
3 June 2024

Preamble: our series of articles is mainly dedicated to multiplayer games played online.
A “cheat” is a technique that offers the possibility to bypass the rules of a video game, allowing the player to:
On online multiplayer video games, cheats can alter the experience of other participants. As a result, some video games editors are particularly harsh on cheaters, sometimes going so far as to ban them from the game for life.
Easy Anti Cheat (EAC) is an American company specialized in detecting and protecting against cheating mechanisms in online multiplayer video games. In 2016, two of its members, Simon Allaeys and Aarni Rautava, presented their analytical work at the Steam Dev Days conference. See their presentation here.
According to EAC, cheats are mostly created by hackers (the word “hacker” here refers to a person with the ability to understand and take control of a computer system, without criminal intent). Since a video game is nothing more than a software, cheat mechanisms are actually modifications of the code that allow the gamer to bypass the rules set by its publisher.
EAC has identified three predominant hacker profiles. First, the “scripters”, who according to EAC, represent the majority of cheat creators. “They more or less copy and paste whatever they can find, experiment a lot and create relatively simple hacks,” Allaeys explains. Then there are the “senior hackers” who “are more experienced and more professional. They create cheats and features that they can sell. They are very often excellent programmers or reverse-engineering professionals. The last category is the one of the “researchers”, who are, according to S. Allaeys, more interested in the challenge than in actually cheating. They produce proofs of concept and have no selling objectives.
Many reseller websites offer monthly subscriptions, much like Netflix or Spotify, to sell the cheats to the gamers.
“If cheaters have been so numerous and well-equipped for almost twenty years, it is primarily because it is very easy to find cheats on the Internet. A well-formulated Google query triggers an avalanche of results with clear URLs: Iwantcheats.net, Unknowncheats.net, Artificialaiming.net, Exocheats.net, Privatecheatz.com…,” writes Sébastien Wesolowki, a journalist for Vice France, specialized in video games.
The article goes on to say: “Most of these sites can be classified in two categories: platforms reserved for sales and forums with or without a commercial dimension. Some are barely two years old, others opened in 2000.
The idea of our article is neither to analyze the technical efficiency of cheats, nor to make a judgement on the players who use them. Our goal is to inform them. Because if cheats are created by hackers and inspired by hacking techniques, that implies that some of the creators and/or sellers may have other purposes than to allow players to be efficient…
Orange Cyberdefense’s Epidemiology Laboratory tracks undetected malware. Here is a recent example of what they found. Hackers have created a fake mirror site copying the page of an “official” service specializing in the distribution of paid cheats for various known multiplayer games:
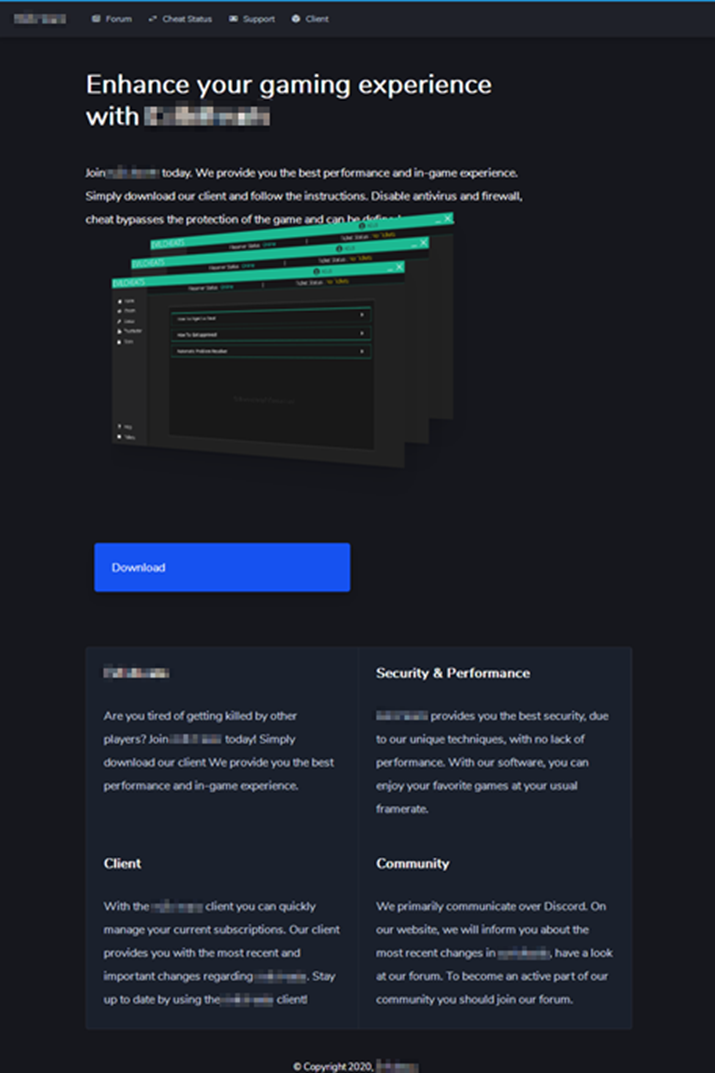
Figure 1: Copy of a cheating service, Orange Cyberdefense
The cheat site proposed here is actually a fake one. The software is not the “official” used by the real cheat service but a “stealer” type malware. It steals the player’s data to send them to cybercriminals, as shown in this second screenshot.
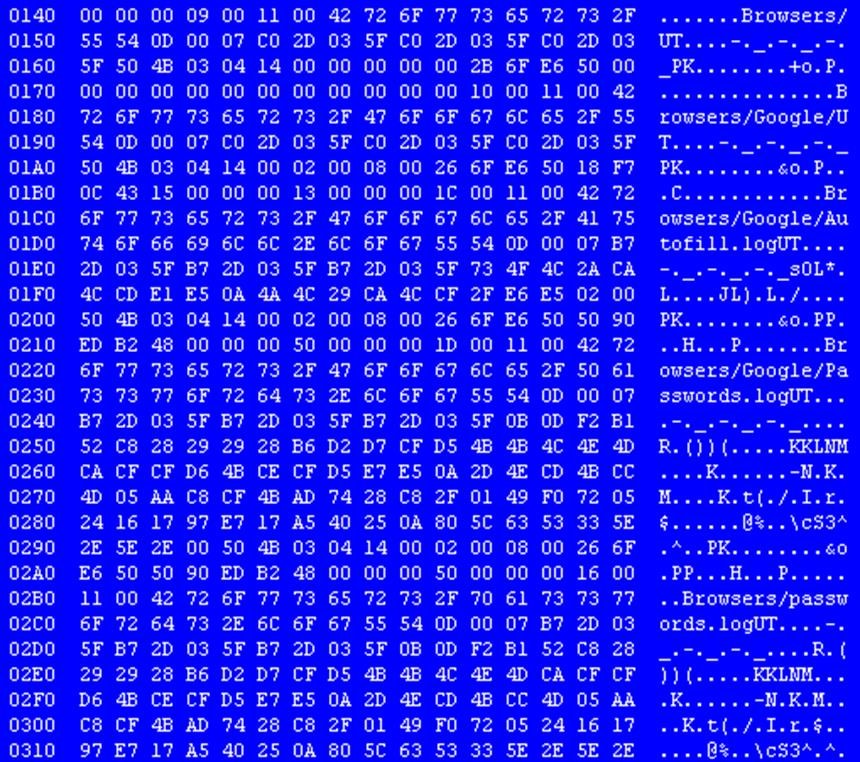
Figure 2: “stealer” type malware exfiltering browser data, Orange Cyberdefense
This site is just one example among many… The risks for players using cheats are above all to have their personal data stolen, sold or used for malicious purposes. In our first article, we insisted on the fact that, according to Avast, 55% of players reuse their passwords from one site to another. A practice that thus constitutes a real danger in this particular case, especially if they are used for a mailbox or a bank account for example.
The most obvious advice would be not to use cheats. That being said, if it seems mandatory to win, for one reason or another, here are the good practices to apply:
Note that these actions do not, in any way, prevent a malware attack, but can only, in some cases, “limit the damages”. The best thing, in terms of cybersecurity, is not to take this kind of risk…