

Managed Threat Intelligence [detect]
Boost your in-house SOC with Cyber Threat Intelligence
Organizations are increasingly at risk from Advanced Persistent Threats (APT). The challenge is to be able to detect and timely respond to these in a dynamic threat landscape.
Managed Threat Intelligence by Orange Cyberdefense can help you to improve detection of Advanced Persistent Threats (APT) by aggregating Threat Intelligence with an easy to consume and cost effective service.
Our proprietary Cyber Threat Intelligence (CTI) datalake consolidates over 500 public and private sources. The data is qualified and enriched by our experts, and ready to consume via our web application and API.
This helps your in-house SOC teams to fully benefit from an Intelligence-led security approach whilst avoiding the complexity of managing multiple sources, tooling or specialized teams.

Benefit from industry-leading Cyber Threat Intelligence
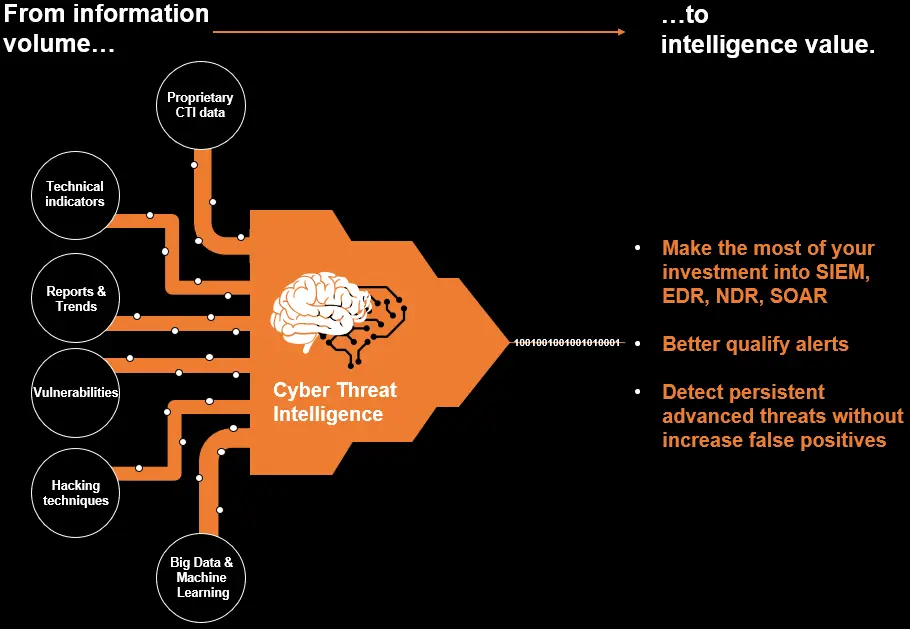
Our Threat Intelligence is available for security technology enrichment:
- Embedded in our threat detection and response services
- Stand-alone, for security technology enrichment via our Managed Threat Intelligence [Detect] service
Our Intelligence ready to consume:
- Orange data, already qualified and continuously updated
- 900 000 new threats per day
- Qualified sources from our CyberSOCs and CERTs, Vulnerability Operations center, Epidemiology Lab, Cybercrime unit, World Watch and our Security Research team
- Large sighting of CyberSOC analyst
- Easy to integrate with SIEM, SOAR, TIP
- Powerful API to forge your own feed
- SaaS portal for easy search
- CTI Partner feeds available
Obtain qualified and actionnable data about threats to better anticipate
Speed up qualification of incidents
Decrease incident response times by enriching your SOAR
Enhance your detection
Feed your SIEM with CTI data and be alerted of any new threats relative to a vulnerability with monitored search
Time & money saving
Achieve better ROI on existing technology and teams via a single CTI service
Easy to use
API swagger, web application and unlimited users
Our assets and unique capabilities
3 000 000
of CTI events per day leading to a million of new qualified threats per day
28
CyberSocs, Socs using our solution including 4 CERTs worldwide
Partnerships
with key tech vendors and agencies such as: Europol, First, TF-CSIRT or Phishing Initiative...
40+ experts
dedicated for R&D and threat research
>15 data types
ASN, Credit card, CVE, Cryptowallet, Domain, Email, File hash, FQDN, IP/IP_range, Pastie, Phone, Regkey, SSL certificate, URL, IBAN...
Deep dive into our datasheet:




