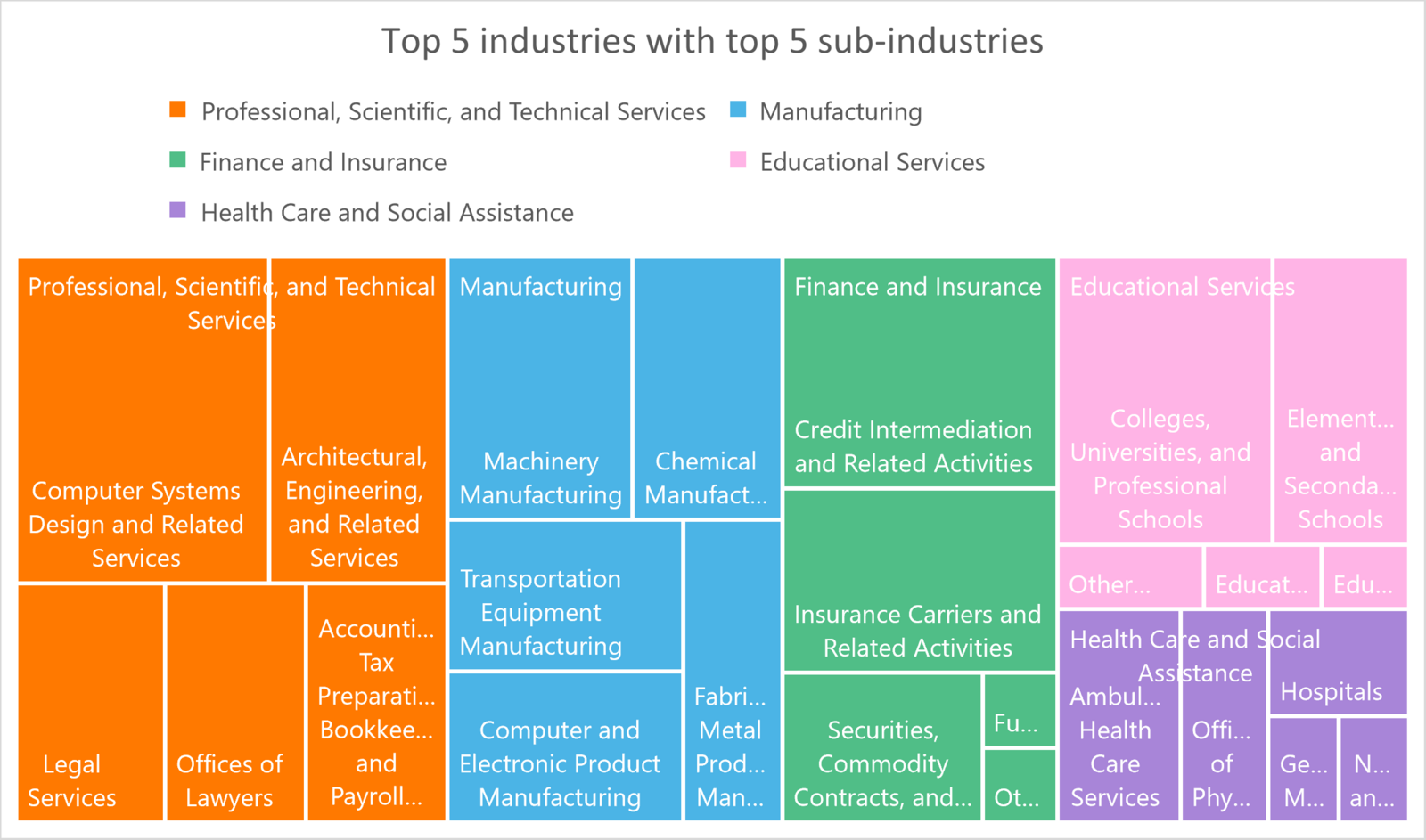
An interesting observation is that the Financial Sector has seen an increase in victims. This can partly be explained by the Cl0p event that has caused around 1/3 of the victims from this sector. When diving into the question who from the Finance sector has been impacted the most, we find that Banks were impacted the most, followed by Insurance Carriers and other financial-related services. Education and Healthcare have also been much more impacted in Q2 than before. Here we observe colleges, universities and schools in general being hit. Within the healthcare sector, we register most victims from the ambulatory and healthcare service or offices of physicians or hospitals. Despite the fact that several threat actors claim to not extort the healthcare sector, and especially hospitals; we see a contradictory trend. In Q2, we observed 8 hospitals in our victim dataset.
For Professional Services, we noticed that many victims were somehow related to offering digital services. Here we saw the majority of organizations working, creating or offering some sort of software solutions or other technical services. Another theme within Professional Services is the legal services part, those can be law firms or other businesses offering legal services.
If we then only focus on the frequencies of the top 10 sub-industries that were impacted in Q2 by Cy-X, we find that some of them inherit important functions of today’s society. We observed organizations offering software-related products, banks, colleges & universities, computing infrastructure providers, data processing & web hosting and manufacturing in sub-areas such as computer and electronic products, chemical manufacturing (e.g. pharmacy, cosmetics, etc.) and transportation equipment.
And lastly, we found that English-speaking countries saw an increase again in our victim dataset. Almost half of all businesses that suffered from cyber extortion were headquartered in the U.S. (48%), followed by the U.K. (6%) and Canada (5%). Within the top 10, we also registered Europe to be notable, in particular Germany (top 4), France (top 5), Italy (top 6) and Spain (top 10). Besides English-speaking countries and the European countries, we saw Australia (top 7), India (top 8) and Brazil (top 9) represented in our top 10 list. We also observe that the Nordics (even though in small numbers) saw an increase, especially Sweden has seen as many victims in H1 2023 as we registered in all 2022.
Conclusion
We have shown that cyber extortion has significantly grown (again) since the beginning of 2023, but specifically in Q2. The 8% decrease that was observed in 2022 will unfortunately not be a continuous trend. While we observed around 2,100 businesses being victimized in 2022; we have reached already 1,793 victims in the first half of 2023!
Consequently, we do not believe the victim numbers will decrease nor that the threat of cyber extortion is going away anytime soon.
However, there are two things we believe are happening at this moment, or will happen in the near future. Those two observations are made by someone else but we would absolutely agree with them based on the experience we have gained by observing this form of crime for a few years now.
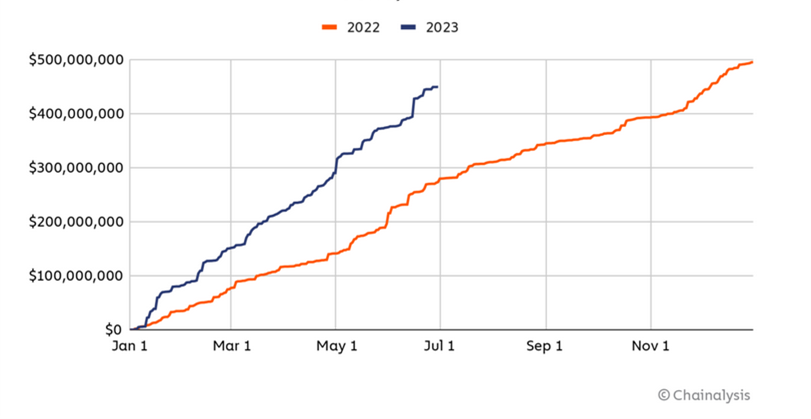
First of all, Chainalysis who just published their mid-year report[2] highlights that ransom payments have unfortunately grown significantly (see below). In H1 2023, the cumulative ransomware revenue has almost reached already the level of all 2022. This sounds very familiar to what we also just realized. Victim numbers are close to the point of the whole last year, ransom revenue follows this trend. This means, we are seeing high volumes this year. High volumes of activity, more threat actors contributing to cyber extortion, many new ‘players’ causing higher volumes of victims. The question remains whether or not the likelihood to pay has increased in the first half of 2023 or if the quantity of victimization makes up for the higher ransom revenue Chainalysis found.
The report explains further that they see that both very small payments and very large payments increased in 2023. For example, in 2023 the ransomware variant Cl0p has had an average payment size of $1,730,486; while other variants such as Dharma only made an average of $265. So again, they see this trend for low and high payments.
The second observation that we also believe is going to happen in the next two months is that we expect threat actors to take vacations. Especially in 2020 and 2021, we saw usually a calmer summer period while by the end of Q3 and all Q4 we registered high volumes of activity. This trend wasn’t continued in 2022, and we believe the war might have ‘interrupted’ the ecosystem in 2022, causing this anomaly.
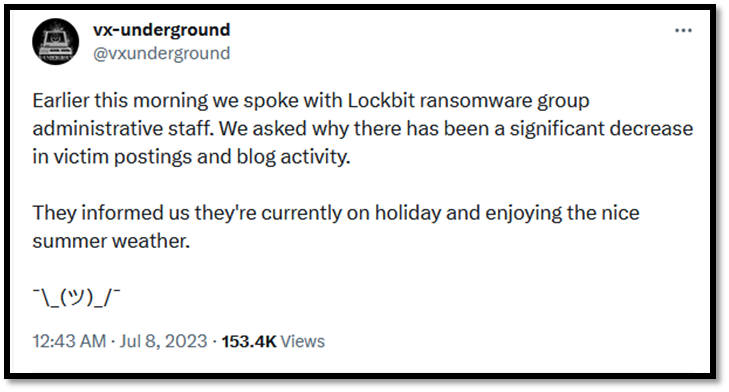
Like our expectations, we saw a recent tweet from vx-underground[3] asking the LockBit3 group exactly that. According to the tweet, LockBit3 confirms to have taken a summer break (see screenshot).


