
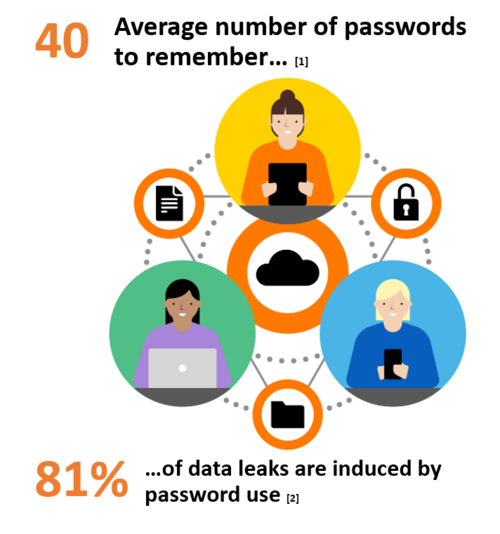
Why are passwords still a security risk?
Nowadays, passwords appear to be more of a risk than an actual protection layer for the user. Passwords represent the key to secure all digital operations, yet have become a huge issue for users who have too many to manage, which often are lost or leaked. Indirectly, this complicates the work of the CISO, which must enhance secure access, strengthen security and simplify the life of users.
The challenge is now to own security solutions that allow users to protect the company’s data in the easiest possible way. Passwordless multi-factor authentication (MFA) combined with single-sign-on improves the security and reduces dramatically the risk.
[1] Cycloide report, 2018
[2] Helpnetsecurity, 2020
Enhance your organization’s security posture with best-of-breed authentication and adaptive access control

Address your business requirements
- CISO: enhance dramatically your security posture and overcome the weakness of passwords while complying with regulation and zero-trust framework
- CIO: reduce the helpdesk cost with a centralized administration, modern and easy to use solution and smart rules to automate the burden of daily tasks
- Business staff: improve the productivity by being able to provide easy and simple access to hundreds of applications including SaaS and VPNs
- Users: ensure frictionless access with a wide range of solutions to fit all needs, such as push authentication on mobile devices with a single tap of a fingerprint on mobile device to authenticate
Build your new identity perimeter
Access Management as a foundation of your Zero Trust journey
Ease of access
Hybrid environment support, single-sign-on (SSO), single pane of glass for user management
Risk reduction
Granular access control with context based authentication (Zero Trust), wide range of step-up second factor
Scalability and agility
Fast deployment with full cloud-based architecture, easy migration from former strong authentication solutions
Compliance
Access traceability and compliance reports in line with your Cloud migration requirements
Flexible Identity Authentication - to the point
Want to protect your business from password theft?
Flexible Identity Authentication protects your resources with double authentication. To access them, your users generate a one-time password (OTP) using a PIN code and an authenticator: physical token, software, sms or grid.
Download datasheetTalking business: some related case studies


There is more to know about access management:




