
8 July 2024


Thulani Mabuza
Team Lead-Technical Pre-Sales
Insider threats remain one of the most complex challenges in cybersecurity. Unlike external attackers, insiders already have legitimate access to systems, making them harder to detect and potentially more damaging (Ambre & Shekokar, 2015). Organizations suffer financial, reputational, and operational losses annually due to these threats, yet many still rely heavily on traditional security solutions that focus only on technological defenses. To truly mitigate insider threats, organizations must adopt a holistic approach that integrates People, Process, and Technology - a framework that aligns perfectly with Socio-Technical Systems (STS) Theory which provides a coverage of four factors namely: Culture, Structures, Methods and Machines (McEvoy & Kowalski., 2019).
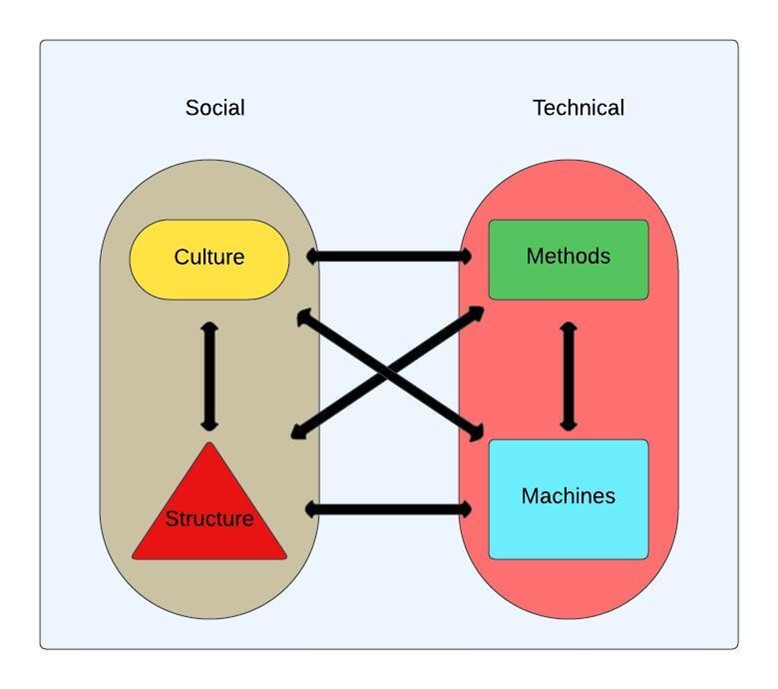
The STS Theory recognizes that security is not just about implementing the right technology, it is about how people interact with systems, how processes govern their behavior, and how technology supports these interactions. Mapping insider threat mitigation strategies to People, Process, and Technology, organizations can create a comprehensive defense model that is proactive rather than reactive.
Organizations today confront a myriad of challenges in identifying and mitigating insider threats. One significant hurdle is the difficulty in detection. Insiders, by virtue of their authorized access, can operate under the radar, making malicious activities hard to distinguish from regular workflows. This challenge is compounded by the sheer volume of data and the complexity of modern IT environments, which can obscure potential red flags.
Another pressing issue is the lack of technical expertise within organizations. Many firms struggle to effectively implement and manage insider threat solutions due to insufficient specialized knowledge. This gap can hinder their ability to identify and protect against threats, leaving them vulnerable to internal risks. A recent study highlighted that 39% of respondents cited technical difficulties in implementing insider threat management tools, often due to a lack of staff expertise (Gurucul: The Challenges of Detecting and Mitigating Insider Threats).
The evolving nature of the workplace also presents challenges. The rise of remote work and the use of personal devices for professional tasks have expanded the potential attack surface. This shift complicates the enforcement of security policies and increases the risk of inadvertent data leaks or unauthorized access.
What we have seen is that organizations often grapple with the balance between trust and control. Implementing stringent monitoring measures can lead to concerns over employee privacy and may foster a culture of mistrust. Striking the right balance is crucial to ensure security without compromising employee morale or violating privacy rights.
The impact of insider threats on organizations is profound and well-documented. Insider threats account for about 60% of data breaches, a proportion that has been increasing. Since 2018, insider security incident prevalence has increased by 47%, and the average cost of an insider threat has surged by 31% (Isaca: Why So Many Organizations Underestimate Insider Threats).
In 2024, a report revealed that 83% of organizations experienced at least one insider attack within the year. Notably, organizations that faced between 11 to 20 insider attacks saw a fivefold increase compared to 2023, underscoring the escalating nature of this threat (SecurityIntelligence: 83% of organizations reported insider attacks in 2024).
The Security Navigator 2025 CyberSOC data also show that 'Internal' actors now account for 47% of all incidents, up from 37% as show in the previous Security Navigator. All incidents with actions classified as 'Misuse' represents 29% and those associated with Internal actors account for 25.4%. Similarly, incidents with actions classified as 'Error' represents 8% of all incidents and 6.59% are associated with 'Internal' actors.
These statistics highlight the critical need for organizations to develop comprehensive strategies that address both the human and technological facets of insider threats. This starts with understanding the current challenges and acknowledging the significant impact of insider-related breaches, organizations need to better prepare and implement effective mitigation measures.
People are at the core of insider threats, whether due to malicious intent, negligence, or manipulation by external actors. Employees, contractors, and even trusted third parties can introduce risks if security is not deeply ingrained in the organizational culture. STS Theory emphasizes that security measures should be designed with a human-centric approach, considering user behavior, motivations, and potential stressors that could lead to insider threats.
A security-conscious culture begins with awareness and education. Employees must understand the risks associated with mishandling data, falling for social engineering attacks, or bypassing security protocols for convenience. Regular training sessions, clear guidelines on data access, and fostering a culture of accountability can significantly reduce the likelihood of unintentional breaches. Moreover, organizations must pay attention to employee dissatisfaction and behavioral red flags that may indicate a potential insider threat. Providing support systems, open communication channels, and ethical ways to report concerns can prevent internal frustrations from escalating into security incidents.
The process pillar ensures that security policies and procedures are well-defined, enforced, and continuously improved. STS Theory stresses that security cannot be an afterthought, it must be embedded into daily operations, ensuring that human interactions with systems follow strict guidelines that prevent misuse.
One of the most effective processes in mitigating insider threats is Identity and Access Management (IAM). Implementing role-based access controls and the principle of least privilege, organizations can limit employees’ access to only what they need for their job functions. Regular access reviews ensure that outdated privileges are revoked, reducing the risk of insider exploitation.
Monitoring and behavioral analysis are also essential components of process-driven security. Insider threats often go undetected because insiders do not trigger traditional security alerts. Organizations should employ User and Entity Behavior Analytics (UEBA) to detect unusual activity, such as unauthorized access attempts, large data transfers, or login activity from unexpected locations. Establishing incident response plans specifically tailored for insider threats ensures that security teams can act swiftly and contain risks before they escalate.
While people and processes form the foundation of insider threat mitigation, technology provides the tools to enforce security policies, detect anomalies, and prevent unauthorized activities. However, STS Theory reminds us that technology alone cannot solve insider threats it must be integrated seamlessly with human behavior and operational processes to be effective.
A key technological safeguard is Zero Trust Architecture (ZTA), which operates on the principle of "never trust, always verify." Every user, whether internal or external, must continuously authenticate their identity and permissions before accessing sensitive data. Multi-Factor Authentication (MFA), encryption, and network segmentation ensure that even if an insider’s credentials are compromised, the attacker’s access remains limited.
Security Information and Event Management (SIEM) systems, combined with advanced threat intelligence, enable organizations to correlate security events in real-time and detect patterns indicative of insider threats. Cloud access security brokers (CASBs) further enhance visibility into cloud-based applications, ensuring that employees are not exposing sensitive data through unauthorized file sharing or data transfers.
Organizations must also secure endpoints, especially with the rise of remote work and bring-your-own-device (BYOD) policies. Mobile Device Management (MDM) solutions ensure that corporate data remains protected even when accessed from personal devices, while endpoint detection and response (EDR) tools provide continuous monitoring for suspicious activities.
Understanding the impact of insider threats requires more than just theoretical analysis - it demands real-world simulation. Our Security Analysts continuously perform Security Assessments that simulate insider threats in order to provide organizations with a proactive approach to identifying vulnerabilities and strengthening security controls before an insider can exploit them. Mimicking potential insider attack scenarios, these assessments offer valuable insights into how threats can manifest and what measures are needed to prevent them.
During these simulations, we assess how an insider with legitimate access - whether a disgruntled employee, negligent user, or compromised individual - could manipulate internal systems, exfiltrate sensitive data, or escalate privileges beyond their intended permissions. This allows us to measure the potential damage such an attack could cause, from unauthorized access to business-critical information to complete system compromise.
Our assessments evaluate the effectiveness of existing security controls, including access management policies, monitoring capabilities, and response mechanisms. Weaknesses that could be leveraged by an insider - such as excessive privileges, lack of logging, or inadequate segregation of duties are highlighted, ensuring organizations can address them before they lead to a real incident.
Most importantly, these security assessments provide clear, actionable recommendations for mitigating insider risks. This includes strengthening access controls, refining incident response plans, and improving organizational awareness of insider threats. Leveraging these insights, organizations can proactively fortify their defenses, minimize potential damage, and build a security strategy that effectively counters insider threats.
Insider threats demand a multi-layered security approach that goes beyond traditional perimeter defenses. Applying Socio-Technical Systems (STS) Theory to the People, Process, and Technology framework, organizations can develop a security strategy that is both comprehensive and adaptive. People must be educated and empowered to recognize and report risks, processes must enforce security at every level of operation, and technology must provide the necessary safeguards without disrupting productivity.
The key takeaway is that security is a shared responsibility. Organizations that balance technical safeguards with user behavior and organizational culture will not only reduce the likelihood of insider threats but also strengthen their overall cybersecurity resilience in an era of ever-evolving risks.
Security assessments tailored around the impact of insider threats should form part of the requirements by organizations to assess their resilience.
Ambre, A., & Shekokar, N. (2015). Insider threat detection using log analysis and event correlation. Procedia Computer Science, 45, 436-445.
McEvoy, T. R., & Kowalski, S. J. (2019). Deriving cyber security risks from human and organizational factors–a socio-technical approach. Complex Systems Informatics and Modeling Quarterly, (18), 47-64.
Isaca: Why So Many Organizations Underestimate Insider Threats
Gurucul: The Challenges of Detecting and Mitigating Insider Threats
SecurityIntelligence: 83% of organizations reported insider attacks in 2024
Orange Cyberdefense: Security Navigator 2025